
How Smart Grids Are Revolutionizing Energy Systems
Smart grids are transforming the way energy is distributed and consumed. These systems rely on advanced technologies like IoT devices, sensors, and real-time data to ensure efficient power delivery.
However, with these improvements come vulnerabilities.
Unlike traditional grids, smart grids are deeply integrated with digital technologies. While this allows for better control and monitoring, it also opens the door for cybercriminals to exploit weaknesses.
The importance of cybersecurity in smart grids cannot be overstated. Our daily lives depend on the uninterrupted flow of electricity. Disruptions from cyberattacks can cause chaos, affecting hospitals, transport, and communication systems. It’s crucial to recognize that smart grids need to be fortified against potential threats.
The Role of IoT Devices in Smart Grids: A Double-Edged Sword
IoT devices are at the heart of smart grid operations. These devices enable real-time data collection, facilitating a more responsive and efficient energy system. But there’s a catch. With thousands of connected devices, the attack surface expands.
Weak points can exist in the form of poorly configured devices, outdated software, or unsecured communication channels. If cybercriminals gain access to any IoT device, they can penetrate deeper into the network.
On top of that, many IoT devices have limited processing power, which means they often lack robust security features. This presents an easy entry point for attackers aiming to disrupt the entire energy supply.
Why Hackers Target Critical Infrastructure
You might wonder, why would hackers target energy systems? The answer lies in the critical role energy plays in everyday life. A successful attack on a smart grid can cause widespread blackouts, economic losses, and even endanger lives.

For cybercriminals, targeting critical infrastructure offers high rewards. In some cases, hackers are motivated by financial gain, demanding ransoms in exchange for halting their attacks. In other cases, attacks are politically or ideologically driven.
Governments and utility companies need to work together to ensure their grids are secure. This means investing in advanced threat detection and response systems to keep hackers at bay.
The Growing Threat of Ransomware in Smart Grids
In recent years, ransomware attacks have skyrocketed. These attacks involve malicious software that locks users out of their systems until a ransom is paid. Unfortunately, smart grids are no exception.
Cybercriminals are increasingly targeting energy providers. Once they’ve infiltrated the system, they can encrypt data or disable key functions, essentially holding the grid hostage.
Ransomware attacks not only disrupt power distribution but also erode trust between consumers and energy providers. When people lose faith in the reliability of their electricity, it can take years to rebuild that confidence. This makes securing smart grids against ransomware a top priority for the energy sector.
The Importance of Endpoint Security in Smart Grids
Every device connected to a smart grid is a potential endpoint. This includes everything from smart meters to communication nodes. With so many endpoints, securing each one becomes a massive challenge.
Endpoint security is about ensuring that every device is properly protected. This might involve using encryption, multi-factor authentication, and constant software updates.

It’s also vital to implement real-time monitoring systems. By continuously tracking network activity, energy companies can detect unusual behavior and respond to threats before they escalate.
To enhance security, some companies are turning to AI-powered solutions. These systems use machine learning to identify anomalies and predict potential vulnerabilities.
Real-Time Monitoring: A Proactive Approach to Cybersecurity
In a world where cyber threats evolve by the minute, real-time monitoring has become a cornerstone of smart grid security. It involves tracking the entire grid’s operations and flagging any unusual activity that could signal a cyberattack.
This approach is essential because cyberattacks on smart grids can happen in seconds. Without proactive monitoring, energy providers risk missing critical warning signs. For example, an attacker could exploit a vulnerability in a single IoT device, quickly spreading malware throughout the system.
By constantly scanning for potential threats, energy companies can detect attacks early and take immediate action. This might include isolating affected areas, deploying patches, or switching to backup systems.
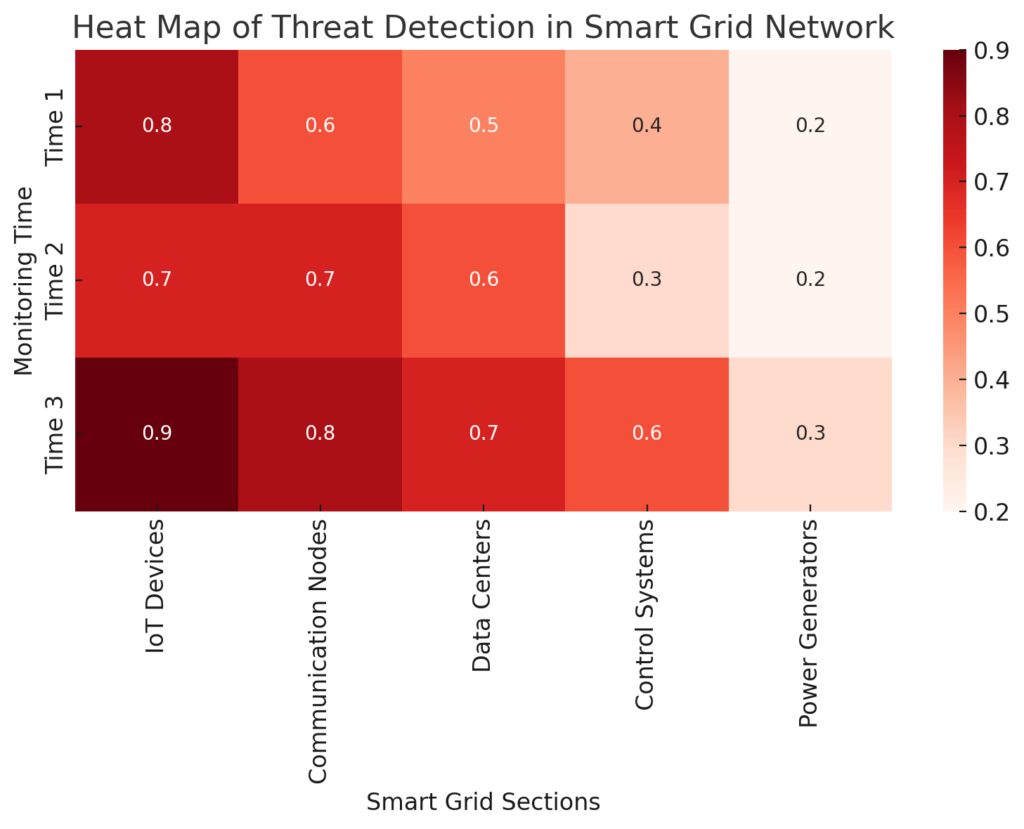
AI-powered monitoring tools are particularly effective in this regard. These systems can analyze vast amounts of data at lightning speed, identifying patterns and anomalies that humans might overlook. As a result, companies can respond to attacks before they cause widespread damage.
The Danger of Distributed Denial of Service (DDoS) Attacks on Smart Grids
One of the most common forms of cyberattacks on smart grids is the Distributed Denial of Service (DDoS) attack. In these attacks, cybercriminals flood a system with traffic, overwhelming it and causing a shutdown.
For smart grids, a DDoS attack could mean halting power distribution to entire regions. This type of disruption is particularly dangerous because it’s often hard to trace back to the original attacker. Worse still, DDoS attacks can serve as distractions while more sophisticated breaches occur elsewhere in the network.
Energy providers need to implement DDoS protection systems that can mitigate these risks. Firewalls, load balancers, and redundancy measures can help maintain grid stability even during an attack.
Ensuring that critical systems remain operational during a DDoS attack can prevent massive economic and societal consequences. In the energy sector, downtime is not an option.
Building Cyber Resilience: The Role of Incident Response Plans
No matter how strong a cybersecurity defense is, there’s always a chance that an attacker could get through. That’s why smart grids need cyber resilience—the ability to recover quickly from a breach.
This starts with having a robust incident response plan in place. When a cyberattack happens, time is of the essence. A well-prepared team should know exactly how to respond, from isolating infected systems to communicating with stakeholders.
Incident response plans should be regularly tested and updated to address the latest threats. Additionally, companies need to establish clear communication protocols. This ensures that everyone, from technicians to company executives, understands their role during an attack.

Cyber resilience also involves investing in backup systems. In the event of a large-scale attack, energy providers need to have alternative power sources ready to minimize disruptions.
The Role of Governments and Regulations in Protecting Smart Grids
Governments play a critical role in protecting smart grids from cyberattacks. By establishing regulatory frameworks and security standards, they can ensure that energy providers prioritize cybersecurity.
In many countries, regulations such as the NERC CIP (North American Electric Reliability Corporation Critical Infrastructure Protection) standards mandate specific security measures for energy companies. These include requirements for physical security, data encryption, and vulnerability assessments.
Additionally, governments often collaborate with the private sector to share information about emerging threats. Through initiatives like public-private partnerships, both sides can work together to develop more effective cybersecurity solutions.
However, regulations alone aren’t enough. Companies must also foster a culture of security, where every employee understands the importance of protecting the grid. Regular training sessions and security drills can go a long way in building awareness and preparedness.

The Future of Cybersecurity in Smart Grids: AI and Machine Learning
As cyber threats become more sophisticated, so too must the solutions used to combat them. Artificial intelligence (AI) and machine learning are at the forefront of this evolution.
These technologies allow energy companies to analyze vast amounts of data in real time, identifying patterns and potential threats that humans might miss. For instance, machine learning algorithms can detect subtle changes in grid behavior, flagging possible attacks before they escalate.
AI-powered systems also excel at automating routine security tasks. This frees up human analysts to focus on more complex issues, while AI handles tasks like patching vulnerabilities or monitoring device activity.
In the future, AI will likely become an integral part of smart grid defense, offering an additional layer of protection against the ever-growing threat of cyberattacks.

Steps to Secure Critical Infrastructure
Conduct Regular Security Audits
One of the most critical steps in protecting smart grids is performing regular security audits. These audits should include a comprehensive review of your entire system—hardware, software, and network configurations.
Security audits can identify vulnerabilities in smart meters, IoT devices, and even the control systems that manage energy distribution. During these audits, you should:
- Review all access points: Ensure that devices and systems are accessible only to authorized personnel.
- Test system integrity: Conduct penetration tests to simulate attacks and determine how well your defenses hold up.
- Check for outdated software: Make sure all devices, especially IoT components, are running the latest firmware and software versions.
An audit isn’t just about checking for weaknesses; it’s also about identifying areas where security measures are performing well and reinforcing them. By routinely testing your systems, you can stay ahead of attackers and proactively patch vulnerabilities before they’re exploited.
Implement Multi-Layered Security (Defense in Depth)
Defense in Depth is a strategy that employs multiple layers of security, creating a series of barriers for an attacker to break through. The idea is to make it as hard as possible for attackers to penetrate your system.
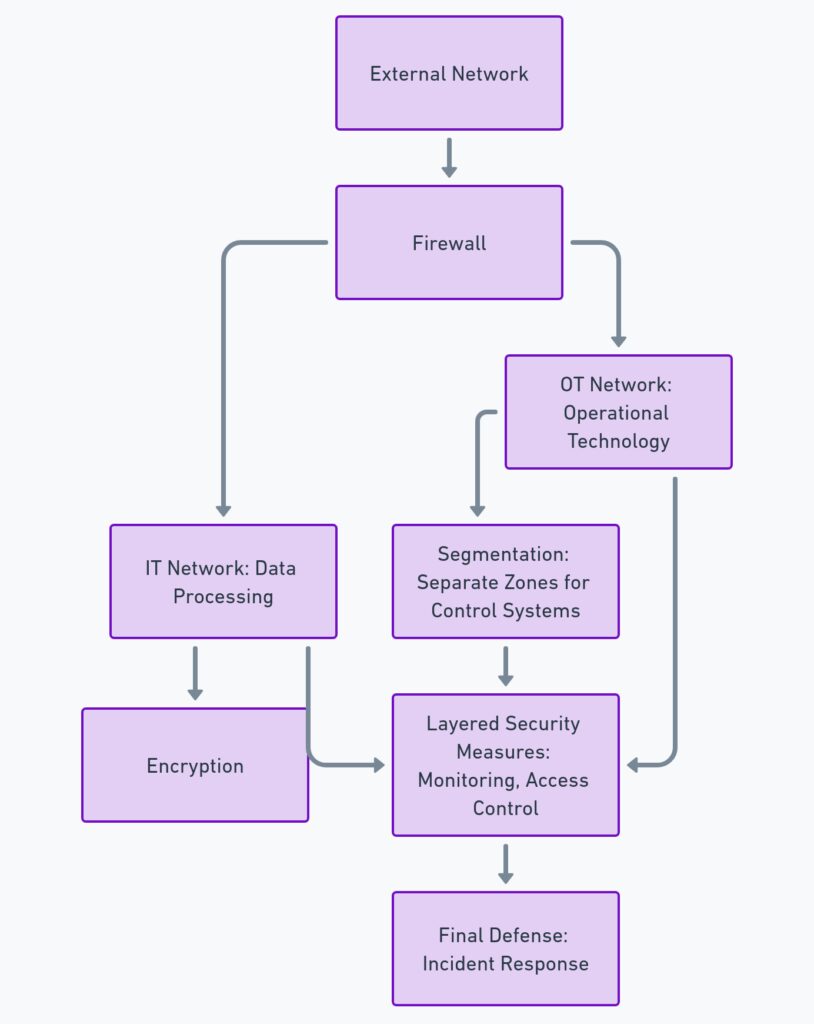
Some key layers of defense to implement in smart grids include:
- Firewalls and Intrusion Detection Systems (IDS): These should be installed at critical points in the network to monitor traffic and block malicious access attempts.
- Encryption: All data transmitted across the smart grid, especially between IoT devices and control centers, should be encrypted. Encryption helps prevent attackers from intercepting or altering communications.
- Network Segmentation: Create separate networks for different parts of your grid. For instance, the operational technology (OT) network that manages grid operations should be isolated from the IT network used for business functions.
- Physical Security: Protect critical components, like substations and control rooms, with physical security measures, including cameras, biometric access controls, and 24/7 monitoring.
Layering these protections adds redundancy and helps ensure that if one security measure fails, another is there to block or mitigate the attack.
Strengthen Endpoint Security and Device Management
Smart grids rely on a vast number of connected devices, including sensors, smart meters, and control systems, all of which serve as potential entry points for attackers. Endpoint security is crucial to protecting each of these devices.
Best practices for endpoint security include:
- Use endpoint protection software: Install security software on all connected devices to monitor for malware, unauthorized access, and abnormal behavior.
- Enforce strong authentication: Require multi-factor authentication (MFA) for users accessing critical devices or control systems. This can involve biometric verification, one-time passwords (OTP), or hardware security tokens.
- Update devices regularly: Ensure that every device connected to the grid, especially IoT components, receives firmware updates and security patches promptly. Neglecting updates can leave your devices vulnerable to exploits.
- Disable unused services: Devices often come with multiple services enabled by default. Disable unnecessary services and protocols to reduce the number of potential entry points for attackers.
Implementing robust device management systems that monitor and control all connected endpoints ensures that no device becomes a weak link in your security chain.
Create an Incident Response Plan and Conduct Regular Drills
Being prepared for an attack is just as important as preventing one. Every energy provider should have a detailed incident response plan that outlines the steps to take in the event of a cyberattack.
Key components of an incident response plan should include:
- Designated response teams: Assign clear roles and responsibilities to team members, including IT personnel, security experts, and communication officers.
- Rapid response protocols: Define the immediate steps that need to be taken, such as isolating compromised devices, switching to backup systems, and informing stakeholders.
- Communication strategy: Ensure there’s a plan for communicating with the public, government agencies, and other stakeholders if an attack occurs.
Incident response plans should be tested regularly through simulated cyberattacks or drills. This ensures that your team knows exactly how to respond and can practice working under pressure.
Partner with Threat Intelligence Providers
Staying informed about the latest cyber threats is essential. Cybercriminals are constantly evolving their tactics, which means the threat landscape is always changing. Partnering with threat intelligence providers can help you stay ahead of new and emerging threats.
Threat intelligence providers offer services like:
- Real-time threat alerts: Receive notifications about vulnerabilities being exploited in the energy sector or broader critical infrastructure.
- Malware analysis: Access detailed reports on the latest malware, ransomware, and attack strategies targeting smart grids.
- Incident tracking: Understand how similar organizations are being attacked and learn from their experiences to strengthen your defenses.
By integrating threat intelligence into your cybersecurity strategy, you can adjust your defenses to protect against specific, evolving threats targeting energy systems.
Educate and Train Employees on Cybersecurity Best Practices
Human error is often the weakest link in cybersecurity. Whether it’s opening a phishing email or using a weak password, employee mistakes can lead to breaches. To counter this, provide regular cybersecurity training to all employees.
Effective training programs should cover:
- Phishing awareness: Teach employees how to recognize and report suspicious emails, links, or attachments.
- Password management: Enforce strong password policies and encourage the use of password managers.
- Incident reporting: Ensure all employees understand how to report any unusual activity or potential security incidents immediately.
- Secure device use: For those working remotely or accessing smart grid systems via mobile devices, teach best practices for securing connections (e.g., using VPNs).
Training should be ongoing, with regular refreshers to keep employees up to date on the latest threats and best practices.
By implementing these practical steps, energy providers can dramatically reduce their vulnerability to cyberattacks and improve the resilience of their smart grids.
Helpful Resources for Enhancing Cybersecurity in Smart Grids
1. National Institute of Standards and Technology (NIST) Cybersecurity Framework
- The NIST Cybersecurity Framework provides guidelines, standards, and practices to help organizations manage and reduce cybersecurity risks. This resource is particularly useful for critical infrastructure sectors like energy.
- Visit the NIST Cybersecurity Framework to learn how to implement risk management strategies tailored to smart grids.
2. North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) Standards
- The NERC CIP Standards are a set of regulations designed specifically to protect the reliability of the electric grid. They provide guidelines for physical and cybersecurity in energy systems.
3. U.S. Department of Energy (DOE) Office of Cybersecurity, Energy Security, and Emergency Response (CESER)
- The DOE CESER office offers cybersecurity resources, tools, and training tailored to the energy sector. They also provide threat intelligence and support for grid resilience.
- Access their resources at the DOE CESER website.
4. European Union Agency for Cybersecurity (ENISA)
- ENISA offers insights and best practices for improving the cybersecurity of critical infrastructure, including smart grids. They publish reports on current trends, cybersecurity challenges, and solutions for the energy sector.
- Explore ENISA’s publications and guides on smart grid security here.
5. SANS Institute: Cybersecurity Training and Certifications
- The SANS Institute offers in-depth cybersecurity training, including courses specific to industrial control systems (ICS) and smart grids. Their ICS Security Summit is a great way to learn from experts in the field.
- Learn more about their training programs here.