
Robotic Process Automation (RPA) is transforming industries, enabling businesses to automate repetitive tasks with ease. However, as RPA adoption skyrockets, data security and risk management challenges are becoming top priorities.
Securing RPA environments is crucial for protecting sensitive information and maintaining operational integrity. This guide will explore the essential strategies and tools to secure RPA effectively, from data encryption to access control.
Understanding RPA Security Challenges
RPA introduces unique risks, especially since bots often handle sensitive data. Recognizing these challenges is the first step in building a secure automation framework.
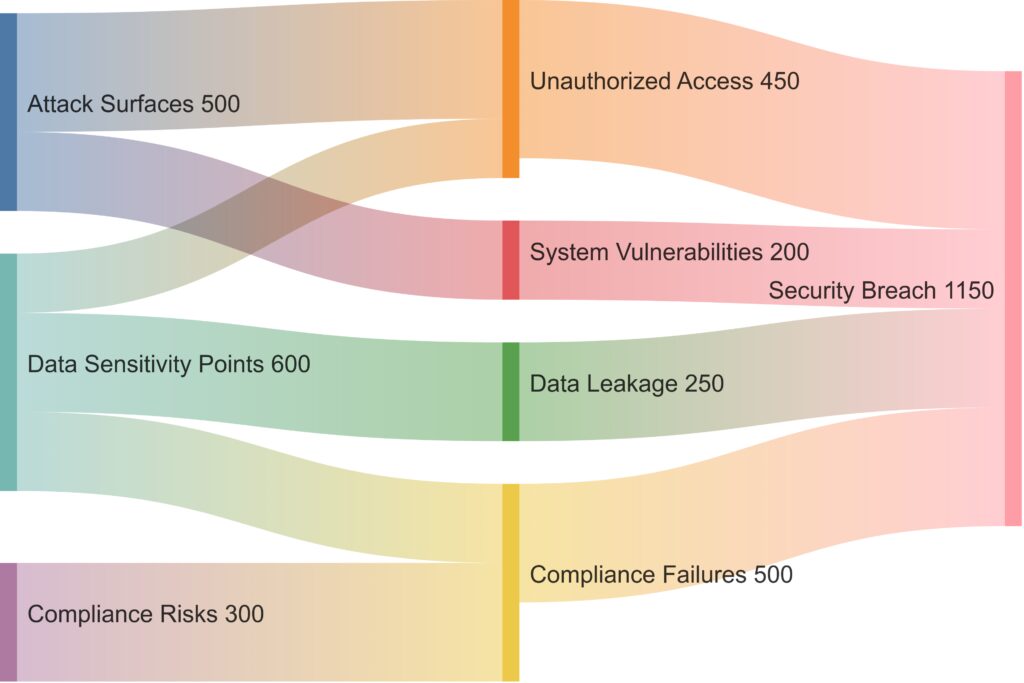
Risk Categories:Attack Surfaces: Contributes to unauthorized access and system vulnerabilities.
Data Sensitivity Points: Increases risks for data leakage, unauthorized access, and compliance failures.
Compliance Risks: Leads primarily to compliance failures.
Security Breaches: Aggregated from different risk areas, indicating the impact of unauthorized access, data leakage, and compliance issues.
The color gradients and arrow thickness visually represent the magnitude of each risk contribution.
Data Sensitivity and RPA
RPA bots frequently interact with sensitive data such as personal information, financial records, and business secrets. This direct access raises the stakes: if a bot is compromised, the data it handles is at risk, too. Safeguarding sensitive data is critical, particularly for industries subject to stringent regulations like finance and healthcare.
Unauthorized access, accidental data leaks, and bot misconfigurations are just a few ways data can be exposed.
Increasing Attack Surfaces
RPA introduces new potential vulnerabilities. Each bot represents an endpoint that can be exploited if not adequately protected. Since bots often mimic human actions, they may inherit vulnerabilities in the systems they interact with, like legacy applications or weakly secured APIs. Inadequate bot security management can result in an expanded attack surface for cyber threats.
Compliance and Regulatory Risks
When bots interact with sensitive data, organizations must consider compliance with data protection regulations such as GDPR or HIPAA. Regulatory risks are amplified because automation often results in higher transaction volumes, which means a single breach could expose significant amounts of data. Failure to meet regulatory standards can result in hefty fines and reputational damage.
Essential Security Measures for RPA

To effectively protect sensitive data and manage risks, RPA security should be addressed holistically. Key areas include access controls, data encryption, and proper bot lifecycle management.
Implementing Access Controls
Access controls are crucial in defining which users, bots, and applications can interact with sensitive data and functions.
- Role-based access control (RBAC) restricts bot access based on assigned roles, ensuring they only perform necessary actions. By assigning specific permissions, organizations reduce the risk of unauthorized access.
- Multi-factor authentication (MFA) can further secure bot logins, ensuring only authenticated users can manage and interact with bots.
- User behavior monitoring helps detect unusual bot behavior, which might indicate a security breach.
Access control measures limit exposure, reducing the chances of accidental or malicious data access.
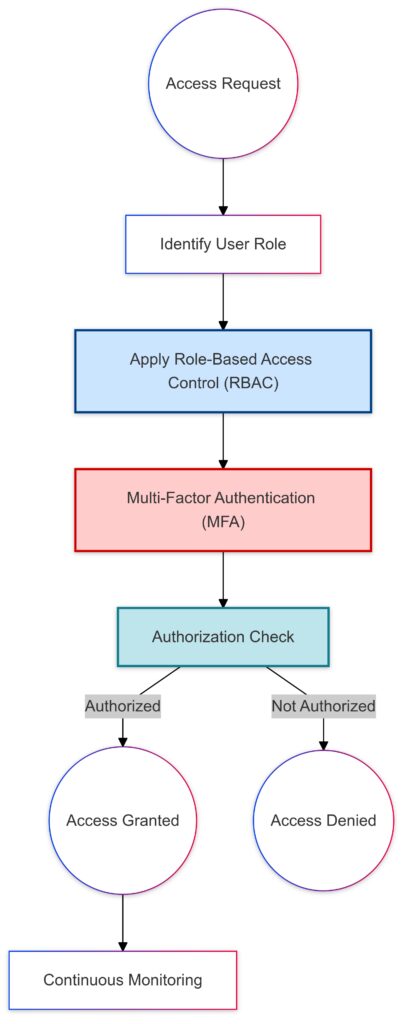
Access Request: The user initiates an access request.
Role Identification: The system identifies the user’s role.
Role-Based Access Control (RBAC): Ensures that access permissions are aligned with the role.
Multi-Factor Authentication (MFA): Adds an extra layer of security.
Authorization Check: Final validation to either grant or deny access.
Monitoring: Continuous monitoring after access is granted.
Highlighted Security Elements:
MFA (in red): Emphasizes the added security layer.
RBAC and Authorization: Ensures role-based restrictions and validates access permissions.
Data Encryption and Protection
Data encryption is a cornerstone of RPA security. Encrypting sensitive data—both at rest and in transit—protects it from unauthorized access.
- Encryption protocols like TLS (Transport Layer Security) should be used to protect data as it moves between bots and systems.
- Encryption of logs is essential, as logs may store sensitive data processed by bots. Secure storage of these logs ensures confidentiality even in the case of a breach.
- Data masking can further protect sensitive information, allowing bots to process data without exposing it.
These practices ensure data integrity, confidentiality, and compliance with data protection regulations.
Securing Bot Credentials
Bots require credentials to interact with different systems, but poorly managed credentials can be a security risk.
- Credential vaulting stores bot credentials securely, ensuring only authorized bots have access to them. Vaulting can also log usage for auditing purposes.
- Rotating credentials regularly further limits the risk of misuse, especially in environments where bots access multiple applications.
- Automatic credential expiration prevents stale credentials from being reused by unauthorized entities, enhancing security across the RPA ecosystem.
These steps protect bots and systems from unauthorized access while managing credentials efficiently.
Monitoring and Auditing RPA Activity

Continuous monitoring and auditing help identify security risks and mitigate them before they escalate. This involves tracking bot activity and analyzing any anomalies that could indicate a potential security breach.
Real-Time Monitoring for Threat Detection
Real-time monitoring allows organizations to detect suspicious activity as it happens. Tools with real-time analytics and alert capabilities can notify administrators of unusual bot behavior, enabling a quick response to potential threats. Monitoring solutions can log each bot’s actions, making it easier to track any unauthorized access attempts or data manipulation.
- Alert mechanisms trigger immediate responses to anomalies, helping to contain issues before they impact sensitive data.
- Integration with security information and event management (SIEM) systems consolidates RPA logs with broader enterprise security logs for a comprehensive security view.
Auditing for Compliance
Regular auditing is essential for maintaining compliance with data protection regulations and internal policies. Audit logs provide visibility into who accessed what data and when.
- Regular bot activity reviews can reveal access patterns, allowing administrators to adjust permissions as needed.
- Compliance reporting is facilitated by auditing tools, helping organizations stay aligned with legal requirements and industry standards.
- Periodic access reviews ensure that only authorized users and bots have the necessary permissions, reducing the likelihood of accidental exposure.
By regularly auditing and reviewing bot activity, organizations can maintain a security posture that aligns with both internal and external regulations.
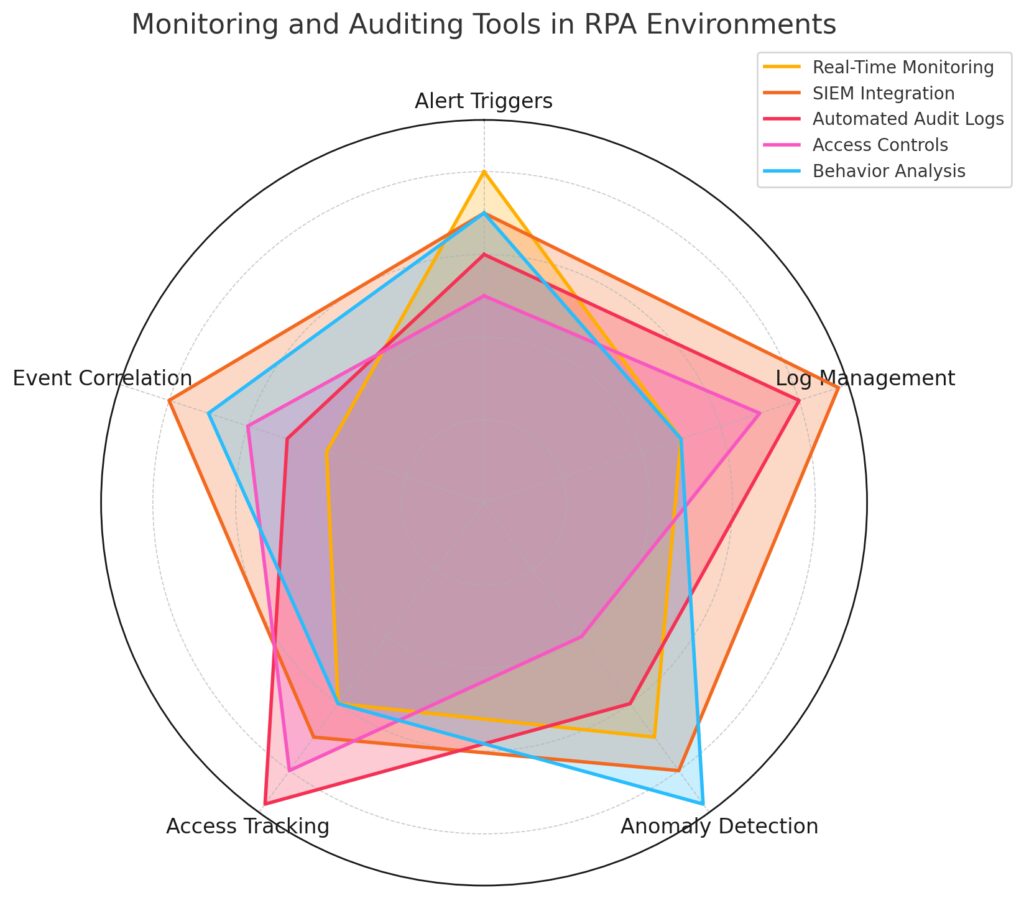
Tools: Real-Time Monitoring, SIEM Integration, Automated Audit Logs, Access Controls, and Behavior Analysis.
Metrics: Each segment includes “Alert Triggers,” “Log Management,” “Anomaly Detection,” “Access Tracking,” and “Event Correlation.”
This chart visually demonstrates how different tools contribute to each metric, highlighting strengths in areas such as log management for SIEM integration and anomaly detection for behavior analysis.
Managing Bot Lifecycle for Security
Bots, like any other software, require regular maintenance and updates to remain secure. Managing the bot lifecycle—from development to deployment and eventual retirement—is essential for minimizing security risks.
Secure Bot Development Practices
Secure bot development begins with designing bots to handle data safely and perform only the actions they’re authorized for.
- Minimize bot permissions during development to restrict access to only necessary data and functions.
- Testing and validation during development can identify potential vulnerabilities before bots are deployed, reducing the risk of security flaws.
- Static code analysis tools can help developers detect security issues in bot scripts, especially if bots interact with sensitive data.
By following secure development practices, organizations can reduce the likelihood of vulnerabilities in production bots.
Regular Bot Maintenance
Once deployed, bots should be regularly maintained to ensure they’re functioning securely and efficiently.
- Patch management is crucial, as bots may interact with systems that receive regular security updates.
- Performance monitoring helps ensure bots aren’t creating unexpected bottlenecks, which could introduce vulnerabilities.
- Error handling mechanisms should be in place to ensure that bots can manage unexpected failures without compromising sensitive data.
Maintaining bots ensures they continue to operate within secure parameters and adapt to any evolving security needs.
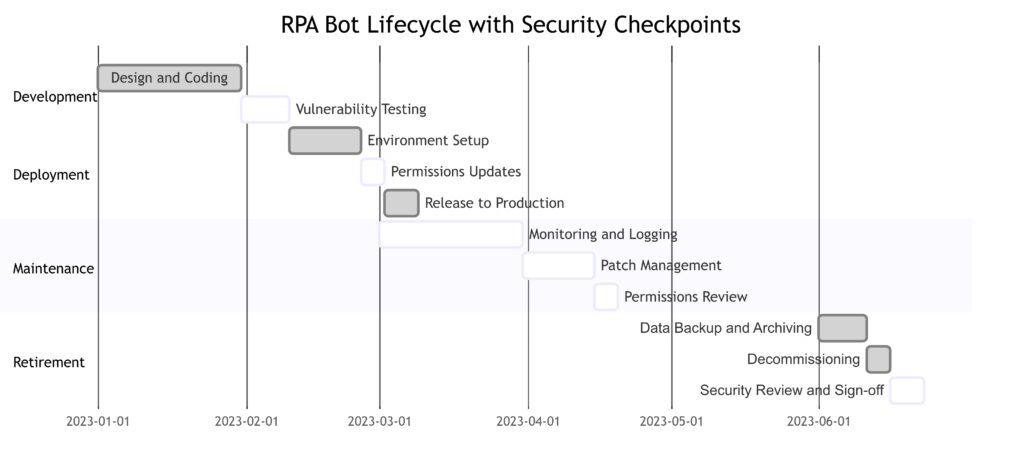
Development: Includes initial design, coding, and vulnerability testing.
Deployment: Focuses on environment setup, permissions updates, and production release.
Maintenance: Continuous monitoring, logging, patch management, and periodic permissions reviews.
Retirement: Covers data backup, bot decommissioning, and final security review.
Advanced RPA Security Techniques
As RPA environments become more complex, implementing advanced security measures can help organizations stay ahead of potential threats. Techniques like threat modeling, automated security responses, and AI-driven anomaly detection provide additional layers of protection.

Threat Modeling for RPA
Threat modeling is a proactive approach to identify potential vulnerabilities and attack vectors within an RPA system. This method evaluates the ways malicious actors could exploit weaknesses and provides a roadmap for prioritizing security improvements.
- Identify attack vectors: Consider how bots could be targeted, such as through credential theft or application exploits. Understanding these vectors helps in implementing specific defenses.
- Risk assessment: By gauging the potential impact of each threat, organizations can prioritize the most critical areas for RPA security.
- Mitigation strategies: Develop targeted defenses based on the model, such as isolating bots in secure environments and limiting their access to high-risk systems.
Threat modeling strengthens security by anticipating and addressing vulnerabilities before they can be exploited.
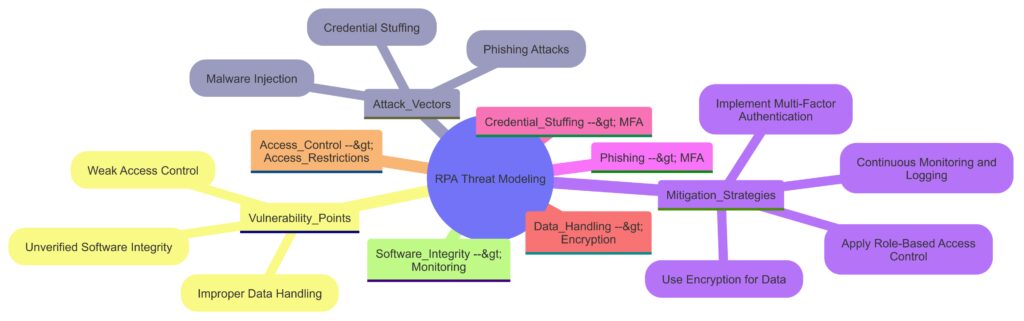
Attack Vectors: Includes threats like phishing, malware injection, and credential stuffing.
Vulnerability Points: Lists weaknesses such as weak access control, improper data handling, and unverified software integrity.
Mitigation Strategies: Outlines prevention techniques like multi-factor authentication (MFA), data encryption, role-based access control, and continuous monitoring.
Connections are made between specific threats and corresponding mitigation strategies to illustrate how each technique helps secure the RPA environment.
Automated Security Responses
Automating security responses within RPA workflows can help prevent security incidents from escalating. When combined with continuous monitoring, automated responses allow organizations to act quickly when threats arise.
- Automated shutdowns: If a bot exhibits unusual behavior, an automated system can stop the bot and restrict access, limiting potential damage.
- Immediate alerts and lockdowns: Integration with monitoring tools allows administrators to receive instant alerts and initiate lockdown procedures, if necessary.
- Automated audit logs: Ensures that every action is documented, which helps with compliance and enables a thorough investigation if a security incident occurs.
Automation minimizes response times and helps contain threats, protecting sensitive data from unauthorized access.
AI-Driven Anomaly Detection
Integrating AI-driven anomaly detection with RPA can bolster security by identifying unusual patterns that may indicate a threat. AI tools analyze data and flag potential security issues, enhancing the ability to detect sophisticated attacks.
- Behavioral analysis: AI tools establish a baseline of normal bot behavior and detect deviations, which could indicate compromised credentials or other security issues.
- Predictive analytics: By analyzing historical data, AI can predict potential security risks, allowing administrators to take preventative measures.
- Continuous improvement: AI-based systems adapt over time, refining their ability to detect threats as more data is gathered.
AI-driven security can help identify subtle threats that traditional monitoring tools might miss, providing an additional layer of defense.
Ensuring Compliance in RPA Security

Compliance is a significant concern for organizations implementing RPA, especially in industries that handle sensitive data. Maintaining a secure RPA environment that aligns with regulatory standards is essential to avoid penalties and protect reputation.
Data Protection Regulations
RPA workflows involving personal or financial data must comply with regulations like GDPR, HIPAA, and CCPA. Non-compliance can result in penalties and legal repercussions.
- Data minimization: Only collect and process data essential for bot operations. By minimizing the amount of data handled, organizations reduce exposure to regulatory risks.
- Privacy by design: Embed privacy measures into RPA workflows from the outset, such as data anonymization and secure storage practices.
- Regular audits: Conduct compliance audits to ensure bots are following regulatory guidelines, especially when processing sensitive information.
Meeting regulatory requirements not only avoids penalties but also builds trust with customers and stakeholders.
Record-Keeping and Documentation
Maintaining thorough documentation of bot actions and access logs is vital for compliance. Detailed records enable organizations to demonstrate adherence to regulatory standards.
- Access logs: Track who accessed what data and when, ensuring an accurate record of all interactions with sensitive information.
- Audit trails: Maintain an audit trail of bot activity, particularly for high-risk transactions. Audit trails are crucial for investigating incidents and proving compliance during audits.
- Change management records: Document any changes to bot permissions or access rights, which helps organizations stay aligned with regulatory requirements.
Comprehensive record-keeping is essential for compliance and provides valuable insights for managing RPA security.
RPA Security Best Practices for the Future
The RPA landscape is constantly evolving, and staying ahead requires a proactive approach to security. Following best practices and adapting to new security trends can help organizations safeguard their RPA environments effectively.
Continuous Security Education
Keeping teams informed about the latest security risks and best practices is essential for maintaining a strong security posture.
- Training programs: Conduct regular training for developers, IT staff, and RPA administrators on security practices and potential risks.
- Awareness campaigns: Educate employees on how to identify and report suspicious activities related to RPA.
- Policy updates: Regularly review and update RPA security policies to address new threats or changes in the regulatory landscape.
Ongoing education ensures that teams are well-equipped to recognize and respond to security issues as they arise.
Collaboration with Security Teams
Working closely with IT security teams can enhance RPA security by integrating established security practices with automation processes.
- Joint risk assessments: Collaborate on risk assessments to identify potential vulnerabilities in RPA workflows.
- Security integration: Incorporate existing security tools, such as firewalls and intrusion detection systems, into RPA environments for comprehensive protection.
- Incident response planning: Develop and test incident response plans specifically for RPA, ensuring rapid responses to potential security breaches.
Close collaboration ensures that RPA security aligns with overall organizational security efforts, creating a unified defense strategy.
Adapting to Emerging Security Trends
The security landscape is continuously changing, and staying updated with new trends helps organizations address evolving threats.
- Zero-trust frameworks: Implement a zero-trust security approach, where every access request is verified, regardless of the source.
- Cybersecurity frameworks: Align RPA security with established frameworks like NIST and ISO, which provide guidelines for risk management and security.
- New encryption standards: As encryption methods evolve, adopting the latest standards helps ensure that data remains protected from unauthorized access.
Remaining adaptable and proactive allows organizations to maintain a strong security posture, even as new threats emerge.
Securing RPA is a multifaceted effort that requires vigilance, proactive measures, and collaboration across teams. By integrating robust security practices with advanced monitoring and compliance efforts, organizations can effectively protect their sensitive data and manage risks associated with automation.
FAQs
What are the main security risks associated with RPA?
RPA introduces risks such as unauthorized access to sensitive data, bot misuse, and expanded attack surfaces. Bots often handle confidential information and interact with multiple systems, which can increase exposure to cyber threats. Additionally, compliance risks are high since a single bot compromise can lead to significant data leakage.
How can access control improve RPA security?
Implementing access control, such as role-based access control (RBAC), ensures that bots and users only access necessary data and functions. Multi-factor authentication (MFA) and regular user behavior monitoring further strengthen access security, reducing unauthorized data access and potential misuse of bot credentials.
Why is data encryption important for RPA?
Data encryption protects sensitive information as it moves between bots and systems, safeguarding against unauthorized access. Encrypting both data at rest and data in transit is essential. Securing logs and credentials with encryption adds another layer of defense, maintaining data confidentiality in the event of a breach.
How can AI-driven anomaly detection enhance RPA security?
AI-driven anomaly detection identifies unusual bot activity by establishing baselines for normal behavior and flagging deviations. This proactive approach detects subtle security threats that traditional tools might miss, allowing organizations to respond quickly to potential breaches and maintain secure RPA operations.
What role does threat modeling play in RPA security?
Threat modeling proactively identifies potential vulnerabilities and attack vectors specific to RPA workflows. This approach helps organizations understand how malicious actors might exploit weaknesses, allowing them to prioritize mitigation strategies, such as isolating bots in secure environments and restricting access to sensitive systems.
How does compliance affect RPA security practices?
Organizations using RPA to handle personal or financial data must comply with regulations like GDPR and HIPAA. Compliance requirements impact how bots handle data, from minimizing data collection to ensuring secure storage. Regular audits and documentation are critical to maintaining compliance and avoiding penalties.
Why is continuous monitoring necessary in RPA environments?
Continuous monitoring allows for real-time tracking of bot activity, which helps detect security threats as they arise. Real-time alerts, integration with SIEM systems, and automated shutdowns upon unusual activity contribute to a quick, effective response to threats, keeping data secure and minimizing potential damage.
What are the best practices for maintaining bot security?
Best practices include credential vaulting, periodic audits, regular access reviews, and using secure bot development practices. Patching and performance monitoring keep bots updated and secure, while error-handling mechanisms ensure that bots can manage unexpected failures without compromising data security.
How can organizations protect bot credentials?
Organizations can protect bot credentials by using credential vaults that securely store login details, limiting direct access. Regularly rotating credentials and enforcing automatic expiration also help reduce misuse risk. This ensures that even if credentials are exposed, they are only temporarily valid, enhancing overall bot security.
Why is bot lifecycle management important for RPA security?
Managing a bot’s lifecycle, from development through deployment and retirement, helps minimize security vulnerabilities. By regularly updating and patching bots, testing for vulnerabilities, and retiring outdated bots, organizations can prevent outdated or unpatched bots from exposing sensitive data.
What is data masking, and how does it improve RPA security?
Data masking hides or replaces sensitive data elements with fictitious values, allowing bots to process information without directly exposing it. This technique is especially useful when bots handle confidential information, as it reduces the risk of data leaks or exposure during processing and testing.
How does auditing support compliance in RPA?
Auditing creates a transparent record of all bot activities, data access points, and user interactions. Regular audit reviews ensure that bots are compliant with data protection standards, while providing a documented trail for regulatory bodies, thus minimizing the risk of compliance violations and fines.
What is the zero-trust approach, and why is it relevant for RPA security?
A zero-trust approach means that no user, system, or bot is inherently trusted. In RPA, this approach ensures that every access request—whether from bots or users—requires authentication and authorization. This method helps prevent unauthorized data access and mitigates potential threats within automated workflows.
How does patch management impact RPA security?
Patch management ensures that bots and the systems they interact with remain secure by regularly updating them with the latest security patches. Unpatched bots can become vulnerable entry points for attacks, especially if they access legacy or high-risk systems. Regular patching is crucial to prevent exploitation of known vulnerabilities.
What types of data are most vulnerable in RPA workflows?
Data that includes personal, financial, and proprietary business information is particularly vulnerable in RPA workflows. Since bots can access and process this information, inadequate security practices can expose it to misuse or theft. Encrypting, masking, and controlling access to sensitive data are essential to protect it.
Why is collaboration with security teams crucial for RPA security?
Collaborating with IT and security teams enables a unified approach to securing RPA environments. Security experts provide insights on risk management, help in setting up monitoring tools, and support incident response planning. This alignment ensures that RPA-specific security needs are met within the broader enterprise security framework.
How does data minimization reduce security risks in RPA?
Data minimization restricts bots from collecting or processing more information than necessary, reducing the amount of sensitive data they handle. This approach limits exposure in case of a breach and helps organizations stay compliant with regulations that prioritize data privacy and limiting data usage.
What should an incident response plan for RPA include?
An incident response plan for RPA should include steps for detecting, responding to, and mitigating bot-related security breaches. It should outline specific actions like disabling affected bots, analyzing logs, notifying stakeholders, and documenting the response for auditing. Testing and regularly updating this plan are essential to ensure its effectiveness in an actual breach.
How can regular security training support RPA security efforts?
Regular security training keeps developers, RPA admins, and users aware of potential risks and best practices for RPA security. Training programs improve understanding of secure bot management, credential protection, and compliance requirements, reducing the chances of accidental security breaches caused by human error.
What role do SIEM systems play in RPA security?
Security Information and Event Management (SIEM) systems centralize security data from across an organization, including RPA activity logs, for real-time monitoring and incident response. Integrating RPA logs with SIEM tools helps detect anomalies and provides comprehensive insights into security events, making it easier to identify and respond to potential threats in RPA workflows.
How can error handling improve RPA security?
Effective error handling ensures that bots respond safely to unexpected events, like missing data or system failures, without compromising data security. By incorporating secure error-handling procedures, organizations reduce the risk of exposing sensitive information when a bot encounters an error, protecting both data integrity and privacy.
Resources
RPA Security Tools and Platforms
- UiPath Security & Governance: UiPath offers extensive security features, including credential vaults, role-based access, and monitoring capabilities tailored to RPA environments. UiPath Security
- Automation Anywhere Enterprise Security: Automation Anywhere’s RPA platform provides security options like secure credential management, access control, and data encryption. Automation Anywhere Security
- Blue Prism Security: Blue Prism’s RPA platform includes features such as multi-factor authentication, data masking, and security audit trails to ensure comprehensive RPA security. Blue Prism Security