
The Role of Qubits in Quantum Cryptography: Beyond Classical Encryption
What Makes Quantum Cryptography Different?
Alright, let’s dive in. Imagine the world of encryption as a high-stakes poker game. In classical encryption, you’re hiding your cards, hoping no one figures out your hand.
But in quantum cryptography, your cards are more like phantom cards—if someone even tries to take a peek, the whole deck changes. That’s the magic of quantum mechanics—it plays by different rules, opening up new possibilities for data security.
At its core, quantum cryptography leverages qubits, quantum particles, and their wild, unpredictable nature to secure information in ways classical cryptography can only dream of.
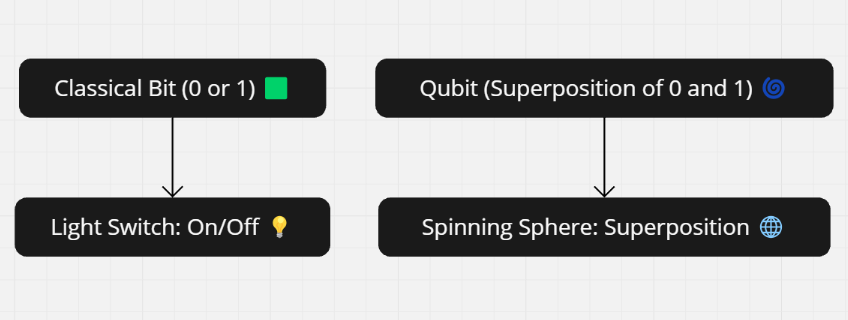
Side-by-side comparing a classical bit (0 or 1) with a qubit (able to be in superposition of 0 and 1)
The Rise of Quantum Computing: Breaking Classical Encryption
You’ve probably heard the buzz around quantum computers. They’re the new kids on the block, but these aren’t just faster versions of today’s computers—they’re a completely different breed. Thanks to quantum principles like superposition and entanglement, quantum computers can process information at a mind-boggling scale.
That sounds great, right? But here’s the kicker: Quantum computers are also dangerously good at cracking classical encryption methods like RSA and AES, the systems we rely on for keeping everything secure, from your online banking to state secrets. Scary, huh?
That’s where quantum cryptography comes to the rescue. It fights fire with fire by using quantum systems themselves to build unbreakable encryption.
Introducing the Qubit: A New Era of Data Security
So, what exactly is a qubit? If a classical bit is like a light switch, turning on (1) or off (0), a qubit is more like a dimmer switch. It can be in the on position, the off position—or somewhere in between, in what’s called a superposition. This ability to be both 0 and 1 at the same time is where the magic lies.
In encryption terms, this means that quantum cryptographic systems are fundamentally more complex and harder to break than binary systems. And because qubits exist in these quantum states, they bring a level of unpredictability that hackers can’t easily simulate.
How Qubits are Fundamentally Different from Classical Bits

Here’s the big deal: classical bits are reliable, predictable little guys. You flip them on, they stay on. Flip them off, same deal. But qubits? Oh, they’re a whole other story. Thanks to the quantum property of superposition, they can exist in multiple states until measured. And this isn’t just abstract theory—it directly affects the way we can encode and protect information.
When qubits are used in quantum cryptography, they can detect any interference. If an eavesdropper tries to intercept the data, the act of measuring the qubits disturbs them, which alerts the system. This essentially renders the man-in-the-middle attack obsolete.
Quantum Superposition: The Key to Cryptography’s Future
Let’s break down this idea of superposition a bit more. Imagine spinning a coin—it’s not heads or tails, but a blur of both until it lands. In quantum mechanics, a qubit is like that spinning coin, holding a probability of both 0 and 1. This is what gives quantum cryptography its edge over traditional systems.
For cryptography, superposition means that data can be encoded in such a way that it becomes almost impossible to crack using classical means. It opens up a whole new approach to how we generate keys and encrypt messages, offering a level of security far beyond classical encryption.
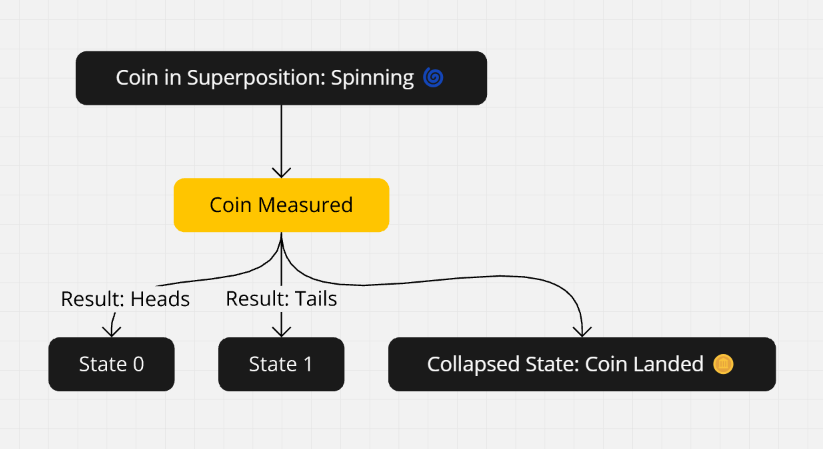
Showing a coin spinning in the air, symbolizing how a qubit can exist in both states (0 and 1) until measured. Add a before and after shot: one showing the coin spinning (superposition) and one where it lands (collapsed state).
Entanglement: The Unbreakable Bond in Quantum Security
Now, here’s where things get wild: quantum entanglement. This is like a deep cosmic connection between two qubits. Once entangled, no matter how far apart they are—whether on opposite sides of the room or on opposite sides of the universe—changing the state of one instantly affects the other.
This phenomenon forms the backbone of quantum cryptography. When two qubits are entangled, the information between them is perfectly synced and, more importantly, impossible to tamper with. If a hacker even tries to interfere, the entanglement is disrupted, and the system knows something’s up. Think of it like two safes that open only if both keys are turned at the exact same moment. No one can sneak in without you knowing.
Quantum Key Distribution (QKD): A Game-Changer in Encryption
So, how does all this quantum weirdness translate into actual encryption technology? Enter Quantum Key Distribution (QKD). This is the process of using qubits to securely share encryption keys between parties. Traditional methods rely on complex algorithms to exchange keys, but QKD takes it a step further by ensuring that any interception attempt changes the state of the qubits—alerting the users.
With QKD, it’s impossible for hackers to copy the key without detection, making it one of the most secure methods of key distribution ever developed. This makes it an ideal weapon in the fight against increasingly sophisticated cyberattacks.
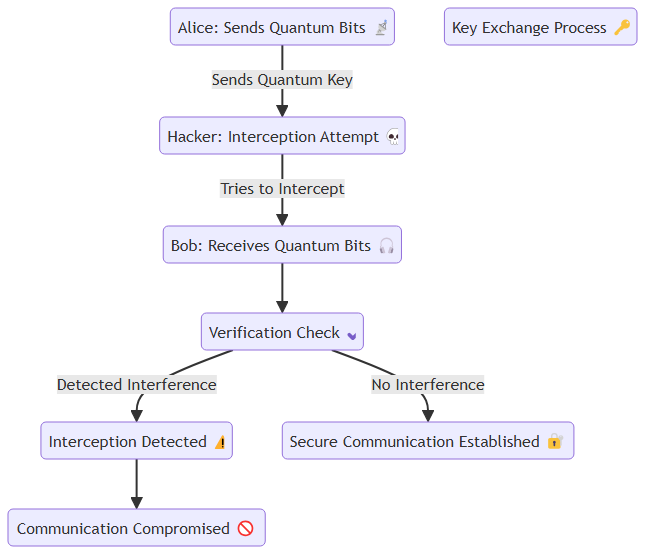
This would show two parties (commonly Alice and Bob in cryptographic contexts) exchanging quantum keys. Insert a “hacker” trying to intercept the key, which disrupts the system, thus alerting Alice and Bob that their communication is compromised.
The Role of Quantum Entropy in Unhackable Codes
Now, let’s talk about entropy. In classical cryptography, randomness is crucial for generating strong encryption keys. But quantum systems take randomness to the next level. Thanks to the inherent unpredictability of quantum mechanics, qubits can create genuinely random numbers—known as quantum entropy—that are far more secure than any algorithm-generated randomness.
The beauty of this is that the randomness of qubits can’t be reverse-engineered. In traditional encryption, a sufficiently powerful computer might eventually crack the code by guessing the random number sequence, but with quantum entropy, the odds of that happening are so astronomical it’s practically impossible.
Is Classical Encryption Obsolete?
You might be wondering, “Does this mean we’re ditching classical encryption?” Not quite. Quantum cryptography is powerful, but it’s not ready to replace every form of encryption just yet. Classical encryption still works well for many applications, and until quantum computers become more widespread, traditional methods like RSA and AES remain secure for now.
However, once quantum computers become mainstream, classical encryption will face serious challenges. In fact, experts are already working on post-quantum cryptography—new algorithms designed to withstand quantum attacks. But for now, quantum cryptography exists alongside classical methods, offering an extra layer of protection.
Current Challenges in Quantum Cryptography Development

Quantum cryptography sounds amazing, right? But there are still hurdles to clear before it’s ready for the big leagues. One of the biggest challenges is decoherence—the tendency of qubits to lose their quantum state due to external noise or environmental factors. Think of it like trying to keep a soap bubble intact on a windy day; the quantum state is incredibly fragile and can collapse easily.
Another obstacle is the hardware. Right now, maintaining and manipulating qubits requires incredibly precise conditions—often temperatures near absolute zero and specialized equipment. This makes quantum cryptography systems expensive and impractical for widespread use—at least for now. But as technology improves, these barriers are likely to fall.
Overcoming Noise and Decoherence: The Road Ahead for Qubits
Dealing with noise and decoherence is one of the most significant challenges for quantum cryptography. Imagine trying to have a private conversation in a crowded, noisy room—eventually, your words get drowned out, and communication breaks down. That’s exactly what happens to qubits when exposed to environmental interference. They lose their quantum properties, making encryption unreliable.
Researchers are working on ways to combat this by developing error-correction techniques and more stable qubit systems. One potential solution is using quantum error correction codes, which help detect and correct mistakes caused by noise, ensuring that the qubits remain stable enough for reliable encryption. It’s a work in progress, but each breakthrough moves us closer to practical, everyday quantum encryption.
Real-World Applications of Quantum Cryptography
Though it may sound futuristic, quantum cryptography is already stepping out of the lab and into the real world. Banks, government agencies, and tech companies are all beginning to explore its potential. One key application is in secure communications, where sensitive information can be exchanged without fear of eavesdropping. For example, Quantum Key Distribution (QKD) is being used to safeguard national security communications and financial transactions.
Other industries that rely on ultra-secure data transmission, like healthcare and defense, are also looking to quantum cryptography for solutions. The prospect of creating unbreakable encryption could revolutionize how these industries handle confidential information, ensuring that data breaches become a thing of the past.
Could Quantum Cryptography Protect Against Quantum Hackers?
As quantum computers evolve, there’s a growing concern that they could be used by hackers to break current encryption methods. This has given rise to the term quantum hackers—malicious actors who could potentially exploit quantum computing to crack encrypted data. But here’s the silver lining: quantum cryptography is designed to be quantum-proof.
Because qubits operate in ways that classical systems cannot comprehend, they provide security even in the face of quantum attacks. For instance, QKD ensures that any attempt to intercept a quantum key is immediately detected. In theory, as long as quantum cryptography is properly implemented, it should be able to resist even the most advanced quantum-based hacking attempts.
Quantum vs Classical: Can They Coexist?
Despite the hype, quantum cryptography isn’t here to totally wipe out classical encryption—not yet, anyway. Right now, both systems are learning to coexist. Classical methods are tried and tested, handling day-to-day encryption needs efficiently. Meanwhile, quantum cryptography is being developed for high-stakes, high-security applications where the absolute protection of information is critical.
The future likely holds a hybrid model, where quantum techniques are layered on top of classical encryption methods. This approach would provide an added layer of security without needing to overhaul every encryption system we currently rely on. In essence, classical and quantum cryptography can work together, with each offering its unique strengths.

The key differences between classical encryption and quantum cryptography. This might feature elements like “Classical Key Exchange” and “Quantum Key Distribution” with bullet points summarizing each one
Governments and Corporations Leading the Quantum Charge
It’s not just scientists in white coats who are excited about quantum cryptography—big players in both government and business are investing heavily in the technology. Countries like China and the United States are leading the race, with massive funding going into quantum research and development. For example, China has already launched a quantum satellite, known as Micius, to test long-distance quantum communication.
Corporations like Google, IBM, and Microsoft are also heavily involved. They’re pouring resources into building quantum computers and exploring quantum encryption systems. These tech giants see quantum cryptography not just as the future of security, but as a competitive edge in the tech industry’s next revolution.
A Peek Into the Future: Where Will Quantum Cryptography Lead Us?
The future of quantum cryptography is filled with possibilities that could dramatically change how we protect data. In the next decade, we might see quantum encryption become the standard for securing sensitive communications. As quantum computers continue to develop, they will push traditional encryption methods to their breaking point, leading to a widespread shift toward quantum-resistant technologies.
We’re also likely to witness the rise of quantum networks, where quantum-encrypted data flows through entangled qubits across vast distances. Imagine a world where global communications are secured by the laws of physics themselves, making hacking attempts virtually futile. The exciting part? This is not a sci-fi fantasy—it’s a plausible reality within our lifetime.
How Soon Will Quantum Cryptography Be Mainstream?
So, when can we expect to see quantum cryptography become part of our everyday digital lives? It’s hard to say with certainty, but experts believe we’re still several years away from widespread adoption. The technology is advancing rapidly, but challenges like scalability, cost, and hardware requirements need to be addressed before quantum encryption can be deployed on a global scale.
However, some industries—like banking and defense—are already investing in quantum-safe encryption methods to future-proof their data security. For the general public, the rollout of quantum cryptography might happen gradually, as hybrid systems blending quantum and classical techniques become more accessible and affordable.
Conclusion: The Dawn of a New Cryptographic Era
While quantum cryptography is still in its early stages, it represents a giant leap forward in the quest for unhackable security. With qubits at its core, this revolutionary approach could outpace the capabilities of classical encryption and safeguard data against the threats posed by quantum computers.
As we move closer to the era of quantum computing, the need for quantum-resistant encryption becomes more pressing. Whether through Quantum Key Distribution, entanglement, or superposition, qubits offer a glimpse into a future where data security is governed by the very laws of nature. The journey to mainstream adoption may be long, but the end result promises to be nothing short of revolutionary.
Resources:
- IBM Quantum Computing
Learn about IBM’s advancements in quantum computing and how they’re contributing to the future of quantum cryptography. - National Institute of Standards and Technology (NIST)
NIST is working on post-quantum cryptography standards to protect against future quantum threats.
NIST Post-Quantum Cryptography - Quantum Cryptography at MIT
Explore research and educational resources on quantum encryption and QKD at MIT.
MIT Quantum Research - Google Quantum AI
Google’s quantum computing division, which is working on the development of quantum encryption technologies.
Google Quantum AI - The Quantum Security Initiative (QSI)
A resource center dedicated to exploring the security implications of quantum technologies and quantum cryptography.
Quantum Security Initiative - European Union Quantum Flagship
The EU’s massive investment in quantum technologies, including quantum cryptography and quantum communications.
EU Quantum Flagship - Center for Quantum Networks
Research on building the infrastructure for quantum communication and the quantum internet, key for future quantum cryptography.
Center for Quantum Networks - “Quantum Computation and Quantum Information” by Nielsen & Chuang
A foundational textbook that covers quantum computing and quantum cryptography in-depth.
Quantum Computation and Quantum Information - Quantum Key Distribution (QKD) Overview – ID Quantique
A leading provider of quantum encryption solutions, including QKD systems.
ID Quantique - Arxiv.org – Quantum Cryptography Research Papers
Access the latest research papers on quantum cryptography from academic experts and institutions around the world.
Arxiv Quantum Cryptography