Software-Defined Networking (SDN) is transforming how networks are designed, managed, and secured. By decoupling the control plane from the data plane, SDNs allow for more flexible and programmable network management. However, this very flexibility introduces vulnerabilities, particularly in the form of Distributed Denial of Service (DDoS) attacks. To counter these threats, a sophisticated approach known as hybrid detection has emerged as a critical tool in the arsenal of network security. Let’s explore how hybrid detection operates, its intricacies, and its broader implications for securing SDNs.
The Anatomy of DDoS Attacks in SDNs
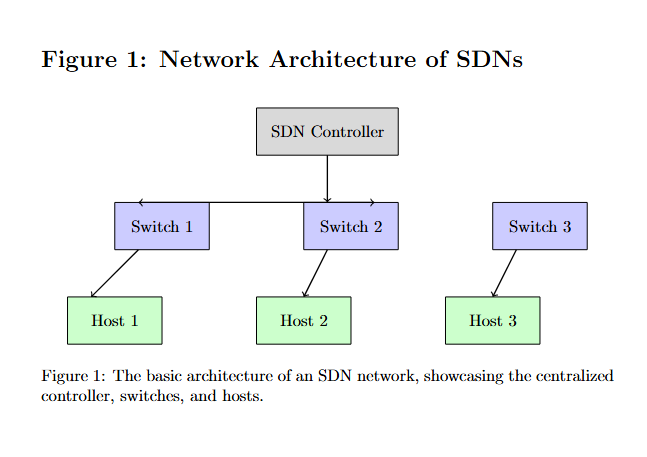
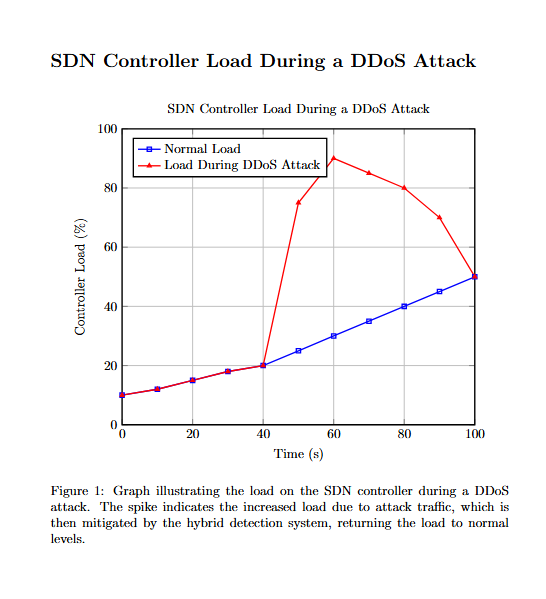
DDoS attacks are a significant concern for any network, but in SDNs, the stakes are higher. The centralized control plane in SDNs, which provides a global view of the network, is both a strength and a vulnerability. Attackers target this central control with overwhelming traffic, attempting to exhaust the resources of the controller, thereby causing network-wide disruptions.
A DDoS attack typically involves multiple compromised systems (often part of a botnet) flooding a target—such as an SDN controller—with excessive traffic. This can lead to two primary outcomes:
- Resource Exhaustion: The attack consumes the controller’s CPU, memory, and bandwidth, leading to degraded performance or complete failure.
- Control Plane Overload: Overwhelming the control plane disrupts the flow of control messages, causing widespread outages across the data plane.
Understanding these dynamics is crucial because the effectiveness of any DDoS mitigation strategy in an SDN hinges on protecting the control plane while maintaining the integrity and performance of the data plane.
Traditional Detection Approaches: Limitations and Challenges
Historically, DDoS detection has relied on signature-based and anomaly-based methods.
- Signature-Based Detection: This approach compares incoming traffic against a database of known attack patterns (signatures). While this method is effective at identifying recognized threats, it struggles with detecting new or modified attacks, especially those that evolve rapidly.
- Anomaly-Based Detection: In contrast, anomaly-based detection focuses on identifying deviations from normal traffic patterns. By establishing a baseline of typical network behavior, this method can potentially detect new types of attacks. However, it often suffers from high false positive rates, as legitimate but unusual traffic can trigger alerts.
Each of these methods has its strengths, but neither is foolproof. In an SDN environment, where the control plane is a critical target, relying on a single detection method is insufficient. This is where hybrid detection comes into play.
Hybrid Detection: A Synergistic Approach
Hybrid detection mechanisms combine the precision of signature-based methods with the adaptability of anomaly-based detection. This synergy is particularly effective in the dynamic and programmable environment of SDNs, where traffic patterns can change quickly and unpredictably.
How Hybrid Detection Works:
- Baseline Establishment: The system begins by establishing a baseline of normal traffic patterns using anomaly-based detection. This baseline is continually updated to reflect changes in network behavior.
- Signature Matching: Simultaneously, the system scans incoming traffic against a database of known DDoS attack signatures. Traffic that matches these signatures is flagged and mitigated immediately.
- Anomaly Detection: Traffic that does not match known signatures but deviates significantly from the baseline is subjected to further scrutiny. Advanced algorithms assess the likelihood of this traffic being part of a DDoS attack.
- Adaptive Response: The hybrid system can dynamically adjust its detection parameters based on the evolving threat landscape. For instance, if a new type of DDoS attack is detected, the system can update its signature database and refine its anomaly detection algorithms in real-time.
This multi-layered approach ensures that the network is protected against both known and unknown threats, minimizing the risk of false positives and false negatives.
Technical Architecture of Hybrid Detection in SDNs
The implementation of hybrid detection in SDNs requires a sophisticated technical architecture, typically involving the following components:
- Centralized Controller: The SDN controller plays a crucial role in hybrid detection. It collects and analyzes traffic data from across the network, applying both signature-based and anomaly-based detection algorithms.
- Distributed Agents: To reduce the processing load on the central controller and ensure timely detection, hybrid detection systems often employ distributed agents. These agents are deployed at various points in the network, such as switches and routers, where they perform preliminary analysis and report findings to the central controller.
- Real-Time Analytics: A key feature of hybrid detection systems is their ability to perform real-time analytics on traffic data. This requires high-speed processing capabilities and advanced algorithms that can quickly differentiate between legitimate traffic spikes and potential DDoS attacks.
- Machine Learning Integration: To enhance detection accuracy and adaptability, many hybrid detection systems incorporate machine learning models. These models can learn from past incidents, improving the system’s ability to detect new types of attacks over time.
Advantages of Hybrid Detection: Beyond Basic Security
The benefits of hybrid detection in SDNs extend beyond simple threat mitigation. Here’s how it enhances the overall security posture of SDNs:
- Comprehensive Coverage: By combining multiple detection methods, hybrid systems offer broader coverage against a wider range of threats, including both volumetric attacks (which flood the network with traffic) and application-layer attacks (which target specific services).
- Reduced False Positives: One of the most significant challenges in anomaly-based detection is the high rate of false positives. Hybrid systems mitigate this by cross-referencing anomalous traffic with known signatures, reducing the likelihood of legitimate traffic being misclassified as malicious.
- Scalability: As SDNs scale, so too does the threat landscape. Hybrid detection systems are designed to scale alongside the network, maintaining their effectiveness even as the network grows in size and complexity.
- Resilience and Adaptability: The dynamic nature of hybrid detection allows it to adapt to evolving threats. By continually updating its detection parameters and integrating new signatures, the system remains resilient against the latest DDoS tactics.
Potential Challenges and Mitigation Strategies
While hybrid detection offers numerous advantages, it is not without challenges:
- Computational Overhead: The combination of multiple detection methods requires significant computational resources. This can strain the SDN controller and potentially slow down network operations. To mitigate this, many systems offload part of the detection process to distributed agents or use specialized hardware accelerators.
- Complexity in Implementation: Implementing hybrid detection in an SDN environment is complex, requiring a deep integration between the detection mechanisms and the SDN controller. Organizations must ensure they have the necessary expertise and infrastructure to support this integration.
- Evasion Techniques: As attackers become more sophisticated, they may develop methods to evade hybrid detection systems, such as by mimicking legitimate traffic patterns. To counter this, hybrid detection systems must continuously evolve, incorporating the latest threat intelligence and machine learning models.
The Future of Hybrid Detection in SDNs
The evolution of hybrid detection in SDNs is closely tied to advances in machine learning and artificial intelligence. Future systems are likely to incorporate more advanced AI models that can not only detect but also predict potential DDoS attacks. These models will be capable of analyzing vast amounts of traffic data in real-time, identifying subtle patterns that may indicate an impending attack.
Moreover, as SDNs become more integrated with cloud environments and edge computing, hybrid detection systems will need to evolve to protect these distributed architectures. This will likely involve the development of more decentralized detection mechanisms that can operate effectively across diverse and geographically dispersed networks.
Conclusion: Reinforcing the Future of Network Security
As SDNs become increasingly integral to modern network infrastructures, the need for robust and adaptive security measures grows ever more critical. Hybrid detection mechanisms represent a significant advancement in the ongoing battle against DDoS attacks, offering a powerful and flexible solution that combines the best of both signature-based and anomaly-based detection.
The future of network security lies in the continued development and refinement of these systems, ensuring that as threats evolve, so too does our ability to counter them. By embracing hybrid detection, organizations can not only protect their SDNs but also pave the way for a more secure and resilient digital future.
Here are some scholarly references that might be relevant to this topic:
- Wang, Y., Su, Y., & Jin, H. (2018). “A Hybrid Anomaly Detection Framework in Software-Defined Networks.” IEEE Communications Magazine, 56(9), 178-183.
- This paper discusses a hybrid detection framework that combines both signature-based and anomaly-based methods to enhance the security of SDNs against DDoS attacks.
- Sahay, R., Wolthusen, S. D., & Dacier, M. (2017). “Towards Autonomous and Adaptive SDN-Based DDoS Mitigation.” Proceedings of the 2017 Workshop on Adaptive and Reflective Middleware.
- This work explores the potential of autonomous and adaptive systems in SDNs for mitigating DDoS attacks using hybrid detection techniques.
- Wang, P., & Zheng, X. (2018). “An Effective Hybrid Approach for DDoS Detection in SDN.” Journal of Network and Computer Applications, 95, 153-161.
- The paper presents a hybrid detection mechanism combining machine learning and statistical methods to improve DDoS attack detection in SDNs.
- Liu, Z., Zhang, G., Li, Y., & Huang, T. (2020). “Hybrid Detection of DDoS Attacks in Software-Defined Networks Using Long Short-Term Memory.” IEEE Access, 8, 123576-123588.
- This paper introduces a hybrid detection approach that integrates deep learning techniques, specifically LSTM, for more accurate DDoS detection in SDNs.
Here are some resources where you can explore further information on SDN controller load, DDoS attacks in SDNs, and hybrid detection mechanisms:
- Books and Journals:
- “Software Defined Networks: A Comprehensive Approach” by Paul Goransson, Chuck Black, and Timothy Culver: This book offers a thorough introduction to SDNs, including architecture, security challenges, and DDoS attack mitigation.
- “Software Defined Networking (SDN): Anatomy of OpenFlow Volume I” by Doug Marschke and Jeff Doyle: A detailed exploration of SDN principles, focusing on the OpenFlow protocol and its implications for network security.
- IEEE Xplore Digital Library: Search for papers on “SDN security,” “DDoS mitigation in SDNs,” and “hybrid detection mechanisms” for access to cutting-edge research articles and conference papers.
- “A Survey of DDoS Attack Detection and Mitigation in Software Defined Network” by Ahmad Alsmadi and Dewei Dai: A review article published in the Journal of Network and Computer Applications that surveys different methods for detecting and mitigating DDoS attacks in SDNs.
- Online Courses and Tutorials:
- Coursera’s “Software Defined Networking”: Offered by Princeton University, this course covers the basics of SDNs, including security concerns such as DDoS attacks.
- edX’s “Introduction to SDN and OpenFlow”: Provides a practical introduction to SDNs and security challenges associated with them.
- Udemy’s “Mastering Software-Defined Networking (SDN)”: A course that delves into SDN technologies, architectures, and security.
- Research Papers and Articles:
- “Hybrid Detection of DDoS Attacks in Software-Defined Networks Using Machine Learning”: This research paper discusses a hybrid detection approach using machine learning to identify and mitigate DDoS attacks in SDNs. Available on IEEE Xplore.
- “Security Challenges and Opportunities for Software-Defined Networks”: Published in the IEEE Communications Magazine, this article explores the security issues in SDNs and provides insights into possible solutions.
- “An Effective Hybrid Approach for DDoS Detection in SDN” by Wang and Zheng: Found in the Journal of Network and Computer Applications, this paper details a hybrid approach for DDoS detection in SDNs.
- Web Resources and Blogs:
- SDxCentral (https://www.sdxcentral.com/): A comprehensive resource for all things SDN, including news, tutorials, and articles on security challenges like DDoS.
- Open Networking Foundation (ONF) (https://opennetworking.org/): The ONF provides resources, whitepapers, and guidelines on SDN technologies and their security implications.
- Network World (https://www.networkworld.com/): Offers articles and analysis on SDN developments, including security issues such as DDoS attacks.
- Conferences and Workshops:
- ACM SIGCOMM: A leading conference on communications and networking where research on SDN security is often presented.
- IEEE International Conference on Communications (ICC): Another key venue for academic presentations on SDN security, including DDoS mitigation strategies.
- NDSS Symposium (Network and Distributed System Security Symposium): Focuses on the latest in network security, including emerging threats to SDNs and novel detection techniques.