
One-shot learning has emerged as a vital approach for tasks where large amounts of data are hard to come by. When we talk about one-shot learning, we refer to the ability of a system to learn from just a few examples, sometimes even a single one.
This is a challenge because most traditional machine learning models rely on large datasets to accurately make predictions. But that’s where Siamese networks step in, acting as a game-changer, especially in tasks like signature verification.
Understanding Siamese Networks: A Quick Overview
At its core, a Siamese network is a type of neural network architecture designed to compare two inputs and determine their similarity. Unlike other architectures, which may only deal with one input at a time, Siamese networks work with pairs of inputs. The idea is to map these inputs into a space where the distance between them corresponds to their similarity. If two inputs are similar (e.g., two images of the same person’s signature), their distance will be small; if they are different, the distance will be large.
So why is this architecture so powerful? Well, it’s because of its ability to generalize. Rather than learning to classify every possible example, it learns a function that can recognize when two inputs are alike.
Signature Verification: The Classic Use Case
One of the most well-known applications of Siamese networks is in signature verification. In this context, the network’s task is to determine whether a given signature matches the known signature of an individual. This is extremely important in areas like banking, contracts, and secure document processing.
Here’s how it works: You provide the model with two signature images. One is the reference (authentic) signature, and the other is the new signature that needs verification. The Siamese network processes both images through identical sub-networks that extract features from each image. Afterward, it computes the similarity score between these feature sets. If the score is above a certain threshold, the signatures are considered a match. Otherwise, they’re flagged as different.
Why Siamese Networks Are Ideal for Signature Verification
The primary strength of Siamese networks in signature verification lies in their one-shot learning ability. In real-world applications, you don’t often have dozens or hundreds of signatures for each individual, so you need a model that can learn from limited data. This is where Siamese networks shine. Because they focus on learning the relationship between pairs rather than memorizing individual examples, they can perform well even when there are very few samples per person.
Additionally, these networks are also robust to variations in how a signature might be written. Factors like pen pressure, speed, or slight deviations in stroke can make the task tricky. But because a Siamese network learns a generalizable comparison function, it can handle these variations effectively.
Other Applications in One-Shot Learning
Beyond signature verification, Siamese networks have found their place in various one-shot learning tasks. From facial recognition to object tracking and even medical diagnosis, they offer a flexible and powerful framework for comparing and identifying items based on minimal examples.
One interesting application is in facial verification, where a model compares two facial images and determines if they belong to the same person. This is useful for security systems, where you might need to verify someone’s identity without a vast database of images for comparison. Similar to signature verification, Siamese networks can recognize facial features even if lighting, angles, or expressions differ slightly.
How Do Siamese Networks Work Under the Hood?
The internal mechanics of a Siamese network are both simple and brilliant. Here’s a quick breakdown:
- Two identical networks process the inputs, which could be images, text, or even sounds. These sub-networks share the same architecture and weights, ensuring that both inputs are treated in the same way.
- Feature extraction occurs in each sub-network. For example, in signature verification, the features might be curves, line thickness, or patterns that are unique to the individual’s writing.
- Once the features are extracted, a distance metric (often Euclidean distance) is applied to calculate how similar or different the two inputs are.
- The output is a score or probability that indicates whether the inputs are a match.
This process allows the model to learn in a way that’s very different from traditional classification models. Instead of predicting a label, it learns to compare.
Expanding the Use Cases of Siamese Networks
While signature verification is a well-established use case, the versatility of Siamese networks in one-shot learning opens the door to a variety of other applications. Let’s dive deeper into some of the more fascinating and advanced uses of this architecture.
Facial Recognition: Unlocking Your Devices
One of the most popular modern applications of Siamese networks is in facial recognition systems, such as those used to unlock smartphones or control access in secure buildings. These systems don’t require hundreds of images of your face to learn how to recognize you. Instead, they can compare a current image of your face to a stored reference image and determine whether it’s a match.
Facial Recognition Example

Here’s why Siamese networks work so well for facial recognition:
- The model doesn’t need to memorize every face it sees; it simply needs to learn relationships. By comparing key features like eye distance, jawline shape, and more, the network can generalize well to unseen faces.
- It’s highly efficient in terms of data. You only need one or a few images of a face to build a reliable system.
- It’s robust to variations like facial hair, glasses, or even changes in lighting.
Handwriting Verification: Beyond Signatures
While signature verification is the classic example, Siamese networks are also highly effective for general handwriting verification. For example, they could be used to confirm the authenticity of handwritten legal documents, letters, or even historical manuscripts. The same principles apply here—comparing key features like stroke patterns, writing pressure, and letter formation helps determine whether two handwriting samples match.
Medical Image Analysis: Identifying Rare Diseases
In the medical field, particularly in medical image analysis, one-shot learning is incredibly valuable. Sometimes, doctors need to diagnose rare diseases that only show up in a handful of cases. Training a traditional machine learning model with so few examples would be difficult, but Siamese networks can be trained to compare a new image (e.g., an X-ray or MRI) with a set of reference images of known cases.
For instance, in radiology, a model could compare images of healthy tissue with those that show signs of a rare condition. The network learns to detect small, subtle differences that might go unnoticed by the human eye, enabling earlier and more accurate diagnoses.
Object Tracking in Video Streams
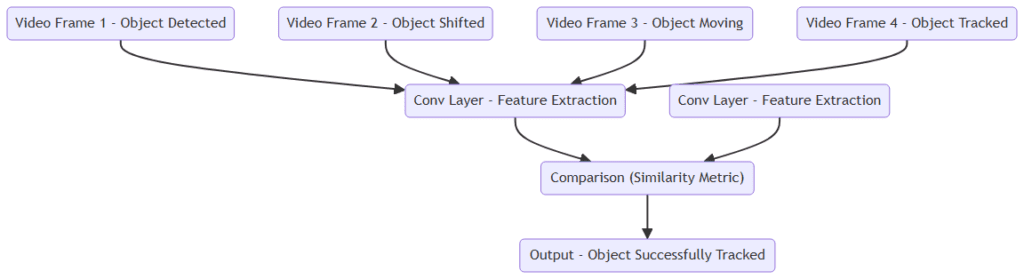
Another exciting application is in object tracking, such as following a car or person across frames in a video. Traditional tracking algorithms often need extensive training data for each object, but a Siamese network can solve this problem using its comparison approach. Instead of learning to identify every possible object in every context, it just learns to compare one frame of an object to subsequent frames. This approach makes object tracking more flexible and efficient, especially in dynamic environments where objects can change position, orientation, or lighting.
Personalized Recommendation Systems
Siamese networks are also finding their way into recommendation systems, particularly those that rely on user preferences. For example, a music streaming service could use a Siamese network to compare your listening habits to those of other users and recommend new songs based on the similarities between your preferences. Rather than needing large amounts of data on each user, the system could work effectively even if you’ve only listened to a handful of songs.
By comparing users based on behavior patterns—like song tempo, genre preferences, or listening time—the network learns to suggest content tailored to your tastes.
Signature Forgery Detection: The Next Level
Beyond verifying signatures, Siamese networks are also being used to detect forgery attempts. The same model that identifies genuine signatures can also be trained to spot signs of tampering or forgery. This is particularly important in legal or financial settings, where fraudulent signatures can cause significant harm.
What makes this even more interesting is that a well-trained Siamese network can often outperform human experts in detecting forgeries, especially subtle ones. By focusing on fine details in a signature—like minute differences in stroke pressure or angle—the model can pick up on variations that humans might overlook.
Language Translation Verification: Are They Saying the Same Thing?
Another niche but fascinating use of Siamese networks lies in language translation verification. When translating from one language to another, it’s essential to verify that the two versions convey the same meaning. By feeding a network with pairs of sentences, one in the original language and one in the translated language, the Siamese architecture can help ensure that the translations match in terms of meaning, even if the phrasing differs.
For businesses operating in global markets, this could ensure that marketing messages, contracts, or product instructions are accurately translated, avoiding costly miscommunications.
Comparing Siamese Networks with Other Architectures
When we think about one-shot learning tasks, Siamese networks aren’t the only game in town. But they have some distinct advantages over other neural network architectures:
Illustrating the Siamese Network Architecture

Efficiency in data usage: Siamese networks shine when you have limited data, which makes them ideal for situations like signature verification or facial recognition. Other architectures might need massive amounts of labeled data to achieve similar results.
Flexibility: Traditional models often require a lot of specific examples for each class they need to predict. But with a Siamese network, you don’t need to train the model on every possible variation of a signature or face—it only needs to learn how to compare.
Generalization capabilities: While many neural networks are prone to overfitting (where they learn patterns that are too specific to the training data), Siamese networks are designed to generalize by focusing on relationships between data points rather than specific characteristics.
Implementing Siamese Networks: Tips for Success
If you’re considering using Siamese networks in a project, there are a few practical tips to keep in mind:
- Preprocessing is key: Whether you’re working with images, text, or some other data type, preprocessing plays a big role in the success of a Siamese network. Clean, well-structured inputs will lead to better feature extraction.
- Choose the right distance metric: Depending on your task, you may want to use different distance metrics, like cosine similarity or Euclidean distance, for measuring the similarity between the two inputs.
- Data augmentation can help: While Siamese networks are great at learning from limited data, using data augmentation techniques—like rotating or flipping images—can still help improve the model’s robustness, especially for image-based tasks.
Siamese networks have proven themselves to be powerful tools in the realm of one-shot learning, solving problems that require efficiency, flexibility, and the ability to work with limited data. From signature verification to facial recognition and beyond, their unique approach of learning to compare has made them invaluable in a variety of industries. Whether you’re verifying signatures or diagnosing rare diseases, Siamese networks offer a flexible and reliable solution for learning in situations where data is scarce but precision is critical.
FAQs:
What is a Siamese network, and how does it differ from traditional neural networks?
A Siamese network is a unique type of neural network that processes two inputs simultaneously to determine their similarity. Unlike traditional networks that classify inputs, Siamese networks compare two inputs by passing them through identical sub-networks and then measuring the similarity between their feature representations. This makes them ideal for tasks where the goal is to recognize relationships rather than just predict a category.
How do Siamese networks contribute to one-shot learning?
In one-shot learning, models are required to make accurate predictions based on very few training examples. Siamese networks excel at this by learning to compare new examples with reference examples, rather than requiring large datasets. They use distance metrics to judge the similarity between pairs of inputs, enabling the model to recognize new classes with minimal data.
How are Siamese networks used in signature verification?
In signature verification, Siamese networks compare two signature images: one known (authentic) and one new. The network processes both images through identical networks that extract features. It then computes a similarity score. If the score is above a set threshold, the signatures are considered a match; otherwise, they are different. This process helps detect forgeries or verify the authenticity of a signature.
Why are Siamese networks so effective for facial recognition?
Siamese networks are highly effective in facial recognition because they learn to compare facial features, such as distances between key points like eyes, nose, and mouth. Instead of memorizing every face, the network generalizes well and can recognize faces even with variations like lighting changes, angles, or expressions, making it ideal for applications like smartphone unlocking or security systems.
What are some real-world applications of Siamese networks beyond signature verification?
Siamese networks are used in a wide variety of applications, including:
- Object tracking in video streams (e.g., following a moving car or person).
- Medical image analysis to compare images for diagnosing rare diseases.
- Handwriting verification to detect forgery or match handwriting samples.
- Language translation verification, ensuring accurate meaning across languages.
- Recommendation systems that compare user behavior for personalized suggestions (e.g., music streaming).
Can Siamese networks handle variations in input, like handwriting differences or changes in facial expressions?
Yes! Siamese networks are robust to variations like handwriting differences or facial expressions because they learn to compare general features rather than specific examples. In handwriting verification, for instance, they can account for natural variations in pen pressure or stroke direction. Similarly, in facial recognition, they recognize a face even if the person is smiling, frowning, or wearing glasses.
What kind of data do Siamese networks work with?
Siamese networks can work with various data types, including images, text, and even audio. They are highly flexible and can be trained to compare pairs of data in tasks like image recognition, text similarity, speech verification, or handwriting analysis. The key is that both inputs must be transformed into comparable feature sets, regardless of the data type.
How do Siamese networks learn to compare inputs?
Siamese networks use shared weights across identical sub-networks to process both inputs. After feature extraction, a distance metric—often Euclidean distance or cosine similarity—is applied to compute the difference between the outputs. The network is trained using pairs of inputs, labeled as similar or dissimilar, so it learns to minimize the distance between similar pairs and maximize the distance between dissimilar pairs.
What are some advantages of Siamese networks compared to other machine learning models?
Some advantages include:
- Data efficiency: Siamese networks can learn from very few examples, which makes them ideal for one-shot learning tasks.
- Flexibility: They don’t need large, labeled datasets to generalize, allowing them to work with minimal training data.
- Generalization ability: Since they focus on comparing inputs, they are less prone to overfitting and can adapt to new data more easily than traditional classifiers.
What challenges can arise when using Siamese networks?
Although Siamese networks are powerful, they can face challenges such as:
- Preprocessing requirements: Input data needs to be clean and well-structured for effective feature extraction.
- Selection of distance metrics: The success of a Siamese network depends on choosing the right distance metric for a given task, which can sometimes require experimentation.
- Computational costs: Depending on the size and complexity of the input data, Siamese networks can be computationally expensive, particularly when processing high-resolution images or videos.
Can Siamese networks be used for forgery detection?
Absolutely. Siamese networks are highly effective in forgery detection tasks, especially for signatures and handwriting. By comparing the fine details of genuine samples to potentially forged ones, they can detect subtle differences, such as variations in stroke order or pen pressure, that might be missed by a human observer.
Are Siamese networks suitable for real-time applications?
Yes, Siamese networks can be adapted for real-time applications like facial recognition and object tracking. However, their performance depends on the complexity of the input data and the network architecture. With optimized models and sufficient computational power, they can provide quick comparisons even in dynamic environments, such as video streams or security systems.
How does data augmentation enhance the performance of Siamese networks?
While Siamese networks are effective with small datasets, data augmentation—creating variations of the input data, such as flipping or rotating images—can further improve their robustness. This helps the network become more resilient to changes in the input, like different angles in facial recognition or slight deviations in handwriting.
Are Siamese networks used in industries outside of tech?
Yes, beyond tech, Siamese networks are making waves in various industries:
- Healthcare, for diagnosing rare diseases through medical image comparison.
- Finance, for verifying signatures or spotting fraud.
- Legal, for verifying handwriting on contracts or documents.
- Retail, where personalized recommendation systems can benefit from user behavior comparisons.
What future developments can we expect for Siamese networks?
As the demand for efficient and flexible machine learning models grows, Siamese networks will continue evolving. We may see advancements in their ability to handle more complex, multi-modal data, where they compare images, text, and sound together. Additionally, the development of lightweight, real-time Siamese architectures could enhance their usability in mobile and edge computing devices.
GitHub Repositories
- Siamese Network with Keras and TensorFlow
A repository with a practical implementation of Siamese networks for one-shot learning tasks like image verification.
GitHub Link - Signature Verification using Siamese Networks
This repository focuses specifically on signature verification using Siamese networks and is an excellent resource for getting started with real-world applications.
GitHub Link