
The fusion of artificial intelligence (AI) and photonic cryptography is redefining how we approach data security in the digital age. With the rise of quantum computing, traditional encryption methods are at risk, making quantum light-based solutions a promising frontier.
The Basics of Photonic Cryptography
What Is Photonic Cryptography?
Photonic cryptography harnesses quantum properties of light particles (photons) to encrypt information. Unlike traditional cryptographic methods relying on computational complexity, this approach uses the physics of quantum mechanics to secure data.
Quantum light enables:
- Quantum Key Distribution (QKD): A secure way to share encryption keys.
- Eavesdropping detection: Alterations in quantum states reveal unauthorized access attempts instantly.
The result? Virtually unbreakable encryption—unless physics itself is rewritten.
Why the Need for Quantum Solutions?
With the advent of quantum computers, classical encryption like RSA and ECC will become vulnerable to attacks. Quantum-safe algorithms are a necessity to future-proof data security.
Photonic cryptography stands out by offering inherent resilience, but implementing it at scale remains challenging. Enter AI, the perfect partner to simplify these complexities.
The Role of AI in Photonic Cryptography
AI for Optimizing Quantum Key Distribution
Quantum Key Distribution (QKD) requires managing intricate variables such as photon polarization, noise interference, and transmission losses. AI-driven algorithms can analyze these factors in real time, optimizing:
- The stability of photon transmission across networks.
- The detection and prevention of interception attempts.
For example, AI-enabled predictive models can adapt QKD protocols dynamically, maximizing security under changing conditions.
Advanced Error Correction with Machine Learning
Noise and errors are common in quantum systems. Machine learning (ML) algorithms excel at:
- Identifying patterns in noisy environments.
- Applying error-correction protocols efficiently.
By improving signal fidelity, AI ensures quantum data remains reliable, even across long distances or in imperfect environments.
Automating Quantum Cryptographic Protocols
Photonic cryptography is resource-intensive to deploy and maintain. AI simplifies this through:
- Automated deployment of cryptographic systems.
- Streamlined management of quantum networks.
Such automation reduces human error while accelerating adoption, making secure communication accessible for industries worldwide.
Advanced Applications of AI in Photonic Cryptography
Securing Financial Transactions
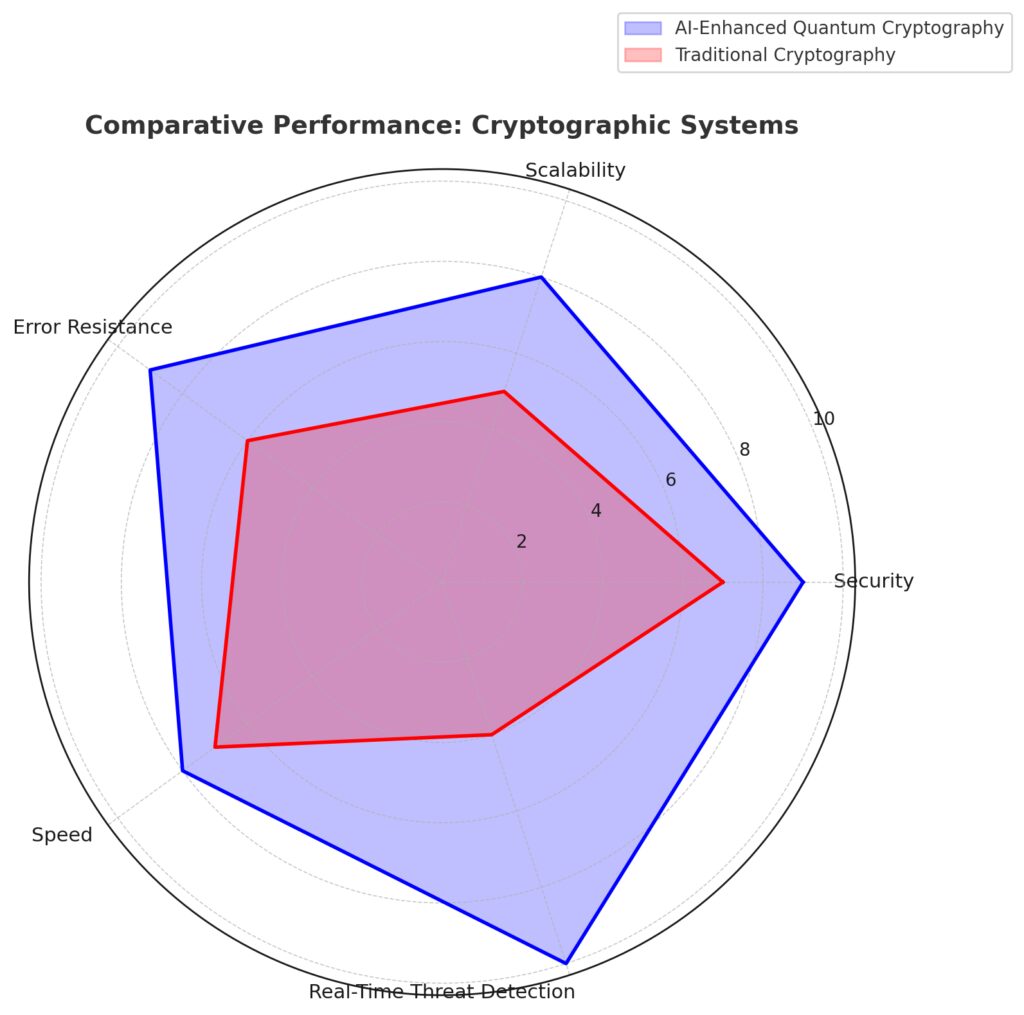
A comparative analysis of traditional cryptography versus AI-enhanced quantum cryptography across key performance metrics.
Banks and financial institutions require top-tier encryption for millions of transactions daily. AI-enhanced photonic cryptography provides:
- Tamper-proof communication channels for interbank transfers.
- Scalability to handle high-speed, high-volume data exchanges.
Protecting Government Communications
Governments face relentless cyber threats. AI-assisted quantum encryption safeguards:
- Military communication systems.
- Diplomatic transmissions and classified data exchanges.
The ability to detect and thwart espionage attempts in real time offers unparalleled peace of mind.
AI-Driven Quantum Key Management
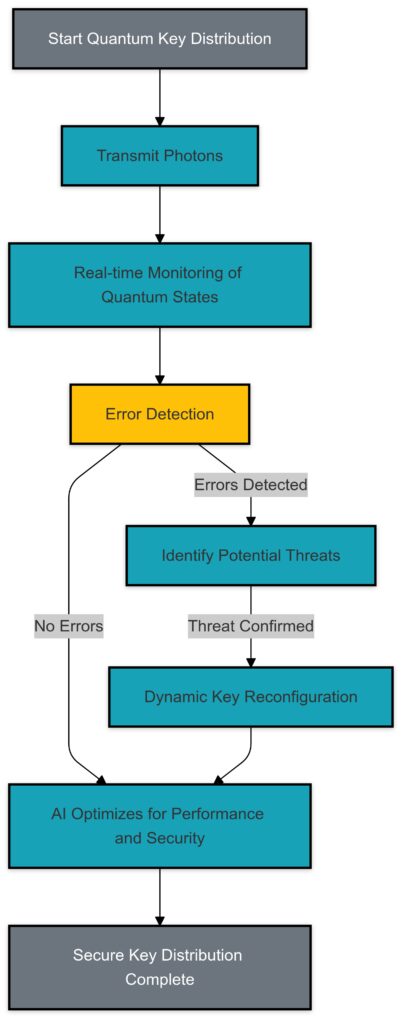
AI-driven optimization of quantum key distribution through error detection, threat management, and real-time system adaptation.
The process of generating, distributing, and managing encryption keys in QKD is technically intricate. AI simplifies this through:
- Dynamic key allocation: Ensuring real-time adaptation to changes in the network.
- Fault-tolerant protocols: Identifying and mitigating errors during key transmission.
- Resource optimization: Allocating bandwidth and quantum channels efficiently, even in high-traffic systems.
For instance, AI can analyze the optimal polarization states of photons for transmission, ensuring minimal data loss and higher fidelity in secure communications.
Reinforcement Learning for Enhanced Security
Reinforcement learning—a subset of AI—plays a critical role in adaptive security mechanisms. These algorithms continuously improve by “learning” from attempts to intercept quantum data.
- Real-time threat modeling: Detecting and neutralizing eavesdropping strategies.
- Adaptive encryption protocols: Changing quantum states or paths dynamically to evade detection.
This allows systems to evolve and outsmart attackers, even as new vulnerabilities arise.
Quantum Network Optimization with AI
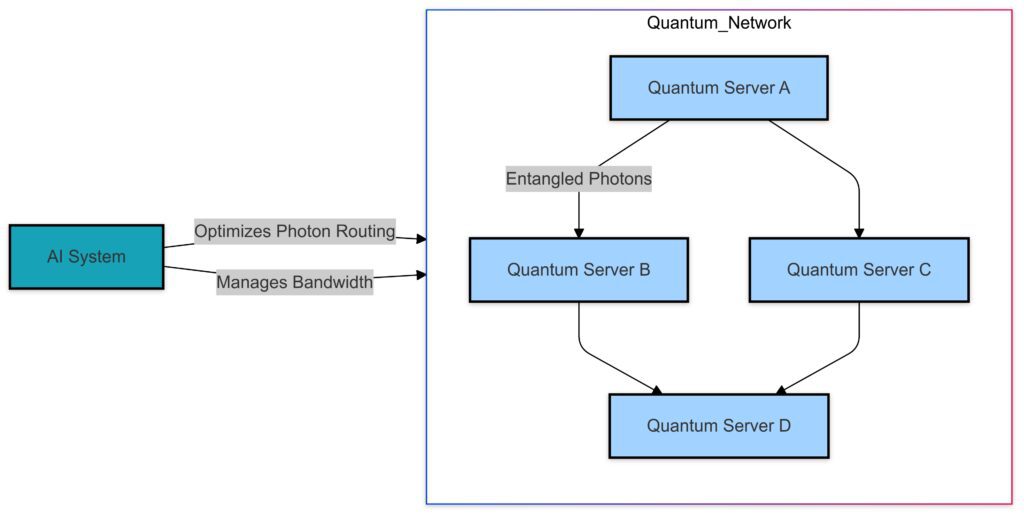
Creating a global quantum network requires managing multiple quantum nodes, connections, and channels. AI optimizes:
- Routing paths for photons: Ensuring minimal loss and high-speed transmission.
- Scalability solutions: Expanding quantum networks to accommodate more users and devices without degrading security or performance.
- Bandwidth allocation: Balancing network traffic to maximize efficiency.
AI’s ability to model and predict quantum behavior is critical to achieving these feats at scale.
Challenges and Opportunities Ahead
Addressing Quantum Decoherence
Quantum systems are notoriously fragile. Decoherence occurs when photons lose their quantum states due to environmental interference.
AI combats this by:
- Predicting decoherence events: Using machine learning to anticipate and mitigate environmental factors.
- Error correction algorithms: Restoring lost quantum states with minimal data loss.
Building a Scalable Quantum Network
Scaling quantum systems from labs to real-world applications requires addressing challenges like:
- Photon loss over distance: AI improves the efficiency of quantum repeaters.
- Network congestion: Algorithms dynamically adjust traffic to maintain performance.
These advancements bring us closer to the realization of a global quantum internet.
Ensuring Interoperability with Classical Systems
Bridging quantum and classical networks is another significant challenge. AI facilitates:
- Hybrid encryption models: Allowing quantum and classical systems to communicate securely.
- Seamless integration: AI ensures compatibility without compromising security.
This interoperability is key to transitioning industries toward quantum-safe operations.
How AI and Photonics Complement Emerging Technologies
Revolutionizing Telecommunications
The integration of AI and quantum photonics is reshaping how data travels across communication networks. Future telecommunications may leverage:
- Quantum repeaters: AI improves their efficiency to enable long-distance quantum communication.
- Real-time optimization of optical networks: By analyzing photon paths, AI ensures minimal latency and maximal throughput.
These advancements will not only enhance global internet security but also pave the way for quantum internet, a network inherently immune to cyberattacks.
Enhancing Cybersecurity with AI-Driven Quantum Algorithms
AI-driven models analyze and refine quantum cryptographic protocols for:
- Identifying emerging threats faster than human capabilities.
- Implementing adaptive encryption to counter evolving cyberattack methods.
The combination of AI and photonic cryptography creates a proactive security framework—a stark contrast to today’s reactive models.
Synergy with Blockchain Technology
Quantum encryption and AI bolster blockchain systems by:
- Enhancing smart contract security using quantum-safe keys.
- Providing instant fraud detection with AI analysis of transaction patterns.
This synergy positions blockchain as an even stronger candidate for secure, decentralized applications in finance, healthcare, and beyond.
Industries Leading the Quantum Light Revolution
The Tech Industry’s Quantum Leap
Tech giants like Google and IBM are investing in quantum computing and photonic networks. By incorporating AI, these companies aim to:
- Scale quantum systems for practical use.
- Deliver robust cybersecurity solutions for enterprises and consumers alike.
Aerospace and Defense
The defense sector prioritizes secure communication, particularly for satellites and military networks. AI-empowered quantum systems enhance:
- Satellite-to-ground communication encryption.
- Resistance to sophisticated cyberespionage efforts.
Healthcare Data Security
In healthcare, AI and photonic cryptography ensure sensitive patient information remains confidential, even during transmission between facilities or cloud servers.
Future Possibilities with AI and Quantum Light
The roadmap for AI-enhanced photonic cryptography is as exciting as it is challenging. Here are potential breakthroughs:
- Quantum-enabled cloud storage: A future where personal and enterprise data is secure against even quantum-level threats.
- AI-driven photonic processors: Devices that utilize photons instead of electrons for unparalleled speed and energy efficiency.
- Widespread quantum internet adoption: Powered by AI to optimize performance and accessibility worldwide.
While challenges like cost and technical complexity persist, the intersection of AI and photonic cryptography has already begun to redefine what’s possible in the cybersecurity landscape.
Conclusion
The convergence of AI and photonic cryptography is nothing short of revolutionary. By leveraging the unique properties of quantum light and the computational power of AI, we’re paving the way for a future where data is secure, no matter the threats ahead.
This transformation, however, demands collaboration across industries, policymakers, and researchers to overcome hurdles and harness the full potential of these technologies. The next era of cybersecurity is quantum, and AI is lighting the way.
FAQs
Is quantum encryption better than classical encryption?
Yes, in terms of security. Classical encryption relies on the computational difficulty of breaking keys (e.g., RSA), which can be compromised by quantum computers. In contrast, quantum encryption, like photonic cryptography, is based on laws of physics, making it virtually unbreakable.
For example, if a hacker tries to eavesdrop on a quantum-encrypted channel, the act of interception itself disrupts the quantum states, immediately signaling a breach.
Can AI and photonic cryptography be integrated into existing networks?
Yes, but integration requires overcoming technical challenges like compatibility and scalability. AI plays a crucial role by enabling hybrid encryption models that allow quantum systems to interact with classical networks seamlessly.
For instance, banks are testing hybrid solutions where AI manages quantum keys for encrypting transactions, while classical systems handle non-sensitive operations. This phased approach ensures smooth adoption without disrupting current infrastructures.
What is quantum internet, and how does AI contribute to it?
Quantum internet is a next-generation communication network using entangled photons for data transmission, ensuring unparalleled security. AI contributes by:
- Optimizing photon routing paths to minimize loss.
- Managing quantum nodes to expand network scalability.
For example, a quantum satellite communication system could use AI to coordinate ground stations worldwide, enabling secure data sharing between continents.
Are there risks in combining AI with quantum cryptography?
One potential risk is the lack of transparency in AI algorithms. If not carefully managed, AI decisions about routing or encryption protocols could inadvertently create vulnerabilities.
Additionally, AI-enhanced quantum tools could be exploited for malicious purposes if they fall into the wrong hands. Establishing clear ethical and regulatory guidelines is critical to mitigating these risks.
How soon can we expect quantum encryption to become mainstream?
Quantum encryption is still in its early stages, but AI is accelerating progress. For example, researchers are using AI to improve quantum error correction, bringing us closer to scalable, reliable systems.
In critical sectors like defense and finance, pilot programs are already underway. Mainstream adoption for consumers might take a decade or more, depending on costs, technical advancements, and global infrastructure readiness.
How does quantum light differ from traditional encryption technologies?
Traditional encryption relies on mathematical algorithms to secure data, such as RSA or AES, which can be broken by quantum computers. In contrast, quantum light encryption uses the physical properties of photons—like polarization and entanglement—to secure information.
For example, in Quantum Key Distribution (QKD), encryption keys are transmitted via photons. If a hacker attempts to intercept them, the quantum state of the photons changes, instantly alerting the system to the breach. This is fundamentally different from classical systems, where attackers might go unnoticed.
Why is AI necessary for scaling quantum cryptography?
Quantum systems are extremely sensitive and complex, making scalability a major challenge. AI handles these complexities by:
- Predicting and correcting errors due to photon loss or environmental noise.
- Automating key distribution across large networks.
For instance, in a multi-node quantum network, AI can dynamically adjust the routes of photons to maintain stable connections and prevent interruptions. Without AI, manually managing these intricate systems would be impractical.
What role does AI play in detecting eavesdropping attempts?
AI excels at analyzing vast amounts of data in real time, making it a powerful tool for identifying suspicious activity in quantum communication systems.
For example:
- AI algorithms monitor changes in photon transmission, such as unexpected noise or altered polarization states.
- Machine learning models are trained to distinguish between natural disturbances and malicious eavesdropping attempts.
This proactive approach means AI can shut down compromised channels instantly, preserving the integrity of the encryption process.
Can AI and photonic cryptography protect against insider threats?
Yes, AI can significantly mitigate insider threats. While photonic cryptography secures data during transmission, AI can monitor access patterns and flag unusual behavior.
For instance:
- If an employee suddenly accesses encrypted files at odd hours or from unfamiliar devices, AI can trigger alerts or block access until verification is completed.
- AI-enabled systems can also manage quantum access controls, ensuring encryption keys are only available to authorized users.
This layered approach enhances overall security, even against internal risks.
Are there any energy efficiency benefits to using AI in photonic cryptography?
Yes, photon-based systems are inherently more energy-efficient than traditional electronic systems because they rely on light rather than electricity for data transmission. AI further optimizes this by:
- Reducing redundant photon transmissions through smart routing algorithms.
- Managing quantum repeaters to minimize energy consumption in long-distance communication.
For example, AI could enable a quantum-secure data center to run on fewer resources by efficiently distributing encryption tasks, lowering both costs and carbon footprint.
What happens if AI fails in a quantum cryptographic system?
If AI malfunctions or is compromised, the quantum system might face operational issues, such as slower encryption processes or reduced ability to detect breaches. However, the underlying quantum principles of photonic cryptography—like the no-cloning theorem and entanglement—still provide a strong security foundation.
For added resilience:
- Backup algorithms can take over temporarily.
- Redundant AI models or manual overrides can restore normal operations.
For instance, in a global financial network, if AI managing QKD fails, fallback protocols ensure secure communication until the issue is resolved.
How does photonic cryptography work with existing cybersecurity tools?
Photonic cryptography doesn’t replace existing tools—it enhances them by adding an unbreakable layer of security. AI helps bridge the gap between quantum systems and traditional networks by:
- Integrating quantum keys with classical encryption methods like TLS.
- Using hybrid systems where classical encryption handles low-risk data, and quantum encryption secures high-risk transmissions.
For example, a hospital might use AI to manage both quantum-secure channels for patient records and classical encryption for routine communications. This hybrid model ensures cost-effective security across all systems.
Is photonic cryptography limited to communication, or can it protect stored data?
Photonic cryptography is primarily used for securing communication, but it can indirectly protect stored data by ensuring that encryption keys are transmitted securely. AI expands its potential by:
- Creating quantum-secure storage systems, where data is encrypted using keys transmitted via QKD.
- Managing access to quantum-secure databases using adaptive authentication methods.
For instance, cloud providers could implement AI-enabled quantum encryption to protect sensitive customer data stored across their servers.
How does AI make quantum cryptography more affordable?
Quantum systems are expensive to develop and maintain, but AI reduces these costs by:
- Automating complex processes like key management and error correction, which lowers the need for specialized human operators.
- Optimizing resource usage, such as balancing load across quantum nodes to avoid overutilization.
For example, small businesses could adopt quantum encryption services powered by AI, benefiting from cutting-edge security without requiring in-house expertise.
Could photonic cryptography ever be compromised?
Theoretically, quantum principles make photonic cryptography unbreakable, but practical systems can be vulnerable to implementation flaws. AI mitigates these risks by:
- Detecting and fixing vulnerabilities in real-time.
- Enhancing resistance to side-channel attacks, where hackers exploit weaknesses in the physical implementation rather than the encryption itself.
For instance, AI could monitor hardware like quantum emitters to ensure they’re operating correctly, preventing attackers from exploiting flaws. While no system is 100% invulnerable, AI and photonic cryptography together offer an unmatched level of security.
Resources
Research Papers and Publications
- “Quantum Key Distribution and Its Applications”
A comprehensive paper covering the principles of QKD and its practical uses. This resource is excellent for understanding the fundamentals of photonic cryptography.
Link: Quantum Key Distribution Paper (arXiv) - “Artificial Intelligence for Quantum Technologies”
Explores how AI accelerates the development of quantum systems, including photonic cryptography.
Publisher: Nature Reviews Physics
Link: Nature Physics AI Quantum Article - “Quantum Cryptography: Theoretical and Practical Perspectives”
This paper discusses the challenges of implementing quantum encryption in real-world applications and how AI is bridging the gap.
Link: Springer Quantum Cryptography
Books and eBooks
- “Quantum Computation and Quantum Information” by Michael A. Nielsen and Isaac L. Chuang
A foundational book that delves into the principles of quantum mechanics and their application to cryptography. - “AI for Quantum Systems: Applications and Algorithms” by Alexei Fedorov
This book provides insights into how AI tools like machine learning and reinforcement learning are applied to quantum systems. - “Photonics and Quantum Cryptography” by Agrawal Govind P.
Covers the use of photons in quantum communications and its security applications, with detailed examples.
Online Courses and Tutorials
- edX: “Quantum Cryptography” by TU Delft
A free course offering an introduction to quantum cryptography, with a focus on QKD.
Link: Quantum Cryptography Course - Coursera: “Quantum Computing Fundamentals” by University of Chicago
While focused on quantum computing, it includes modules on photonic systems and encryption.
Link: Quantum Computing on Coursera - Udemy: “AI and Quantum Technologies: A Beginner’s Guide”
Offers hands-on projects combining AI and quantum encryption.
Organizations and Labs
- Quantum Internet Alliance (QIA)
Focused on building a pan-European quantum internet using advanced photonic technologies. Their website contains research updates and educational resources.
Link: Quantum Internet Alliance - MIT Quantum Photonics Lab
MIT’s research group working on integrating photonics and AI for advanced quantum systems.
Link: MIT Quantum Photonics - Google Quantum AI
Google’s quantum research division regularly publishes updates on quantum cryptography and AI.
Link: Google Quantum AI
Tools and Software
- IBM Quantum Experience
A cloud-based platform that allows users to simulate and run quantum experiments, including cryptographic ones.
Link: IBM Quantum - Qiskit
An open-source quantum computing library with modules for developing and testing quantum cryptography protocols.
Link: Qiskit Library - TensorFlow Quantum
A framework integrating AI and quantum systems, useful for experimenting with AI-enhanced quantum cryptography.
News and Blogs
- Quanta Magazine
Regularly publishes articles on advancements in quantum physics, AI, and cryptography.
Link: Quanta Magazine - The Quantum Daily
Covers industry news, use cases, and expert insights on quantum technologies and their intersection with AI.
Link: The Quantum Daily - AI & Quantum Blog by Microsoft
Focuses on how Microsoft integrates AI with quantum computing and cryptography.
Link: Microsoft AI & Quantum