Swarm intelligence is a concept inspired by natural behaviors seen in groups like ants, bees, and birds. In these groups, members work collectively, responding quickly to changes without central control.
Each member follows simple rules, like seeking food or avoiding predators, which result in highly organized group actions.
In cybersecurity, this same idea powers collective defense systems where multiple systems work together, spotting and responding to threats in real-time. The appeal of swarm intelligence is in its ability to harness decentralized insights from each node, which collectively form a strong line of defense.
Origins of Swarm Intelligence in Tech
The concept entered the tech field through AI algorithms and robotics. Originally, developers used it to solve complex problems by mimicking natural group dynamics. Over time, cybersecurity experts recognized its potential in defending against threats, leading to today’s applications in network security, anomaly detection, and beyond.
Key Advantages for Cybersecurity
Swarm intelligence brings several benefits to cybersecurity:
- Adaptability: Swarm-based systems learn and adapt as threats evolve.
- Decentralized Response: Unlike traditional, top-down defense systems, swarm intelligence spreads out detection and response across nodes, reducing vulnerabilities.
- Scalability: Swarm models easily adapt to large-scale networks, making them suitable for organizations of all sizes.
How Swarm Intelligence Works in Cybersecurity
Node Collaboration for Threat Detection
In a swarm-intelligent system, each device or network node acts like a worker in a hive, scanning for suspicious activities or threats. When a device detects something unusual, it communicates this with other nodes. Together, they form a comprehensive response to the detected anomaly, coordinating actions in real-time without needing a central command.
These systems can be programmed to identify patterns—like repeated login attempts or abnormal data transfer rates—that suggest potential attacks. The collective responses act faster than traditional, singular defenses, providing an edge against fast-evolving cyber threats.
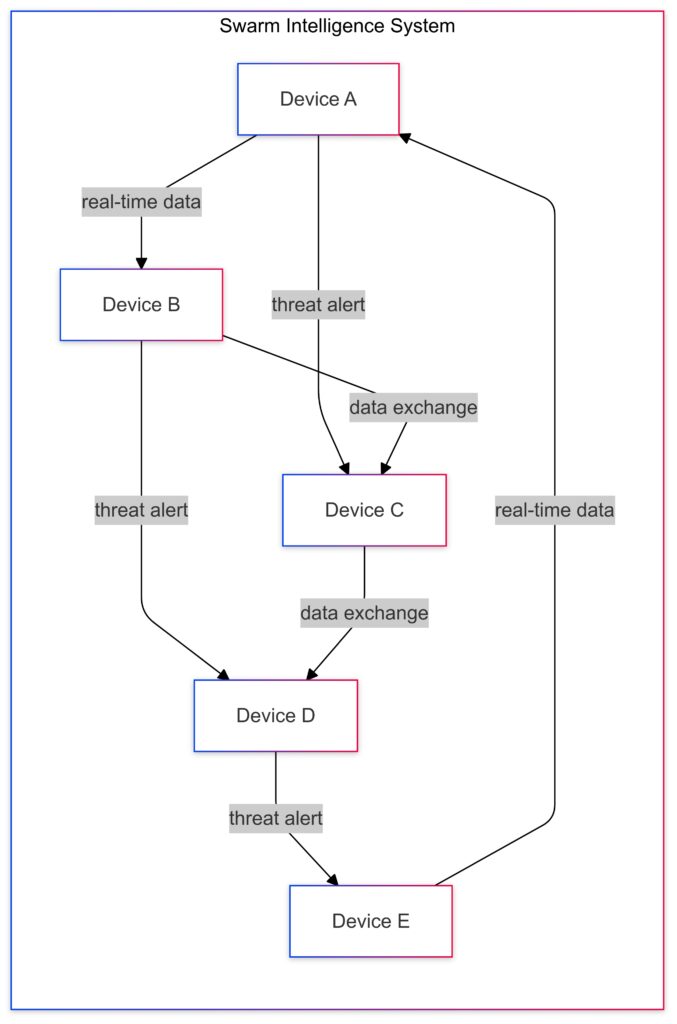
Data Exchange and Threat Alerts flow through the network, with alerts shared in real-time to enhance rapid response to potential threats.
Real-Time Data Sharing
Real-time data exchange is central to swarm intelligence. When one node encounters a threat, it instantly shares this information, so other nodes are ready to respond. This constant exchange allows systems to learn from each other’s experiences and avoid isolated vulnerabilities, effectively creating a collective immune system for the entire network.
The more the system operates, the smarter it becomes. Algorithms can prioritize threats based on severity, automatically triggering responses that prevent potential breaches across the network.
Self-Learning Capabilities
Unlike static systems, swarm intelligence operates with self-learning capabilities. Nodes can adjust based on the patterns they observe, continually refining their responses. This adaptability makes them especially suited to combat advanced, persistent threats (APTs) that evolve over time. With each encounter, the system improves, developing a more nuanced understanding of potential threats.
Real-World Applications of Swarm Intelligence in Cybersecurity

Adaptive Network Defense
Many cybersecurity firms are using swarm intelligence to fortify network defenses. For example, when an attack targets a network, swarm algorithms ensure all devices work together to fend off the threat. This collective effort enables each node to analyze and respond independently, making the system resilient against attacks aimed at a single weak point.
This approach is increasingly popular in large organizations, where traditional defenses struggle to keep up with complex, multi-vector attacks. Swarm intelligence provides a scalable and effective solution that can quickly evolve to meet new threats.
Botnet Detection and Prevention
Botnets are notoriously difficult to detect because they hide within regular network traffic. Swarm intelligence, however, shines in this scenario. By constantly analyzing behavior across all nodes, these systems can spot botnet patterns—like unusual traffic spikes or strange connection requests. When one node identifies potential bot activity, it alerts others, allowing the network to proactively block the threat before it can spread.
This method reduces the risks of botnet-driven attacks, such as distributed denial of service (DDoS) attacks, which can bring down entire websites and services. Swarm intelligence provides a distributed approach to counter these distributed threats effectively.
| Application | Finance | Healthcare | IoT | Critical Infrastructure |
|---|---|---|---|---|
| Fraud Detection | 🕵️ Pattern Analysis Uses swarm intelligence to identify suspicious transaction patterns and detect fraud | 🔍 Claim Verification Flags anomalous insurance claims for verification | 🔍 Device Behavior Monitoring Detects unusual IoT device behavior for early fraud prevention | 🚨 Transaction Anomaly Detection Monitors payment systems for abnormal patterns |
| Endpoint Security | 🔐 Real-Time Defense Applies swarm-based models for quick identification of new malware on user endpoints | 🛡️ Health Data Protection Secures patient records against unauthorized access | 🔒 Network Safety Leverages swarm intelligence to secure connected devices | 🔒 Industrial Endpoint Protection Guards infrastructure devices from unauthorized access |
| Botnet Detection | 🕸️ Network Monitoring Continuously scans for unusual network behavior to detect botnet activity | 🧬 Threat Isolation Detects and isolates botnet-infected devices in the healthcare network | 🌐 IoT Botnet Defense Identifies and alerts on botnet formation in connected IoT devices | 🌐 Threat Containment Uses swarm models to isolate bot-infected systems quickly |
| Insider Threat Monitoring | 👀 Behavioral Analysis Identifies potential insider threats through continuous employee behavior monitoring | 🏥 Access Oversight Tracks abnormal access patterns in sensitive healthcare information | 📡 Internal IoT Access Observes patterns to detect unauthorized access within IoT networks | ⚙️ System Access Control Alerts for unusual access in critical system areas |
Each application leverages swarm intelligence principles, such as distributed threat detection and rapid response, tailored to meet specific needs across sectors.
Fraud Detection in Financial Systems
In the financial sector, swarm intelligence aids in detecting fraudulent activities across complex transactional networks. Traditional methods often rely on after-the-fact analysis, but swarm-based systems flag unusual behavior in real-time. When a transaction deviates from typical patterns, nodes can immediately assess its legitimacy, minimizing the risk of financial losses.
The system’s decentralized nature is especially beneficial for banks and financial institutions that require instantaneous threat detection. By leveraging swarm intelligence, these organizations reduce the risk of fraud slipping through unnoticed.
Benefits of Swarm Intelligence Over Traditional Cybersecurity
Faster, Decentralized Responses
Traditional cybersecurity models rely on central control to direct responses. While effective, they can be slow when threats emerge rapidly. Swarm intelligence’s decentralized structure enables much faster responses, as each node works independently yet collectively. When facing fast-spreading malware, this speed can mean the difference between containment and full-scale infiltration.
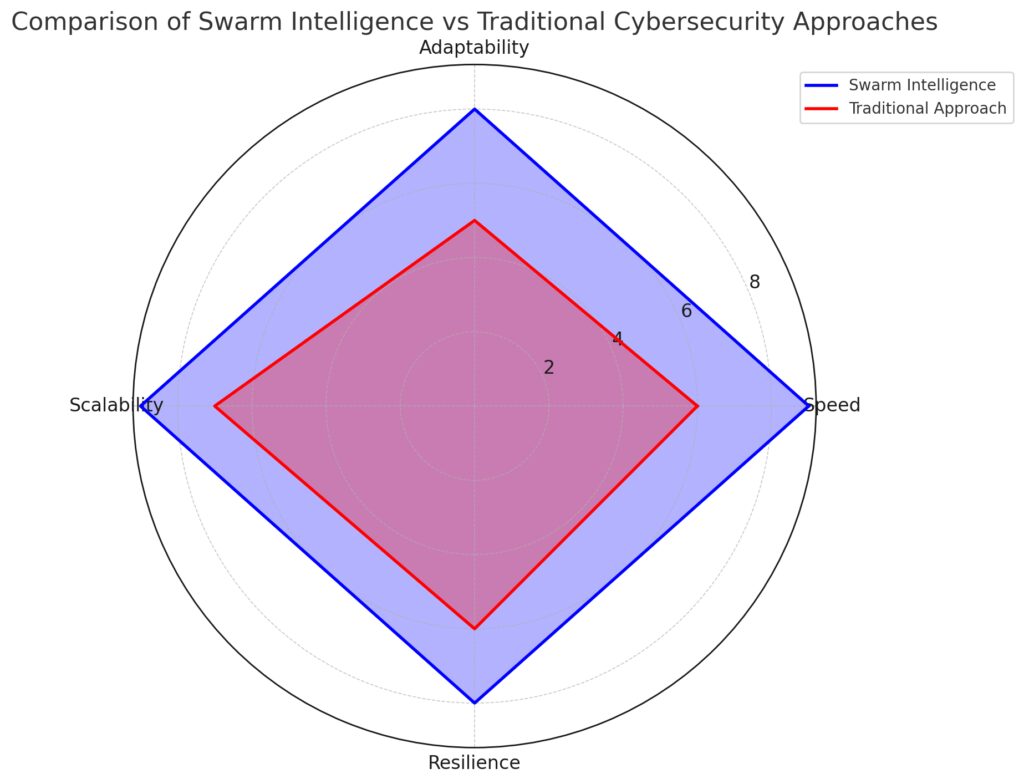
Speed and Adaptability: Swarm intelligence outperforms, offering faster and more adaptive responses to threats.
Scalability: Swarm intelligence is inherently scalable, enabling large networks of devices to collaborate seamlessly.
Resilience: The decentralized structure of swarm intelligence provides greater resilience against attacks.
The blue area highlights swarm intelligence’s advantages, while the red area shows traditional approaches, making the contrast in performance across these benefits clear.
Reduced Single Points of Failure
With swarm intelligence, there’s no single point of failure. Even if one node is compromised, the rest of the system remains strong. This resilience makes swarm intelligence ideal for systems with numerous interconnected devices, such as IoT networks, where vulnerabilities are harder to pinpoint.
Continuous Adaptation
Unlike traditional systems that require manual updates to stay effective, swarm-based systems continuously adapt. As each node learns from real-time threats, it automatically shares this knowledge, resulting in an ever-evolving defense system. This capability is especially valuable against sophisticated, emerging cyber threats that evade static defenses.
Challenges and Limitations of Swarm Intelligence in Cybersecurity
Complexity of Implementation
Despite its advantages, implementing swarm intelligence in cybersecurity is complex. Integrating swarm algorithms across a network requires significant resources, from advanced hardware to specialized software. The system must be configured to ensure each node can communicate efficiently and respond autonomously without creating bottlenecks or communication delays.
Furthermore, these systems demand expertise in AI and machine learning, as well as continuous monitoring to fine-tune the algorithms. This complexity can make it challenging for smaller organizations with limited IT resources to adopt swarm intelligence.
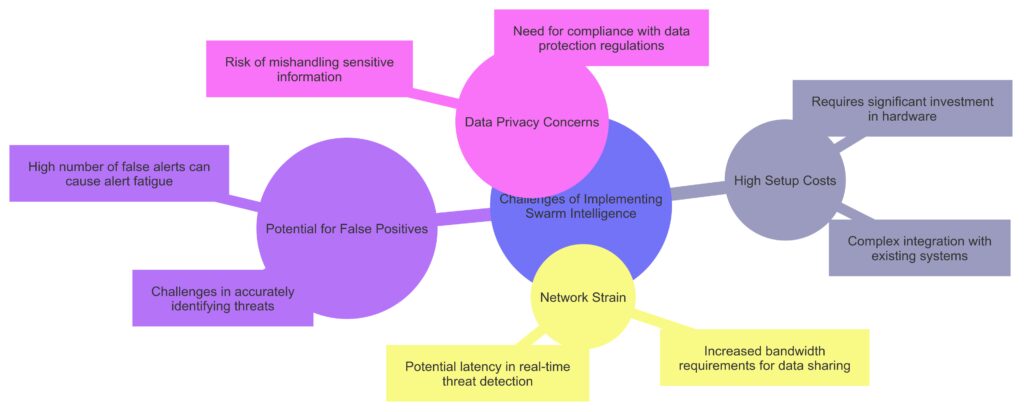
High Setup Costs: Involves significant investment in hardware and complex integration with current systems.
Network Strain: Increased bandwidth demands and potential latency can affect real-time threat detection.
Potential for False Positives: Detection inaccuracies and high false alert rates may lead to alert fatigue.
Data Privacy Concerns: Risks associated with handling sensitive data and ensuring compliance with data protection regulations.
Potential for False Positives
Swarm intelligence systems are highly sensitive to anomalies, which is a double-edged sword. While this sensitivity improves threat detection, it can also lead to false positives—incorrectly flagging normal behavior as suspicious. Over time, this can overwhelm the system with unnecessary alerts, causing security teams to miss real threats.
Minimizing false positives requires carefully training the system to distinguish between actual threats and normal variations. As the system learns, it can refine its responses, but until then, security teams may need to validate many alerts manually.
Risk of Network Overload
As each node in a swarm system communicates with others, this continuous data exchange can strain network bandwidth. Large networks may experience performance slowdowns if the system isn’t optimized for high traffic. This is especially true for IoT and cloud environments, where countless devices are connected at once.
Optimizing the swarm to balance security and efficiency is essential. Companies may need to invest in network infrastructure upgrades to support the increased data flow and avoid compromising network performance.
How to Implement Swarm Intelligence in Cybersecurity
Selecting the Right Framework
The first step in implementing swarm intelligence is choosing a framework that aligns with organizational needs. Popular frameworks like Apache Kafka or RabbitMQ offer robust data streaming capabilities, enabling real-time communication between nodes. Some organizations may also choose proprietary cybersecurity platforms with built-in swarm intelligence modules, such as Darktrace or Cylance.
Each organization should assess its needs to determine the best fit. For instance, financial institutions may prioritize real-time fraud detection, while healthcare networks might focus on protecting patient data against breaches.
Integrating Machine Learning and AI
Swarm intelligence relies heavily on AI and machine learning algorithms to analyze patterns and detect threats. Training these algorithms requires historical data on network behavior, past threats, and normal user activity. By feeding this data into the system, companies can help nodes recognize common attack vectors and anomalies.
Collaboration between data scientists and cybersecurity experts is crucial at this stage. Data scientists provide expertise on AI models, while cybersecurity teams contribute insights into threat behavior. This partnership helps develop a system that is both intelligent and highly targeted in identifying threats.
Continuous Monitoring and Optimization
Once a swarm intelligence system is in place, continuous monitoring is essential to ensure it adapts to new types of cyber threats. Security teams should track performance metrics like detection accuracy, response time, and false positive rates. Based on these insights, they can tweak algorithms, optimize node collaboration, and ensure that the system remains effective over time.
Many organizations also establish feedback loops so that the system learns from every detected threat, improving its responses continuously. This ongoing adjustment process ensures that the swarm remains resilient and ready for evolving cyber threats.
Future of Swarm Intelligence in Cybersecurity
Enhancing IoT and Smart Device Security
With the rise of IoT devices and smart technologies, swarm intelligence has significant potential in these environments. These devices often have limited computing power, making them vulnerable to attack. Swarm intelligence can create a decentralized security layer across IoT networks, allowing devices to collectively identify and respond to threats.
The future of swarm intelligence in IoT security is promising. As IoT devices become more integrated into our daily lives, the need for self-defending networks that adjust to threats in real-time will only grow. Swarm intelligence could potentially become the standard for IoT cybersecurity, helping to protect connected devices without the need for constant manual updates.
Real-Time Protection Against Advanced Threats
As cyber threats evolve, advanced persistent threats (APTs) are becoming more frequent and sophisticated. These threats, often orchestrated by well-funded attackers, evade traditional security methods with ease. Swarm intelligence can play a vital role in defending against APTs by providing real-time, decentralized threat detection that adapts as the attack unfolds.
In the future, swarm intelligence systems may become sophisticated enough to predict attacks before they happen, leveraging data from past incidents to anticipate potential vulnerabilities. This proactive approach could mark a new era in cybersecurity, where attacks are stopped before they even begin.
Convergence with Quantum Computing
The future of cybersecurity may also see swarm intelligence combining with quantum computing. Quantum systems could enable swarm intelligence to process and analyze vast amounts of data far more quickly, unlocking new levels of precision in threat detection. This convergence could lead to highly efficient and resilient defense systems capable of keeping up with the speed and scale of cyber-attacks.
Although quantum computing is still in its early stages, research in this area is accelerating. As the technology matures, we may witness breakthroughs in cybersecurity, with swarm intelligence providing the decentralized, adaptable framework necessary to harness quantum power in real-world applications.
FAQs
How does swarm intelligence help in detecting botnets?
Swarm intelligence detects botnets by constantly monitoring behavior across all network nodes. When one node spots suspicious activity (like an unusual traffic spike or connection request), it shares this information with other nodes, allowing the entire network to proactively respond. This collective approach effectively identifies and neutralizes botnets before they can launch attacks like DDoS, offering a layered and adaptive defense.
Is swarm intelligence effective against advanced persistent threats (APTs)?
Yes, swarm intelligence can be highly effective against advanced persistent threats (APTs). APTs are sophisticated, targeted attacks that can evade traditional defenses. Swarm intelligence enables real-time, decentralized monitoring and response, allowing systems to adjust as the APT unfolds. This adaptability and distributed defense make it more challenging for APTs to exploit vulnerabilities, especially in large networks.
What types of organizations benefit most from swarm intelligence?
Organizations with large, complex networks or those facing frequent cyber threats benefit most from swarm intelligence. This includes sectors like finance, healthcare, government, and critical infrastructure. Swarm intelligence offers these organizations real-time adaptability and scalable protection, which is essential for safeguarding sensitive data and preventing costly cyber-attacks.
How does swarm intelligence differ from traditional cybersecurity approaches?
Unlike traditional cybersecurity, which often relies on centralized detection and response systems, swarm intelligence distributes these tasks across multiple nodes. Each node can independently detect threats and share data with others, resulting in a faster and more adaptive response. This decentralized approach minimizes single points of failure and continuously adapts to emerging threats, making it more resilient than static, centralized models.
Does swarm intelligence require a lot of computational power?
Swarm intelligence does require some computational power to operate effectively, especially in large-scale networks. Each node in a swarm needs to analyze data and communicate findings with other nodes, which can demand resources. However, most systems are designed to balance the computational load across nodes, optimizing processes to avoid overwhelming any single device. As technology advances, swarm intelligence systems are becoming more efficient, making them accessible even to mid-sized organizations.
Can swarm intelligence work alongside existing cybersecurity systems?
Yes, swarm intelligence can complement existing cybersecurity measures rather than replace them. It works well alongside traditional firewalls, antivirus programs, and intrusion detection systems by providing an extra layer of defense that is adaptive and decentralized. Integrating swarm intelligence with these systems can help organizations achieve more comprehensive coverage, as swarm nodes communicate threats in real-time, which enhances the responsiveness of other security measures.
How does swarm intelligence handle false positives in cybersecurity?
False positives are a common challenge in swarm intelligence systems, especially during initial setup. To manage this, machine learning algorithms within the system are continuously trained and refined using historical and real-time data. Over time, the system becomes better at distinguishing legitimate threats from harmless anomalies, which reduces false positives. Some organizations also use human oversight to validate alerts in the early stages of deployment, allowing the system to “learn” from corrections.
What is the role of machine learning in swarm intelligence?
Machine learning is fundamental to enhancing swarm intelligence in cybersecurity. By analyzing historical data, machine learning algorithms can identify patterns and predict potential threats. These predictions help nodes adjust their responses to suspicious activity, improving detection accuracy and reducing false positives. As nodes share insights learned from past threats, the entire system benefits, resulting in a more intelligent, adaptive defense against evolving cyber threats.
Can swarm intelligence prevent zero-day attacks?
Swarm intelligence has significant potential in defending against zero-day attacks, which are vulnerabilities exploited by attackers before they are discovered and patched. By using a decentralized, real-time approach, swarm intelligence enables each node to monitor for suspicious patterns and anomalies that may indicate a zero-day threat. When one node detects an unusual behavior, it alerts the others, allowing the network to respond collectively, even if the vulnerability is not yet known or patched.
How secure is the communication between nodes in swarm intelligence?
The security of inter-node communication is crucial in swarm intelligence. Typically, these systems use encryption protocols to secure data exchanged among nodes, reducing the risk of eavesdropping or data tampering by attackers. Some advanced swarm systems even incorporate blockchain technology for secure, verifiable communication between nodes, ensuring that data shared across the swarm remains private and tamper-resistant.
What role does data sharing play in swarm intelligence?
Data sharing is at the heart of swarm intelligence. When one node detects a threat or anomaly, it shares this information with others, enabling a collective, rapid response. This shared data helps each node learn from the insights and experiences of others, creating a continuous feedback loop that improves threat detection and response. Real-time data exchange ensures that the swarm intelligence system adapts quickly, protecting the network against fast-evolving threats.
Can swarm intelligence systems operate autonomously?
Yes, swarm intelligence systems are designed to operate autonomously, with minimal need for central oversight. Each node functions independently yet collaborates with others, allowing it to detect, respond to, and adapt to threats without human intervention. However, many organizations choose to monitor the system, especially during initial deployment, to fine-tune responses and improve accuracy, which enhances the system’s long-term performance.
Is swarm intelligence suitable for small businesses?
While originally developed for larger, more complex networks, swarm intelligence is becoming increasingly accessible to small businesses. As technology evolves, lightweight swarm intelligence solutions tailored for smaller networks are emerging, allowing small businesses to benefit from collective threat detection without the need for extensive resources. Many small and mid-sized companies now leverage swarm-based security features as part of managed cybersecurity services, which provide scalable protection within budget.
How does swarm intelligence address insider threats?
Swarm intelligence can be effective against insider threats by constantly monitoring and analyzing behavior across all network nodes. When a node detects unusual activities—such as unauthorized data access, unusual login times, or data transfers—it alerts other nodes. This collective observation creates a network-wide response that flags suspicious actions, even if they come from authorized insiders. This approach provides continuous oversight, reducing the risk of insider threats going undetected.
Can swarm intelligence be used for endpoint security?
Yes, swarm intelligence is highly effective for endpoint security. Each endpoint (like a laptop, mobile device, or IoT gadget) can act as a node within the swarm, analyzing and reporting potential threats. This allows each device to detect and respond autonomously, alerting other endpoints of potential risks. With swarm intelligence, endpoint security becomes more dynamic and adaptable, especially valuable in remote and hybrid work environments where traditional perimeter defenses are less effective.
What is the cost of implementing swarm intelligence for cybersecurity?
The cost of implementing swarm intelligence varies depending on the size of the network, level of sophistication needed, and specific security goals. Large organizations may require substantial initial investments in hardware, software, and training. However, for smaller networks, there are now cost-effective options and even subscription-based swarm solutions that make this technology accessible. Many companies also find that swarm intelligence reduces long-term costs by preventing costly breaches and minimizing manual intervention.
How does swarm intelligence enhance cloud security?
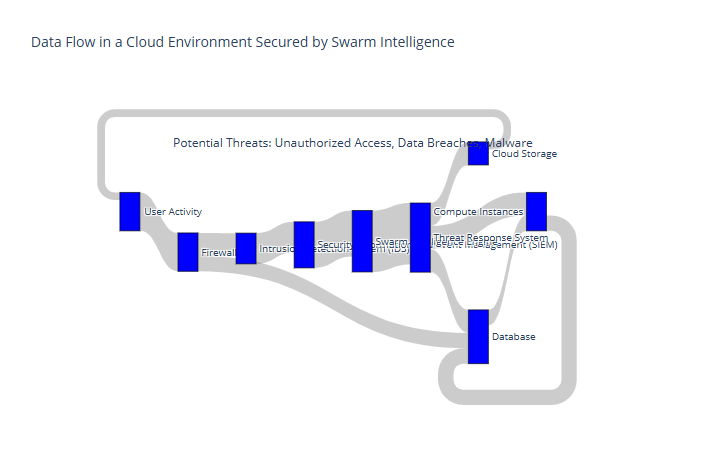
In cloud environments, where resources are highly distributed, swarm intelligence provides a natural fit for real-time, adaptive security. Each cloud resource acts as a node, monitoring for threats within its environment and sharing this information across the network. This setup allows for immediate, coordinated responses to threats within multi-cloud and hybrid-cloud setups, where traditional security tools often fall short. Swarm intelligence also adapts quickly to cloud-native threats, such as misconfigurations and unauthorized access attempts.
Can swarm intelligence improve cybersecurity for critical infrastructure?
Swarm intelligence is increasingly considered a key technology for securing critical infrastructure—such as energy grids, water supplies, and transportation networks—because it provides decentralized, adaptable protection. In these environments, where disruptions can have far-reaching impacts, swarm intelligence enables each infrastructure component to monitor for signs of tampering, failure, or cyber-attack. The real-time, collective response reduces the likelihood of widespread damage from single-point attacks, protecting essential services from malicious disruptions.
How is swarm intelligence different from traditional AI in cybersecurity?
While both swarm intelligence and traditional AI are used in cybersecurity, they differ fundamentally in structure and function. Traditional AI relies on centralized algorithms and data processing, often requiring a central command to analyze threats and deploy defenses. Swarm intelligence, on the other hand, is decentralized, with each node acting independently yet working together. This setup enhances adaptability, speed, and collective decision-making, making swarm intelligence better suited to respond to dynamic, multi-faceted threats.
How does swarm intelligence adapt to new types of cyber-attacks?
Swarm intelligence adapts by learning from each new threat encounter. When a new type of attack or tactic appears, nodes observe and analyze its behavior, adjusting their detection criteria accordingly. This adaptive process is strengthened by machine learning, which allows nodes to retain and share new insights across the network. As a result, the entire system grows smarter and more resistant over time, staying one step ahead of evolving threats.
Are there any privacy concerns with using swarm intelligence?
Privacy concerns in swarm intelligence primarily relate to data sharing among nodes. Since nodes constantly communicate, organizations need to ensure that sensitive data is encrypted and that information shared is limited to what’s necessary for threat detection. Additionally, some organizations implement access controls and data anonymization measures to further protect user privacy, allowing swarm intelligence systems to function effectively without compromising personal or sensitive information.
How scalable is swarm intelligence for large networks?
Network Nodes: Represents the scale of the network, with larger enterprises having more nodes.
Detection Speed (ms): Measures the threat detection speed, which improves as network size increases.
Enterprise Sizes (Small, Medium, Large): Represented by different colors (blue for small, green for medium, and red for large enterprises).
Swarm intelligence is highly scalable, making it ideal for large and complex networks. Each node operates independently, meaning the system can easily grow with the addition of new nodes. This scalability allows swarm intelligence to protect networks of any size, from small business setups to expansive, multi-site corporate environments. For large organizations, swarm intelligence can even operate across distributed data centers and cloud environments, providing cohesive, adaptable security at scale.
Resources
Online Courses and Lectures
- Coursera: “Machine Learning for Cybersecurity”
Offered by the University of Colorado, this course covers machine learning techniques used in cybersecurity, including swarm intelligence models for real-time threat detection. Visit Coursera - Udacity: “AI for Cybersecurity”
This program provides a practical introduction to AI in cybersecurity, covering topics like anomaly detection, threat modeling, and decentralized approaches, including swarm intelligence. Visit Udacity - edX: “Cybersecurity Fundamentals”
This introductory course by Rochester Institute of Technology discusses key aspects of cybersecurity, including newer defense mechanisms like swarm intelligence in later modules. Visit edX
Websites and Blogs
- Darktrace Blog
The Darktrace blog frequently discusses innovations in AI-driven and swarm-based cybersecurity solutions. It’s a great resource for updates on real-world applications and case studies. Visit Darktrace Blog - TechCrunch Cybersecurity Section
TechCrunch regularly covers advancements in cybersecurity, including articles on swarm intelligence and AI-powered defense mechanisms. Visit TechCrunch Cybersecurity - MIT Technology Review – AI and Cybersecurity
This section often features insights into AI’s role in cybersecurity, including articles on decentralized and swarm-based approaches to protecting digital assets. Visit MIT Technology Review
Industry Reports and White Papers
- “Swarm Intelligence in Cybersecurity: Innovations and Trends” by Gartner
Gartner’s annual cybersecurity reports include sections on emerging technologies, with recent years focusing on swarm intelligence as a tool against advanced threats. - “Applying Swarm Intelligence in Critical Infrastructure” by Cisco
This white paper provides an in-depth analysis of how swarm intelligence is being implemented to secure critical infrastructure, with real-world examples and recommendations. - “The Future of AI-Driven Cybersecurity” by McKinsey & Company
This report explores how AI, including swarm intelligence, is transforming cybersecurity across industries. Available on McKinsey & Company