
Homomorphic encryption (HE) allows computations on encrypted data without needing decryption, offering unparalleled privacy and security. While promising, HE is difficult to scale, especially for real-world applications.
This article breaks down the major challenges hindering the adoption of homomorphic encryption on a broader scale.
Understanding Homomorphic Encryption
What is Homomorphic Encryption?
Homomorphic encryption enables performing operations on ciphertexts that translate directly into operations on plaintexts. For example, adding two encrypted numbers results in an encrypted sum, which, when decrypted, yields the same result as if the numbers were added directly.
This encryption is unique in that it allows computation on data without revealing it, making it valuable in privacy-sensitive fields like healthcare, finance, and cloud computing.
Types of Homomorphic Encryption
Homomorphic encryption includes several types:
- Partially Homomorphic Encryption (PHE): Supports a single operation (addition or multiplication) indefinitely.
- Somewhat Homomorphic Encryption (SHE): Supports both operations, but only a limited number of times.
- Fully Homomorphic Encryption (FHE): Allows both addition and multiplication, enabling any arbitrary computation.
FHE is the gold standard for HE but is also the most challenging to scale due to its computational demands.
Partially Homomorphic Encryption (PHE): Supports single operations.
Somewhat Homomorphic Encryption (SHE): Allows limited operations.
Fully Homomorphic Encryption (FHE): Supports all operations.

High Computational Overhead
Why Does Homomorphic Encryption Demand So Much Power?
Homomorphic encryption requires substantial computational power due to its complex encryption schemes. FHE especially involves intricate mathematical operations, making it several orders of magnitude slower than standard encryption techniques like AES.
For instance, multiplying two encrypted numbers under FHE is not just a simple multiplication; it involves additional steps that may take hundreds or even thousands of times longer than plaintext computation.
Impact on Real-World Applications
This computational burden makes HE almost impractical for applications needing real-time data processing. Imagine a financial system needing split-second transactions: the delay introduced by FHE could make this impossible. Without substantial optimization, scaling HE to such applications remains difficult.
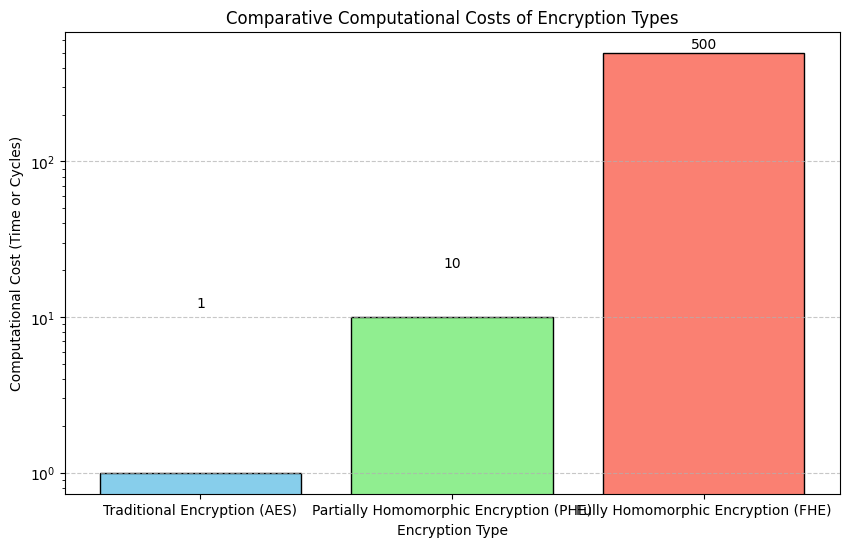
Traditional Encryption (AES) has a low computational cost.
Partially Homomorphic Encryption (PHE) requires more resources.
Fully Homomorphic Encryption (FHE) incurs a significantly higher computational cost, reflected by its much taller bar.
Current Approaches to Addressing Computational Overhead
Researchers are exploring several approaches to make HE more computationally feasible:
- Algorithmic Optimizations: Improving the efficiency of existing algorithms.
- Hardware Acceleration: Leveraging specialized processors, such as GPUs or FPGAs, to handle heavy computations more efficiently.
- Hybrid Schemes: Combining HE with other cryptographic methods to balance performance and security.

Memory and Storage Constraints
Why Does Homomorphic Encryption Require So Much Memory?
HE encrypts data in a way that significantly increases its size, often by orders of magnitude. This “ciphertext expansion” results in massive data sizes that are impractical for storage or processing.
For example, in medical research, encrypted patient data could be too large to store or manage effectively, limiting the feasibility of HE in such data-intensive fields.
Challenges in Data-Intensive Applications
Applications like machine learning or big data analytics rely on processing large datasets. With HE, data size bloat becomes a significant barrier to scaling. The memory and storage requirements escalate quickly, outstripping the capacities of many existing systems.
Potential Solutions for Memory Constraints
To address these challenges, researchers are working on:
- Compression Techniques: Reducing data size without compromising encryption.
- Efficient Data Structures: Designing data structures that minimize storage requirements while retaining encrypted properties.
- Selective Encryption: Encrypting only critical data fields, leaving less sensitive data in plaintext.
Complexity in Developing Homomorphic Encryption Algorithms
Why Are Homomorphic Encryption Algorithms So Complex?
Homomorphic encryption algorithms are based on advanced mathematical concepts, including lattice-based cryptography and modular arithmetic. This complexity makes it difficult for developers to implement HE schemes correctly without specialized training.
Moreover, the need for advanced mathematical knowledge creates a steep learning curve, meaning only a handful of experts have the skills to develop and optimize HE solutions.
Impact on Development and Adoption
The limited pool of experts and the complexity of HE algorithms can slow down development cycles. Many organizations might hesitate to adopt HE simply because they lack the in-house expertise needed to deploy and maintain it.
Efforts to Simplify Development
To make HE more accessible, several efforts are underway:
- Software Libraries: Open-source libraries like Microsoft SEAL and IBM HELib offer standardized implementations, helping developers use HE without deep cryptographic expertise.
- Educational Resources: Increased training and educational resources aim to build a more robust knowledge base in the field.
Lack of Standardization and Interoperability
Why is Standardization Important in Homomorphic Encryption?
Standards ensure consistency, interoperability, and security across systems. However, HE is still relatively new, and the field lacks universal standards that guide its implementation and integration across diverse applications.
Without a standard framework, developers have to rely on custom implementations, which can vary widely in efficiency and security. This lack of standardization complicates HE’s integration into larger, more complex systems.
Challenges in Interoperability
Organizations using HE in cloud computing or cross-industry data sharing face interoperability issues, especially when integrating with non-HE systems. A healthcare provider, for instance, might struggle to share encrypted data securely and seamlessly with a cloud provider due to differing HE implementations.
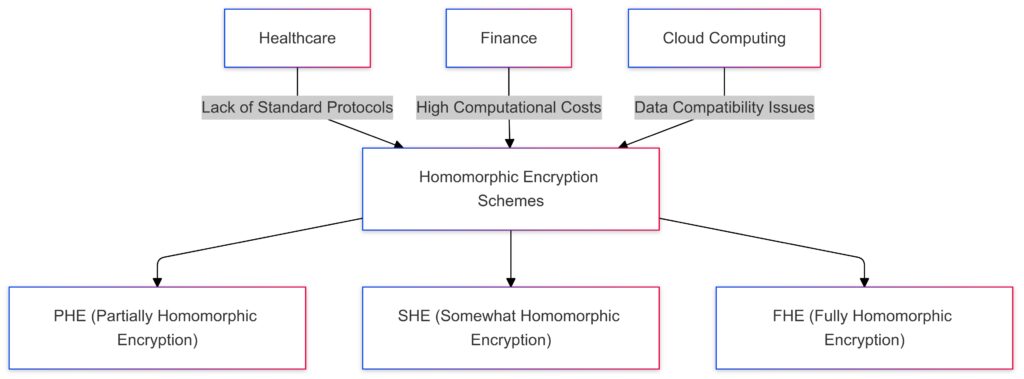
Healthcare encounters a lack of standard protocols.
Finance faces high computational costs.
Cloud Computing struggles with data compatibility issues.
Each industry connects to various homomorphic encryption schemes (PHE, SHE, FHE), highlighting specific interoperability challenges.
Steps Toward Standardization
Several organizations, including the HomomorphicEncryption.org, are working toward standardization by developing:
- Common Protocols: Guidelines for secure, interoperable HE implementations.
- Performance Benchmarks: Establishing performance standards to ensure practical usability.
- Compliance Frameworks: Ensuring implementations meet privacy laws and industry standards.
Network Latency and Bandwidth Limitations
How Network Latency Affects Homomorphic Encryption
Since HE encrypts data into much larger formats, transmitting this encrypted data over networks can be slow and inefficient. For cloud-based applications, this added network latency is a serious concern, as data needs to travel between the user’s device and the cloud servers multiple times for processing.
When the ciphertext size increases, it can lead to significant delays, impacting applications that require low-latency interactions, such as online banking or real-time healthcare monitoring. Imagine if a healthcare provider couldn’t access critical patient data quickly enough due to latency caused by large HE files; this could have serious consequences.
Bandwidth Requirements for Large Encrypted Files
Homomorphic encryption also demands higher bandwidth due to the expanded data size. In applications where large datasets are processed, such as genomics or video analytics, network bandwidth could quickly become a bottleneck, especially in regions with slower internet connections.
Potential Solutions to Minimize Latency and Bandwidth Issues
To address these challenges, researchers are working on techniques such as:
- Edge Computing: By performing computations closer to the data source, edge computing can reduce latency and lessen the data load on networks.
- Data Segmentation: Breaking down data into smaller segments that can be encrypted and processed independently can optimize transmission and processing times.
- Bandwidth-Efficient Protocols: Developing new protocols that reduce the amount of data exchanged between servers without compromising security.
User Experience and Usability Challenges

Why Is Homomorphic Encryption Difficult for End Users?
HE’s complexity doesn’t just affect developers; it impacts end-users too. For example, if HE is used to secure a financial application, it might introduce slower response times, affecting the app’s usability. Users might become frustrated with delays, especially if they aren’t aware of the security benefits HE provides.
Additionally, integrating HE into existing applications can lead to significant changes in data flow, impacting user experience. Unlike traditional encryption, HE often involves more steps to encrypt, compute, and decrypt data, creating additional friction in applications that require simplicity and speed.
Challenges in Making HE User-Friendly
Making homomorphic encryption user-friendly while retaining its security advantages remains a tough task. Even minor delays or added steps can reduce the practicality of HE, especially in consumer-facing applications where ease of use is essential.
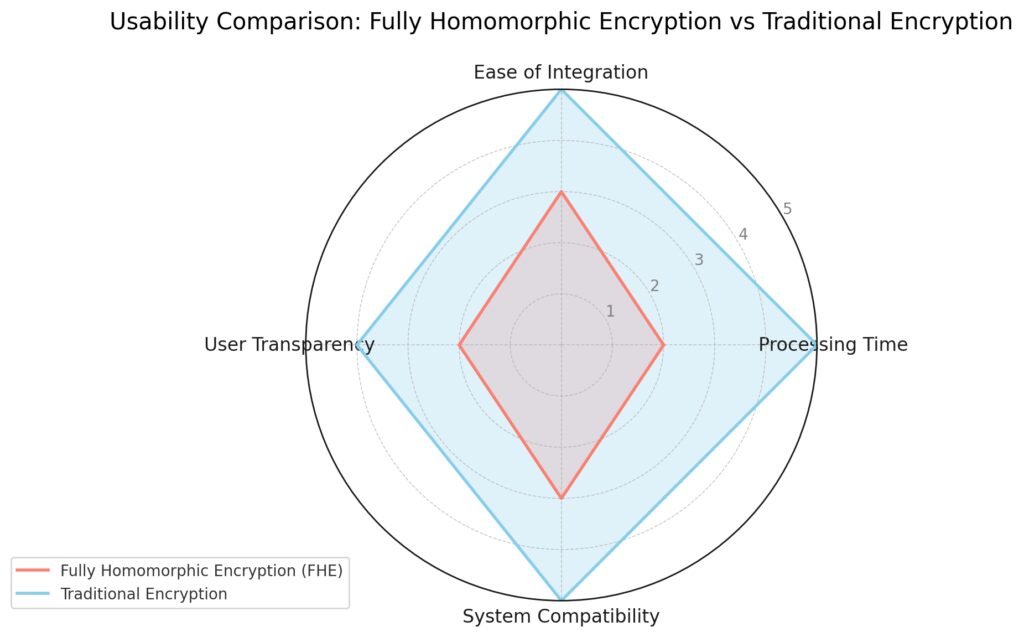
Traditional Encryption scores higher across all categories, showing its ease of use, faster processing time, higher compatibility, and user transparency.
FHE shows limitations in each area, particularly in Processing Time and Ease of Integration due to its complex computations and emerging infrastructure.
This visualization highlights the current usability challenges facing FHE compared to traditional encryption methods.
Strategies to Enhance Usability
To make HE more usable, developers are experimenting with:
- Transparent Encryption: Ensuring that HE is embedded in the backend, making it invisible to the user, so it doesn’t disrupt user workflows.
- Optimized User Interfaces: Creating interfaces that notify users of security benefits without confusing them with complex technical details.
- User Education: Providing education about the importance of privacy-preserving technologies, which can help users understand and accept the slight usability trade-offs HE may bring.
Legal and Regulatory Challenges
How Do Privacy Laws Impact Homomorphic Encryption?
HE was developed with privacy in mind, yet it’s still affected by privacy regulations. For instance, laws like GDPR and HIPAA impose strict requirements for how personal data can be processed and shared. Homomorphic encryption aligns well with these regulations because it allows for secure data processing without decryption. However, navigating these laws can still be challenging, especially since they require transparency and control over data handling.
Furthermore, regulators are still catching up with the technicalities of HE. The lack of legal clarity around emerging encryption methods can make organizations hesitant to adopt HE due to fears of non-compliance.
Jurisdictional Challenges with Encrypted Data Processing
In cross-border applications, such as global financial transactions, encrypted data may travel across multiple jurisdictions. Each jurisdiction has its own set of data protection laws, and HE’s complexity could create legal challenges if these regulations conflict.
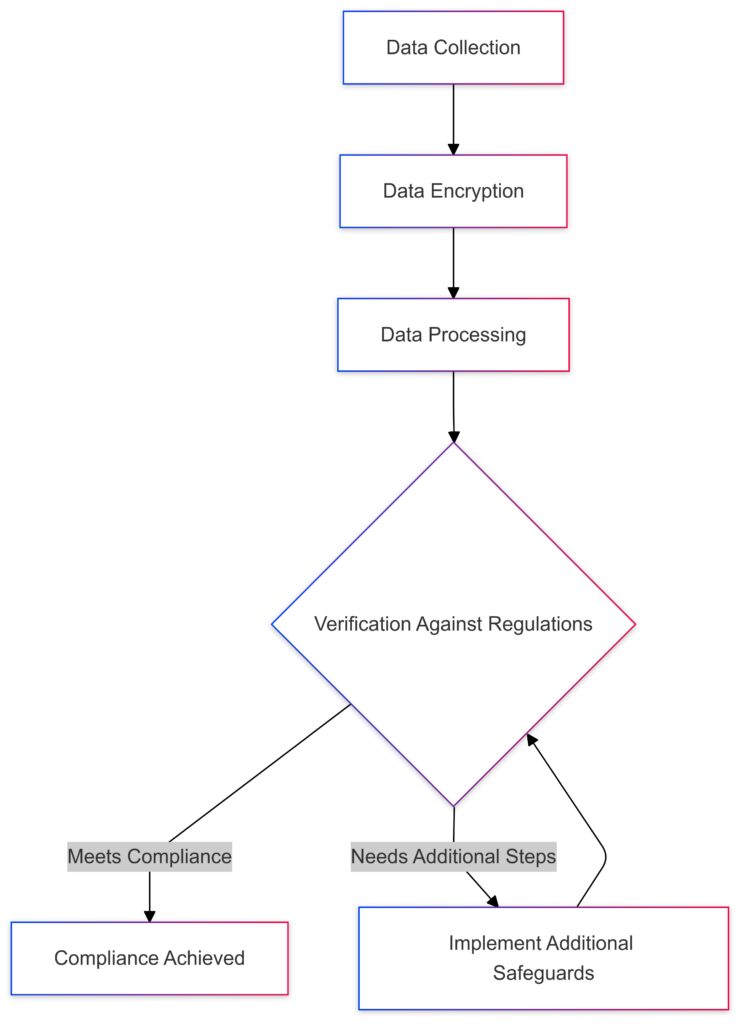
Data Collection starts the process.
Data Encryption secures the data.
Data Processing follows, with encrypted data.
Verification Against Regulations (e.g., GDPR, HIPAA) checks compliance.
If the data meets compliance standards, the process is complete. If not, Additional Safeguards are implemented before re-verifying.
Efforts to Address Legal and Regulatory Challenges
To help HE adoption in regulated industries, several steps are being taken:
- Developing Compliance Standards: Standards organizations are working on guidelines to make HE compliant with global data privacy laws.
- Legal Collaboration: Cryptography experts are collaborating with regulatory bodies to create frameworks that protect data without stifling innovation.
- Documentation and Transparency: Clear documentation of how HE meets regulatory requirements can help organizations demonstrate compliance more effectively.
Limited Industry Adoption and Awareness
Why Is Homomorphic Encryption Adoption Limited?
Despite HE’s advantages, its adoption remains limited. For many industries, HE is still a niche technology, primarily used by research institutions and select tech companies. Many organizations are unaware of HE’s potential benefits, or they assume it’s too complex and expensive to implement.
Additionally, some industries are hesitant to invest in HE due to a lack of real-world use cases. Without concrete examples of HE’s value, organizations may choose simpler, more established encryption methods, even if they don’t offer the same level of privacy.
Challenges with Industry Support and Investment
Limited awareness and adoption create a cycle where there’s less investment in developing HE, which in turn slows down the creation of scalable, accessible solutions. Many companies might also be wary of adopting a technology that isn’t yet standard practice in their field.
Initiatives to Increase Awareness and Adoption
Increasing HE’s presence in the industry requires a combination of education, innovation, and partnership:
- Pilot Programs: Demonstrating HE’s capabilities through pilot projects in industries like healthcare, finance, and e-commerce can showcase its benefits.
- Industry Partnerships: Collaborations between tech companies, research institutions, and industry leaders can drive HE’s adoption in real-world applications.
- Public Awareness Campaigns: Educating the public about the importance of data privacy and how HE can protect it can generate interest and support for the technology.
Scaling homomorphic encryption for real-world applications is no easy feat, with obstacles ranging from computational inefficiency and legal complexity to limited industry support. However, as awareness grows and technology advances, HE could become a cornerstone of data privacy in an increasingly digital world.
Cost and Resource Constraints
Why Is Homomorphic Encryption Expensive to Implement?
The technical demands of homomorphic encryption come with high costs. The computational overhead, memory needs, and bandwidth requirements drive up expenses, particularly for fully homomorphic encryption (FHE). For organizations, this translates to higher costs for cloud storage, specialized hardware, and energy consumption to maintain HE systems.
For instance, a healthcare provider aiming to implement FHE for sensitive patient data might face considerable expenses for the additional storage and processing power. For many businesses, especially small to medium-sized enterprises, these costs can be prohibitive, making it hard to justify investing in homomorphic encryption without clear returns.
Challenges in Budget Allocation
Even when organizations see the potential benefits of HE, they may struggle with budget allocation. Since other, less costly encryption methods already offer sufficient security for many purposes, HE might seem like an unnecessary expense. In sectors with tight budgets, like public services, these costs can be a significant barrier.
Innovations Aiming to Reduce Costs
To help make HE more affordable, researchers and companies are exploring:
- Hardware Optimization: Developing hardware that’s optimized specifically for homomorphic encryption could reduce costs by improving efficiency.
- Cloud-Based HE Services: Cloud providers offering HE as a service could allow organizations to access HE’s benefits without the need for extensive in-house resources.
- Algorithmic Improvements: Streamlining HE algorithms to reduce processing time and memory needs could cut operational costs, making HE a more financially viable option.
Conclusion: The Future of Homomorphic Encryption in Real-World Applications
Homomorphic encryption holds transformative potential across industries, promising enhanced privacy and security for sensitive data. However, significant obstacles, including high computational costs, storage and bandwidth challenges, and limited industry adoption, have made large-scale implementation a considerable challenge.
Advancements in algorithm efficiency, hardware acceleration, and legal frameworks are helping pave the way toward more practical, cost-effective solutions. With increased awareness, research, and support, homomorphic encryption could eventually become a staple in industries where data privacy and security are paramount. While challenges remain, the future looks promising for HE, as it continues to evolve toward feasible, real-world applications.
FAQs
How does homomorphic encryption differ from traditional encryption?
Unlike traditional encryption, which requires data to be decrypted before computation, HE allows operations directly on encrypted data. This unique feature means that data can stay secure and private even while being processed. However, this added functionality also introduces complexity and computational overhead, making HE slower and more resource-intensive than traditional methods.
Is homomorphic encryption secure against cyber threats?
Yes, homomorphic encryption is considered highly secure. Because data remains encrypted during processing, it reduces exposure to cyber threats and data breaches. Even if hackers intercept the data, they would encounter encrypted information that’s essentially unusable without the decryption key. However, like all encryption, HE must be implemented carefully to avoid vulnerabilities.
Can homomorphic encryption be used in real-time applications?
Currently, HE is not ideal for most real-time applications because of its computational delays and data bloat. Real-time systems, like financial trading platforms or emergency healthcare systems, require quick processing speeds that HE struggles to meet. However, research into algorithmic optimizations and hardware accelerations could help HE support real-time applications in the future.
Are there industries already using homomorphic encryption?
Yes, several industries have started experimenting with homomorphic encryption. The healthcare and financial sectors have shown particular interest due to the need for high levels of data security and privacy. Some cloud providers also explore HE as a way to protect user data while providing cloud-based services. However, full-scale adoption remains limited due to scalability issues and high costs.
Is homomorphic encryption compliant with data privacy regulations?
Homomorphic encryption aligns well with data privacy laws like GDPR and HIPAA because it allows data to remain encrypted even during processing. This feature helps companies process personal data while adhering to strict privacy requirements. However, as homomorphic encryption is still an emerging technology, organizations should consult with legal experts to ensure full regulatory compliance.
What are the future prospects for homomorphic encryption?
The future for homomorphic encryption looks promising, especially as research and development continue to tackle current challenges. With improvements in algorithm efficiency, standardization, and hardware optimization, HE could become more accessible and affordable, enabling wider adoption. As the demand for privacy-preserving technologies grows, HE could play a critical role in securing data in an increasingly digital world.
What types of homomorphic encryption exist?
There are three main types of homomorphic encryption:
- Partially Homomorphic Encryption (PHE): Supports one operation, either addition or multiplication, without limit. It’s faster but limited in functionality.
- Somewhat Homomorphic Encryption (SHE): Allows both addition and multiplication but only for a limited number of operations before requiring decryption.
- Fully Homomorphic Encryption (FHE): The most powerful type, supporting unlimited addition and multiplication operations, enabling complex computations on encrypted data. FHE is the focus of most research but is also the most difficult to scale due to its computational demands.
Why is fully homomorphic encryption (FHE) considered the “gold standard”?
FHE is seen as the “gold standard” because it allows any computation on encrypted data, regardless of complexity. Unlike PHE or SHE, which are limited to specific or fewer operations, FHE can support complex workflows without needing decryption at any point. This makes it ideal for privacy-sensitive fields where untrusted systems need to process sensitive data. However, FHE’s extensive computational requirements currently make it impractical for widespread use.
What are some key applications of homomorphic encryption in healthcare?
In healthcare, HE can enable secure medical data analysis, genomics research, and collaborative studies without exposing sensitive patient information. For example, researchers can use encrypted patient data to run studies or train machine learning models on disease patterns without ever accessing the raw data. This preserves privacy and helps comply with health data privacy laws like HIPAA, making HE particularly valuable in medical research and diagnostics.
How does HE impact data storage and bandwidth?
HE dramatically increases data size due to “ciphertext expansion,” where encrypted data is often hundreds or thousands of times larger than the original plaintext. This requires more storage capacity and network bandwidth to transmit encrypted data, impacting applications with large data sets. In fields like big data and machine learning, the storage and bandwidth needs can make HE impractical without further optimization.
Can homomorphic encryption be used with machine learning models?
Yes, HE can be applied to machine learning models, allowing them to train on or infer from encrypted data. This approach, known as privacy-preserving machine learning, is especially valuable in scenarios like personalized healthcare, finance, and IoT. However, the large data size and computational demands of HE make this challenging, and specialized frameworks, such as TF Encrypted, are being developed to address these issues and make HE more feasible for machine learning.
How are researchers trying to reduce homomorphic encryption’s computational costs?
Researchers are working on several methods to reduce the computational demands of HE:
- Algorithmic Optimizations: Developing new encryption schemes that perform faster operations.
- Hardware Acceleration: Leveraging GPUs, FPGAs, and other specialized hardware to handle HE’s complex computations more efficiently.
- Hybrid Encryption Models: Combining HE with other encryption techniques to improve performance without sacrificing privacy, balancing the benefits of HE with lower computational requirements.
These methods are helping bring HE closer to practical, large-scale application, though more work is needed for full implementation.
What are some examples of homomorphic encryption software libraries?
Several open-source libraries and frameworks support HE:
- Microsoft SEAL: Developed by Microsoft, SEAL provides tools for working with HE, making it more accessible to developers.
- IBM HELib: Created by IBM, HELib is another popular library that offers a range of tools for implementing homomorphic encryption schemes.
- PySyft: A Python library for encrypted machine learning that includes support for HE, useful in secure data processing scenarios.
These libraries simplify the development process by providing pre-built HE algorithms, making it easier for organizations to experiment with HE without needing extensive cryptographic expertise.
How do privacy laws impact the implementation of homomorphic encryption?
Privacy regulations like GDPR and CCPA are generally supportive of HE, as it aligns well with the principles of data protection by keeping data encrypted during processing. However, regulations often require transparency in data processing, which can be a challenge with complex technologies like HE. For organizations, maintaining compliance while using HE involves detailed documentation, audits, and sometimes legal consultation to ensure that their HE implementations align with privacy laws.
How is the lack of standardization affecting homomorphic encryption adoption?
Without universal standards, HE implementations vary widely in terms of security and efficiency, complicating efforts to integrate HE with other systems. This lack of standardization also creates interoperability issues, as different applications and organizations may use different HE schemes, making it harder to share or transfer encrypted data. Efforts are underway to develop common HE standards and protocols that could improve consistency, reliability, and security across applications and industries.
What is the role of edge computing in improving homomorphic encryption’s performance?
Edge computing can help reduce the latency and bandwidth issues associated with HE by allowing encrypted data to be processed closer to the data source. For example, in IoT applications, processing encrypted data on edge devices reduces the need for data to travel to distant servers, improving speed and efficiency. Edge computing
What role does hardware acceleration play in making homomorphic encryption faster?
Hardware acceleration, using devices like GPUs and FPGAs, is a promising way to speed up homomorphic encryption. These processors can handle the intensive mathematical operations required by HE much more efficiently than traditional CPUs. By integrating specialized hardware, companies can significantly reduce the processing time and energy consumption of HE computations, bringing HE closer to real-world feasibility for applications that require faster data processing.
What are the differences between fully, partially, and somewhat homomorphic encryption?
- Partially Homomorphic Encryption (PHE) supports only one type of operation, such as addition or multiplication, but not both.
- Somewhat Homomorphic Encryption (SHE) can handle both addition and multiplication but only for a limited number of operations before it loses accuracy.
- Fully Homomorphic Encryption (FHE) supports unlimited additions and multiplications, allowing any computation on encrypted data. FHE is the most versatile but also the most computationally demanding, which makes it challenging to scale for real-world use.
Resources
Homomorphic Encryption Libraries and Toolkits
- Microsoft SEAL
Microsoft SEAL is a powerful, open-source library for homomorphic encryption. Developed by Microsoft, it supports a variety of homomorphic encryption schemes and is well-suited for developers interested in exploring both partially and fully homomorphic encryption. It includes comprehensive documentation, example code, and community support, making it a great starting point. - IBM HELib
HELib is a popular homomorphic encryption library developed by IBM. Written in C++, it focuses on Fully Homomorphic Encryption (FHE) over integers. HELib is widely used in research and education for exploring FHE, offering extensive functionalities and optimization for efficient encryption. - PALISADE
PALISADE is an open-source library focused on lattice-based cryptography, including HE schemes. It offers support for FHE, privacy-preserving machine learning, and secure multiparty computation. This library is suitable for advanced research and applications where data privacy is crucial. - TFHE (Fast Fully Homomorphic Encryption over the Torus)
TFHE is optimized for binary gates, providing an efficient implementation of homomorphic encryption. Known for its speed and flexibility, it is a preferred choice for applications needing fast FHE operations, particularly in binary and bitwise operations.
Research and Academic Resources
- HomomorphicEncryption.org
HomomorphicEncryption.org is a collaborative organization focused on standardizing homomorphic encryption. They publish guidelines, research updates, and best practices for implementing HE securely and efficiently. The site provides whitepapers and links to conferences and workshops on homomorphic encryption. - The Handbook of Applied Cryptography by Alfred Menezes, Paul van Oorschot, and Scott Vanstone
This handbook covers essential cryptographic concepts, including encryption fundamentals. Although it doesn’t focus exclusively on homomorphic encryption, it provides a strong foundation in cryptographic principles, which is helpful for understanding HE at a technical level.
Available as a free PDF download on the authors’ website. - Stanford Online Course: Cryptography I
Offered by Stanford University on platforms like Coursera, this introductory course on cryptography includes foundational topics that support understanding advanced methods like homomorphic encryption. It is a useful resource for beginners and those seeking structured learning.
Visit Coursera or Stanford’s online education portal.
