
In the ever-evolving field of cybersecurity, staying ahead of potential threats is crucial. With cyberattacks growing in complexity, traditional methods often struggle to keep up.
Enter Self-Organizing Maps (SOMs)—a type of unsupervised learning that’s increasingly being used to detect anomalies in cybersecurity. SOMs offer a sophisticated way to detect unusual patterns in data, allowing for quicker response times to potential threats.
In this article, we’ll dive into how Self-Organizing Maps can transform anomaly detection in cybersecurity.
What is a Self-Organizing Map?
Before exploring its role in cybersecurity, let’s break down what a Self-Organizing Map is. SOMs are a type of neural network, developed by Teuvo Kohonen in the 1980s, designed to visualize and organize high-dimensional data into a low-dimensional format, usually a two-dimensional grid. Unlike traditional neural networks, which are often used for classification or prediction, SOMs are particularly effective in clustering and data visualization.
SOMs work by grouping similar data points closer together, which makes it easier to spot anomalies that deviate from the established pattern.
Why Use SOMs for Anomaly Detection in Cybersecurity?
1. Unsupervised Learning for Complex Data
Cybersecurity systems generate massive amounts of data every second. From network traffic logs to user behavior analytics, the sheer volume makes it hard to distinguish between normal and malicious activity. Self-Organizing Maps use unsupervised learning, meaning they don’t require labeled data to function. This makes them incredibly useful in scenarios where defining normal vs. abnormal behavior in advance is impossible.
2. Pattern Recognition
One of the primary benefits of SOMs is their ability to recognize complex patterns within large datasets. For cybersecurity, this means identifying subtle changes in network activity, login behavior, or even file access patterns that might otherwise go unnoticed by traditional rule-based systems. SOMs allow cybersecurity systems to “learn” what normal behavior looks like, and then flag outliers that could signal a breach or attack.
3. Real-Time Detection
When it comes to cyber threats, time is of the essence. SOMs are capable of real-time anomaly detection, which is crucial for preventing or mitigating attacks before they cause significant damage. By constantly monitoring data and updating the map, SOMs help identify anomalies as soon as they occur, allowing cybersecurity teams to respond more quickly.
How SOMs Detect Anomalies
1. Data Mapping and Clustering
When SOMs are applied in cybersecurity, data such as network traffic or login attempts are fed into the map. The high-dimensional data is then mapped onto a two-dimensional grid where similar data points are clustered together. Any data points that are far from the clusters or form a new pattern are considered anomalies.
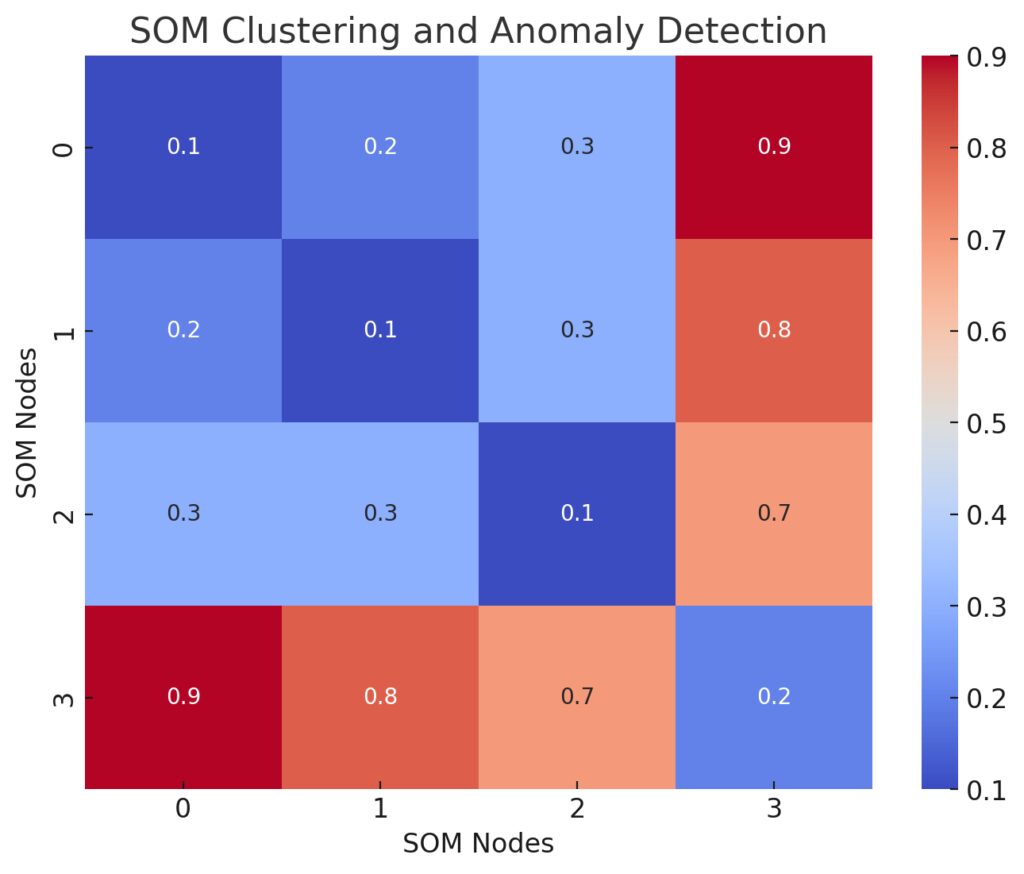
2. Visualization of High-Dimensional Data
The key strength of SOMs lies in their ability to visualize high-dimensional data. For cybersecurity analysts, this is invaluable. It allows them to observe the clustering of normal behaviors and easily spot where anomalies, such as unusual spikes in network traffic, are occurring. These visualizations offer intuitive insights that help analysts identify and mitigate potential threats.
3. Detecting Unusual Patterns
Anomalies in cybersecurity can range from slight deviations in network traffic to more obvious signs of a DDoS attack or a malware infection. SOMs can be trained to detect both minor irregularities and larger, more obvious threats, making them a versatile tool for anomaly detection.
Real-World Applications of SOMs in Cybersecurity
1. Intrusion Detection Systems (IDS)
SOMs are widely used in Intrusion Detection Systems to monitor network traffic. By continuously analyzing patterns in the data, these systems can detect unauthorized access attempts, such as brute force attacks or suspicious logins from unknown locations, even when such events don’t trigger standard alarms.
2. Malware Detection
SOMs can also be applied to detect malware by analyzing file behaviors and system operations. Since malware often behaves differently from legitimate software, SOMs can flag unusual file activities, such as unexpected memory usage or file modification patterns, for further investigation.
3. Fraud Detection
In industries like banking and e-commerce, SOMs are employed to spot fraudulent activities, such as abnormal transactions. These algorithms can analyze user behavior and transaction histories, flagging any deviations from established patterns.
Limitations of SOMs in Anomaly Detection
1. Training Time
Although SOMs are effective in unsupervised learning, they can require significant time and computational resources to train, especially when dealing with large, complex datasets typical in cybersecurity environments. However, once the model is trained, it can operate efficiently in real-time.
2. Complexity in Tuning
Like any machine learning model, fine-tuning SOMs for anomaly detection in cybersecurity can be challenging. Parameters such as the size of the grid and the number of training iterations can significantly impact the map’s performance, requiring expertise and experimentation.

The Future of SOMs in Cybersecurity
As cyberattacks become more sophisticated, the use of AI and machine learning in anomaly detection will continue to grow. SOMs, with their ability to detect complex patterns in unsupervised environments, are likely to play an even bigger role in next-gen cybersecurity solutions.
Combining SOMs with other machine learning techniques, such as deep learning and reinforcement learning, could lead to even more advanced detection systems. These hybrid models would be able to detect even the most subtle anomalies, providing organizations with enhanced protection against emerging cyber threats.
In conclusion, Self-Organizing Maps provide a powerful tool for anomaly detection in cybersecurity. Their ability to recognize patterns, handle complex data, and operate in real-time makes them a valuable asset in safeguarding systems from ever-evolving cyber threats. While there are challenges, the benefits far outweigh the drawbacks, making SOMs a key player in the future of cybersecurity.
FAQs: Self-Organizing Maps in Cybersecurity
What kind of data do SOMs analyze for anomaly detection?
SOMs can analyze a wide range of data, including network traffic logs, user login behavior, file access patterns, and system performance metrics. Any form of high-dimensional data where normal vs. abnormal patterns are crucial for security can be processed by SOMs.
How do SOMs detect cyber threats?
SOMs detect cyber threats by creating clusters of similar data points (normal behavior) on a map. When new data deviates from these clusters, the SOM flags it as a potential anomaly. These anomalies could represent cyberattacks, unauthorized access, or malware activity.
What are the advantages of using SOMs for cybersecurity?
SOMs offer several advantages:
- Unsupervised learning allows them to detect new and unknown threats.
- Real-time detection helps cybersecurity teams respond to threats quickly.
- They excel at identifying complex patterns in massive data sets, making them ideal for monitoring large-scale networks.
Can SOMs be used in real-time systems?
Yes, Self-Organizing Maps can be integrated into real-time systems for continuous monitoring. Once trained, they can operate efficiently in real-time, detecting anomalies as they occur.
What are some real-world applications of SOMs in cybersecurity?
SOMs are used in various cybersecurity systems, including:
- Intrusion Detection Systems (IDS): Monitoring network traffic for unauthorized access.
- Malware Detection: Identifying abnormal file behaviors or system processes that indicate a malware infection.
- Fraud Detection: Detecting abnormal user or transaction behavior in banking and e-commerce systems.
What are the challenges of using SOMs for cybersecurity?
Some challenges include:
- Training time: SOMs can take time and computational resources to train, especially on large datasets.
- Fine-tuning: Optimizing parameters such as grid size and training iterations requires expertise and experimentation.
| Aspect | Pros | Cons |
|---|---|---|
| Unsupervised Learning | No need for labeled data; can detect unknown threats. | May detect false positives due to undefined “normal” data. |
| Real-Time Detection | Capable of detecting anomalies in real time. | Initial setup and tuning may slow deployment. |
| Pattern Recognition | Excellent at identifying complex patterns in data. | Can struggle with minor anomalies or subtle deviations. |
| Training Time | Once trained, operates efficiently in real-time. | Requires significant time and computational resources to train. |
| Fine-Tuning Complexity | Can adapt to various types of data with correct tuning. | Complex parameter tuning, such as grid size and iterations, is required for optimal results. |
| Data Visualization | Provides intuitive visual representation of anomalies. | High-dimensional data visualization may still be challenging in some contexts. |
| Scalability | Scales well with large datasets once trained. | May require additional computational power for extremely large datasets. |
This table highlights the advantages and limitations of using SOMs, offering a clear view of where they excel and where potential challenges lie.
Can SOMs be combined with other AI techniques?
Yes, SOMs can be combined with other AI techniques, such as deep learning or reinforcement learning, to create more sophisticated and accurate cybersecurity systems. These hybrid models can offer enhanced detection capabilities for complex or subtle threats.
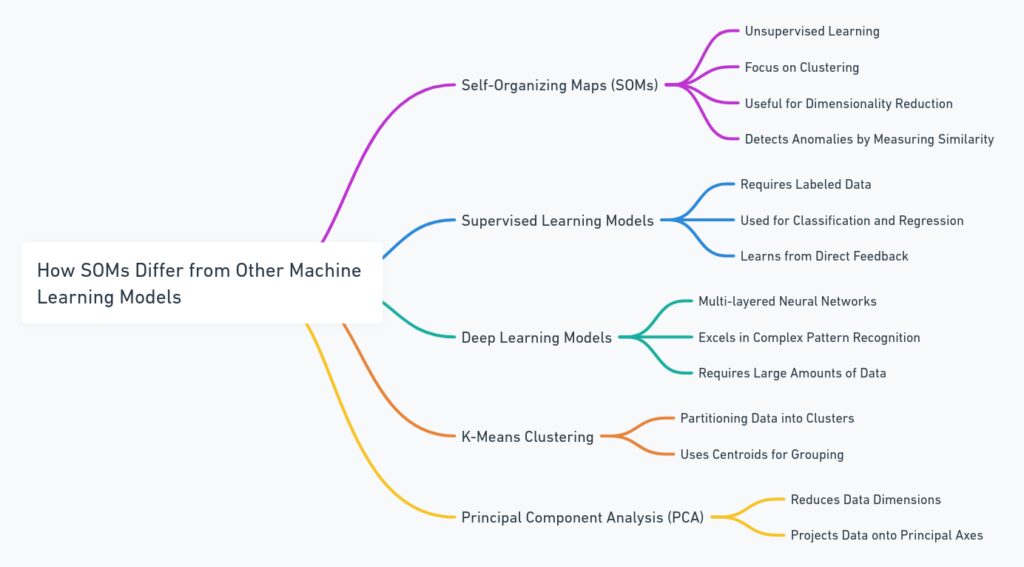
How do SOMs differ from other machine learning models?
Unlike supervised models, SOMs don’t require labeled data. They learn to cluster data based on inherent similarities, making them highly useful in environments where it’s difficult to label data or define what constitutes “normal” behavior in advance.
Is it necessary to have a background in machine learning to implement SOMs?
While it helps to have some knowledge of machine learning, many cybersecurity platforms incorporate SOMs into their detection systems, making it easier for cybersecurity professionals to use them without needing in-depth expertise in machine learning.
Resources
- IEEE Xplore
A vast digital library for accessing research papers on machine learning, cybersecurity, and Self-Organizing Maps. It offers cutting-edge studies and is a valuable resource for both academic and industry professionals.
Visit IEEE Xplore - SpringerLink
This platform provides access to a range of scientific journals, including key papers on neural networks and anomaly detection techniques. SpringerLink is a great source for peer-reviewed studies on SOMs in cybersecurity.
Visit SpringerLink - Google Scholar
A free-to-use search engine that indexes the full text of scholarly literature across an array of publishing formats. Use it to find papers, books, and theses related to Self-Organizing Maps and their application in anomaly detection.
Visit Google Scholar - Kaggle
An open-source platform where you can find datasets and tutorials on implementing machine learning techniques, including SOMs. It’s particularly useful for practitioners looking to experiment with cybersecurity anomaly detection algorithms.
Visit Kaggle - Coursera – Machine Learning and Cybersecurity
Courses offered by top universities that provide hands-on experience with machine learning models, including Self-Organizing Maps for cybersecurity applications.
Visit Coursera