
What is Zero Trust Architecture and Why Does It Matter?
Cyberattacks are evolving rapidly. Traditional security models that trust users and devices once they’re inside the network perimeter are simply not enough anymore.
Enter Zero Trust Architecture (ZTA)—an innovative approach that assumes no user or device should be trusted by default, whether they’re inside or outside your network.
In today’s digital world, cyberattacks are evolving rapidly. Traditional security models that trust users and devices once they’re inside the network perimeter are simply not enough anymore. Enter Zero Trust Architecture (ZTA)—an innovative approach that assumes no user or device should be trusted by default, whether they’re inside or outside your network.
Zero Trust demands verification at every stage, limiting access to sensitive data and applications only when absolutely necessary. It operates on the idea of “never trust, always verify.” By adopting Zero Trust, organizations can significantly reduce risks from cyber threats like malware, phishing, and insider attacks.
With high-profile breaches becoming common, Zero Trust has become crucial. It protects against modern threats while enhancing regulatory compliance and data security. But how can companies incorporate it into their cybersecurity roadmap? Let’s break it down.
Breaking Down the Key Principles of Zero Trust
The foundation of Zero Trust is based on a few key principles. Understanding these principles is essential for successfully integrating it into your cybersecurity strategy:
- Least privilege access: This ensures that users and devices are granted the minimum level of access they need, nothing more.
- Multi-factor authentication (MFA): MFA requires users to verify their identity through multiple methods, making unauthorized access much more difficult.
- Microsegmentation: Rather than having a wide-open network, microsegmentation breaks it into smaller sections, limiting the movement of potential attackers.
- Real-time monitoring: Zero Trust emphasizes continuous monitoring of user behavior, data flow, and network activity to spot suspicious actions in real time.
These principles create a hardened environment where every access attempt is scrutinized and unauthorized actions are stopped before they cause damage.
Zero Trust vs Traditional Security: What’s the Difference?
Traditional security frameworks follow a castle-and-moat approach, where everything inside the network is trusted, and threats are assumed to come from outside. This model worked when networks were closed, and most employees worked on-site. But with cloud computing, remote work, and mobile devices becoming standard, the perimeter has dissolved. It’s no longer clear where “inside” ends.
Zero Trust challenges this outdated idea. In ZTA, everyone is treated as a potential threat—whether they’re working from the office, the coffee shop, or their living room. Every user, device, and system must continuously prove they belong and that they’re following the rules. Unlike traditional security, Zero Trust focuses heavily on verifying identity, managing access dynamically, and using data analytics to detect threats.
Is Your Organization Ready for Zero Trust?
Before you dive headfirst into Zero Trust, it’s essential to assess your current infrastructure. Many organizations are not fully equipped to switch overnight. Start by identifying critical assets that need the most protection. These could be customer data, intellectual property, or core systems.

Next, conduct an audit of your current security policies. Are they flexible enough to support Zero Trust? Legacy systems might not align with ZTA principles, meaning they may need upgrading or replacing. This assessment will help you determine which parts of your infrastructure can integrate with Zero Trust right away and which will need attention over time.
Don’t forget to consider your workforce. Are they aware of cybersecurity best practices? User training will play a huge role in implementing Zero Trust successfully. Phishing simulations, workshops, and awareness campaigns can help build a security-first mindset across your organization.
Mapping Zero Trust to Your Cybersecurity Framework
Integrating Zero Trust into your existing cybersecurity strategy isn’t as daunting as it might seem. A step-by-step approach will ensure minimal disruption to business operations. Start by mapping ZTA principles to your existing cybersecurity framework (e.g., NIST, ISO, or CIS). For instance, NIST’s cybersecurity framework offers clear guidelines that align well with Zero Trust concepts.
Once you’ve mapped out where Zero Trust fits into your framework, start small. Pilot programs are a great way to test how ZTA works in a real-world setting. This can involve deploying MFA for a small group of users or using microsegmentation in a specific department before scaling up.
Build a Zero Trust Cybersecurity Roadmap
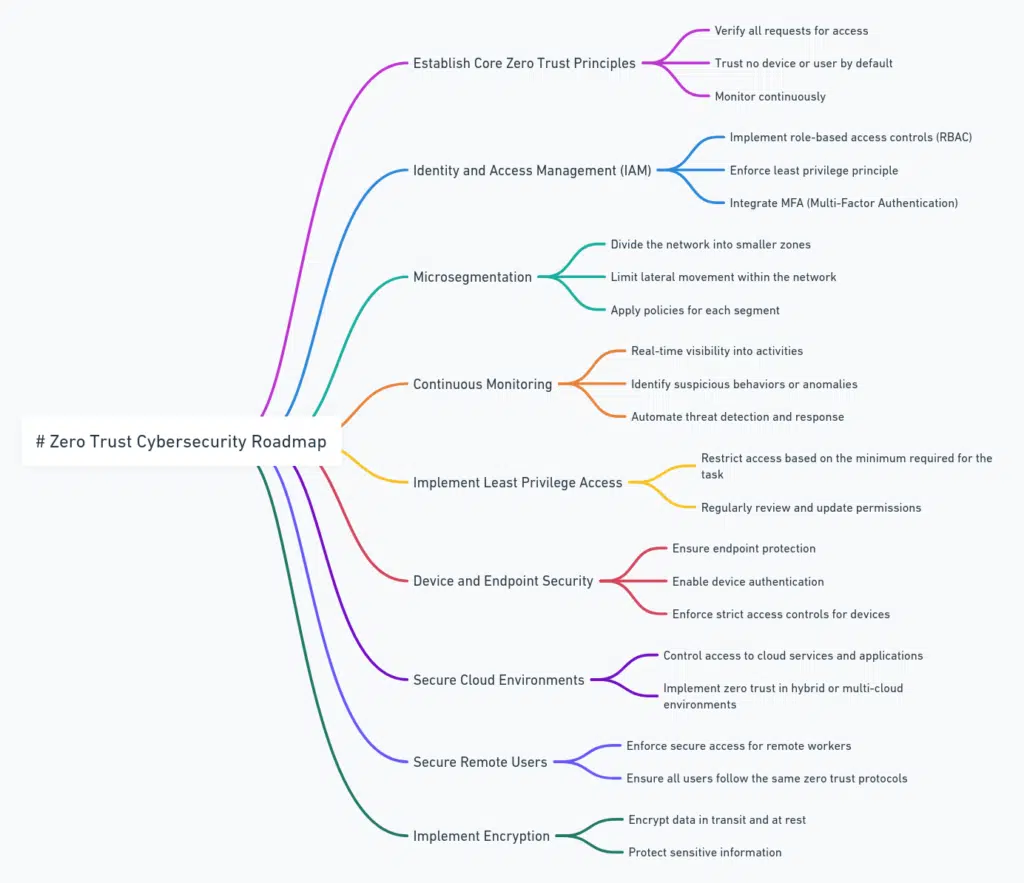
The Role of Identity and Access Management in Zero Trust
In the world of Zero Trust Architecture, Identity and Access Management (IAM) is one of the core pillars. Why? Because identity is now the new perimeter. With the rise of remote work, cloud adoption, and mobile devices, traditional network perimeters are no longer as relevant. Instead, IAM helps to ensure that the right people have the right access, at the right time, and under the right conditions.

IAM systems manage user identities and control access to resources by implementing role-based permissions. However, in a Zero Trust model, IAM goes beyond role-based access. It considers additional factors like device health, location, and the sensitivity of the resource being accessed. Integrating multi-factor authentication (MFA) and single sign-on (SSO) solutions enhances IAM further, ensuring robust protection.
As companies move toward Zero Trust, IAM becomes the front line of defense, making it crucial to streamline identity verification processes and restrict unnecessary access.
Building a Robust Authentication Strategy
A Zero Trust approach demands rigorous authentication methods. The first step is eliminating the assumption that anyone inside your network is automatically trustworthy. This is where multi-factor authentication (MFA) plays a starring role.
MFA requires users to provide multiple forms of verification, such as a password combined with a fingerprint or an OTP (one-time password). This extra step may seem inconvenient, but it’s a simple way to dramatically reduce unauthorized access. But MFA is just one piece of the puzzle.
For highly sensitive data, implementing adaptive authentication—a method that adjusts the level of authentication required based on factors like user location, behavior, and device type—can take security to the next level. Using biometric authentication like facial recognition and fingerprint scanning adds an extra layer of verification. The goal is to ensure that users are exactly who they claim to be, every single time.
Microsegmentation: Containing Threats Before They Spread
Microsegmentation is a technique that divides your network into isolated segments. Instead of a flat network where everyone can access everything, microsegmentation creates barriers between different areas of the network, restricting movement.
For instance, if a hacker compromises one part of the network, microsegmentation ensures they can’t easily move laterally to other systems. Think of it as building multiple firewalls within your infrastructure, so even if one wall is breached, the others remain intact.

By tightly controlling the flow of information and access between these segmented parts, Zero Trust Architecture limits the potential damage from an attack. Whether the breach happens via malware or a compromised insider, microsegmentation ensures that the damage is localized and easier to manage.
Many organizations start by segmenting high-value assets or sensitive systems and gradually apply microsegmentation across their entire network.
The Importance of Continuous Monitoring and Analytics
In a Zero Trust environment, simply implementing strong authentication and network segmentation isn’t enough. Continuous monitoring is critical to detect threats in real time. Instead of periodic checks or audits, Zero Trust relies on continuous, real-time data collection and analysis to keep the network secure.
Security teams need to keep a close eye on user behaviors, network traffic, and system interactions. Anomalies—like sudden attempts to access restricted data or unusual login times—can indicate a potential breach or malicious insider.
Implementing behavioral analytics tools allows organizations to spot suspicious patterns and react immediately. Machine learning-driven analytics can further enhance this process by identifying subtle signs of attack that traditional monitoring might miss. By constantly watching and analyzing the environment, Zero Trust ensures that security never takes a break.
Zero Trust in Cloud Security: Where Does it Fit?
As companies migrate to the cloud, securing cloud environments becomes one of the biggest concerns. Cloud infrastructures are inherently complex and often shared across multiple customers, making them attractive targets for attackers.
Zero Trust principles fit perfectly into cloud security. In a cloud environment, there is no clear network boundary, and the traditional “perimeter” is spread across multiple data centers and platforms. This makes the need for continuous verification and least privilege access more critical than ever.
To secure your cloud infrastructure, you need to ensure that users and applications accessing the cloud are continuously verified. Technologies like software-defined perimeters (SDP) can be used to create virtual boundaries around cloud resources, giving organizations more control over who gets in.
Additionally, using encryption for all data transfers and storage, along with ensuring strong access controls, helps align cloud security with Zero Trust standards. As more businesses turn to hybrid cloud environments, a Zero Trust approach offers the adaptability needed to protect data both on-premise and in the cloud.
Overcoming Challenges in Zero Trust Implementation
Implementing Zero Trust Architecture comes with its own set of challenges, and it’s important to be aware of them before diving in. One of the primary obstacles is the complexity of integrating Zero Trust into existing IT infrastructures, especially if they are outdated or rely heavily on legacy systems. These systems may not support the granular control and continuous verification required by Zero Trust, leading to potential disruptions during the transition.
Additionally, the initial cost and resource allocation for deploying Zero Trust solutions—such as multi-factor authentication (MFA), identity management systems, and network segmentation—can be significant. Organizations may also face pushback from employees who view the increased security measures as a hindrance to productivity.
However, these challenges can be mitigated with proper planning, communication, and a phased approach. Starting small with pilot programs can help ease the transition and allow time for adjustments. Investing in employee training is also key, as informed staff are less likely to resist new security protocols and more likely to follow best practices.
Zero Trust and Compliance: Aligning with Industry Standards
As organizations adopt Zero Trust, it’s essential to consider how it aligns with regulatory frameworks and compliance requirements. Many industries, such as healthcare and finance, are governed by strict data protection laws like HIPAA, GDPR, or PCI-DSS. Fortunately, Zero Trust principles can help meet and even exceed these compliance standards.
For example, least privilege access ensures that only authorized individuals can access sensitive data, a key requirement for many regulations. Continuous monitoring and logging, which are integral to Zero Trust, also support compliance by creating detailed records of all access attempts and network activities. These logs are invaluable during audits and can demonstrate that your organization has taken proactive steps to protect data.
Implementing Zero Trust not only improves your cybersecurity posture but also strengthens your compliance efforts. By focusing on stringent access controls and ongoing verification, organizations can reduce the risk of data breaches that result in regulatory fines or reputational damage.
Best Practices for a Smooth Zero Trust Transition
Transitioning to Zero Trust Architecture doesn’t have to be overwhelming. By following best practices, organizations can achieve a smoother and more successful adoption. First, it’s important to take a phased approach. Begin by identifying your most critical assets and applying Zero Trust principles there. This can involve restricting access to sensitive data and implementing multi-factor authentication (MFA) for high-risk accounts.
Next, ensure you have a strong identity and access management (IAM) system in place. Since identity is the cornerstone of Zero Trust, having a system that accurately manages users, roles, and permissions is essential. This can prevent unauthorized access while allowing legitimate users to do their work without unnecessary friction.
Finally, don’t forget about continuous monitoring. Security doesn’t stop at authentication—monitoring network activity and user behavior in real-time is vital to spotting potential breaches early. Automation tools can help streamline the process, ensuring that suspicious activities trigger immediate alerts and responses.
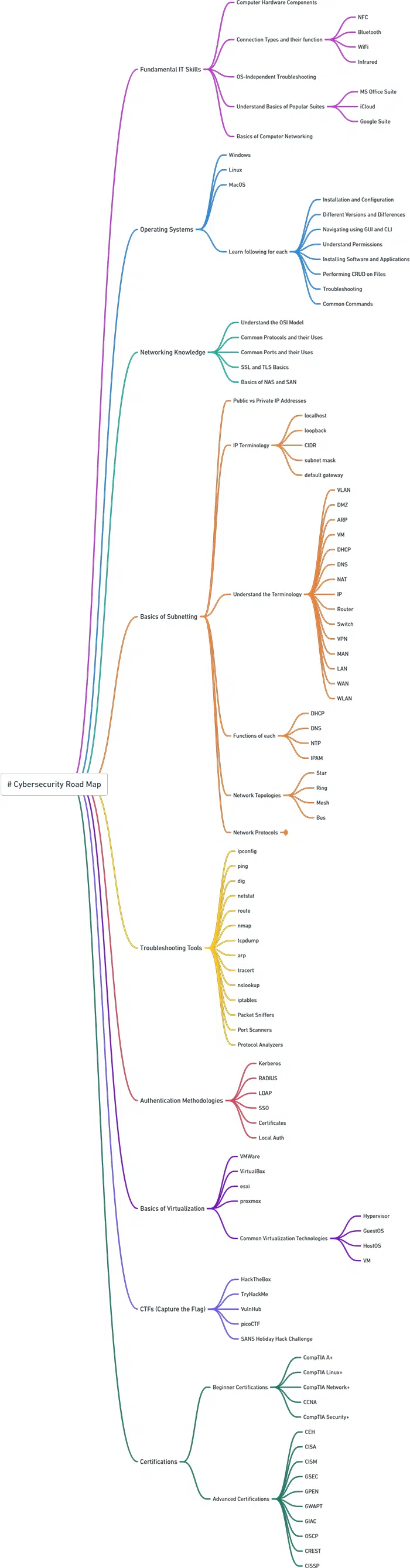
Cybersecurity Roadmap: Building Core Skills and Certifications for a Secure IT Career
Case Studies: How Organizations Have Successfully Integrated Zero Trust
Several companies have already embraced Zero Trust and reaped the rewards. Take Google, for example, which implemented its own Zero Trust framework, called BeyondCorp. In response to the rise of remote work and the need for secure, cloud-based applications, Google shifted away from traditional perimeter-based security and focused on verifying every request to its systems. The result? Improved security with seamless access for employees from anywhere in the world.
Another success story comes from Microsoft, which integrated Zero Trust principles across its services and products. By enforcing least privilege access, multi-factor authentication, and continuous monitoring, Microsoft improved its defense against increasingly sophisticated cyber threats. Other large enterprises, like Netflix and Cisco, have also adopted Zero Trust models to safeguard their global operations.
These case studies show that Zero Trust can be scaled to meet the needs of diverse industries and organizations, from tech giants to more traditional sectors like finance and healthcare.
How to Future-Proof Your Security with Zero Trust
The cybersecurity landscape is constantly evolving, and Zero Trust provides a future-proof solution for organizations looking to stay ahead of threats. By focusing on continuous validation and limiting access based on real-time conditions, Zero Trust enables companies to adapt to changing security challenges quickly and effectively.
One of the most significant advantages of Zero Trust is its scalability. As organizations grow, add new technologies, or migrate to the cloud, the Zero Trust model can easily be expanded to cover new assets and users without requiring a complete overhaul of the existing security infrastructure. The automation capabilities built into Zero Trust frameworks also allow for efficient scaling without adding overwhelming administrative overhead.
Looking ahead, advancements in artificial intelligence (AI) and machine learning will likely make Zero Trust even more effective. These technologies can help predict and prevent potential attacks by analyzing vast amounts of data and detecting unusual patterns that might indicate a threat.
Mistakes to Avoid in Zero Trust Adoption
While Zero Trust offers many benefits, there are some common mistakes that organizations should avoid when adopting this model. One of the biggest pitfalls is assuming that Zero Trust is a one-size-fits-all solution. Each organization is unique, and the implementation of Zero Trust should be tailored to fit specific needs, risk profiles, and industry requirements.
Another common mistake is neglecting employee training. No matter how advanced your security tools are, they won’t be effective if your team doesn’t know how to use them. Make sure to invest in ongoing training programs that teach employees about cybersecurity best practices and how to navigate the new systems.
Lastly, some organizations make the mistake of not monitoring their Zero Trust systems after implementation. Zero Trust is not a “set it and forget it” solution. Continuous monitoring and adjustments are necessary to keep up with the evolving threat landscape and ensure that the system continues to function as intended.
The Future of Zero Trust Architecture: Trends to Watch
As cybersecurity threats grow more sophisticated, Zero Trust Architecture (ZTA) is evolving to meet new challenges. In the future, we can expect AI and machine learning to play an increasingly significant role in automating security processes. By analyzing vast amounts of data, AI will be able to detect anomalies and potential threats more quickly than ever before, minimizing response times and helping to prevent breaches before they happen.
Another trend to watch is the rise of Zero Trust Network Access (ZTNA), which allows organizations to move away from VPNs and adopt more dynamic, secure access methods. As remote work and cloud computing become more prevalent, ZTNA will provide scalable, flexible access to sensitive resources from any location.
Additionally, the concept of passwordless authentication is gaining traction in the Zero Trust model. Traditional passwords are often weak links in security, prone to being forgotten or easily cracked. In the near future, biometric data, cryptographic keys, and behavioral analysis could replace passwords entirely, making access both more secure and more convenient.
As Zero Trust continues to mature, integration with IoT devices, edge computing, and 5G networks will be essential. These technologies expand the network perimeter even further, requiring advanced strategies for managing access and ensuring that every device, whether it’s a phone or a smart sensor, is verified and secured.
Lastly, expect government regulations to push the adoption of Zero Trust even further. With increasing focus on data protection and privacy laws, more industries will be required to adopt stronger cybersecurity measures, with Zero Trust leading the charge.
With these insights into the future of Zero Trust, organizations can better prepare themselves for the evolving threat landscape and adopt best practices that ensure security is always ahead of the curve.
FAQ: Integrating Zero Trust Architecture into Your Cybersecurity Roadmap
What is Zero Trust Architecture (ZTA)?
Zero Trust Architecture is a security model that assumes no user, device, or application should be trusted by default, whether inside or outside the network. It requires continuous verification and strict access controls to protect sensitive data and systems, effectively eliminating the traditional “trusted network” concept.
How does Zero Trust differ from traditional security models?
Traditional security models follow a perimeter-based approach where users and devices inside the network are trusted by default. Zero Trust flips this by treating all access attempts as untrusted until verified, focusing on continuous monitoring, least privilege access, and strong identity management to secure data at every layer.
Why should my organization adopt Zero Trust?
With the rise of cloud computing, remote work, and increasing cybersecurity threats, traditional perimeter-based security is no longer sufficient. Zero Trust provides stronger protection by limiting access to sensitive resources, requiring continuous validation, and reducing the attack surface in the event of a breach.
How do I know if my organization is ready for Zero Trust?
Evaluate your current security infrastructure, including identity and access management (IAM), legacy systems, and employee awareness of cybersecurity. If your organization has high-value assets or is frequently targeted by cyberattacks, Zero Trust may be critical. Conducting a security audit can help determine which areas need upgrading before implementing Zero Trust.
How can we start implementing Zero Trust?
Start by identifying the most sensitive data and assets in your organization and applying Zero Trust principles there. This might include rolling out multi-factor authentication (MFA), implementing microsegmentation, and conducting continuous monitoring of user behavior. Taking a phased approach—starting with small pilot programs—can make the transition smoother.
What are the key technologies involved in Zero Trust?
Key technologies in Zero Trust include:
- Identity and Access Management (IAM)
- Multi-factor authentication (MFA)
- Microsegmentation
- Continuous monitoring and analytics tools
- Software-Defined Perimeters (SDP) for cloud environments
- Behavioral analytics for detecting threats in real-time
Does Zero Trust require replacing all our current security tools?
No, Zero Trust can be integrated with many existing systems. However, legacy systems that don’t support granular control or continuous monitoring may need to be upgraded. The key is to align your current tools with Zero Trust principles, such as least privilege access and real-time monitoring.
How does Zero Trust affect cloud security?
Cloud environments have blurred the lines of traditional network perimeters. Zero Trust fits perfectly into cloud security by continuously verifying every access request, ensuring that only authorized users and devices can interact with cloud-based assets. It also adds additional layers of security with encryption, identity management, and microsegmentation.
What challenges can I expect when adopting Zero Trust?
Common challenges include:
- Legacy infrastructure that may not support Zero Trust technologies
- Cost and resources involved in deploying MFA, IAM, and segmentation tools
- Employee resistance due to the perceived inconvenience of stronger access controls
- The complexity of integrating Zero Trust into multi-cloud or hybrid environments
However, proper planning, phased implementation, and staff training can ease the transition.
Can Zero Trust help with compliance and regulatory requirements?
Yes, Zero Trust can align with many compliance frameworks such as HIPAA, GDPR, and PCI-DSS. Its focus on least privilege access, continuous monitoring, and detailed logging can help organizations meet regulatory requirements for data security and access control.
How does Zero Trust improve network security for remote work?
With the rise of remote work, users are accessing corporate resources from various locations and devices. Zero Trust ensures that every access request is verified, no matter where the user is located. It also uses tools like multi-factor authentication and continuous monitoring to prevent unauthorized access to critical systems.
What are some common mistakes to avoid when implementing Zero Trust?
Avoid these common mistakes:
- Assuming Zero Trust is a one-size-fits-all solution
- Neglecting employee training on new security processes
- Not monitoring the system after implementation—continuous adjustments are needed
- Failing to start with high-priority areas (e.g., critical assets) and attempting to apply Zero Trust across the entire network at once
What is the future of Zero Trust?
The future of Zero Trust involves deeper integration with technologies like artificial intelligence and machine learning to automate threat detection and improve security. It will also expand into cloud environments, IoT, and 5G networks as these technologies grow. Expect further development in passwordless authentication, Zero Trust Network Access (ZTNA), and more scalable security frameworks.
Can Zero Trust completely prevent cyberattacks?
While no security model can guarantee 100% protection, Zero Trust significantly reduces the attack surface and limits the damage that an attack can cause. By verifying every request, limiting access to critical resources, and monitoring continuously, Zero Trust makes it much harder for attackers to breach your systems or move laterally within your network.
Resources
1. National Institute of Standards and Technology (NIST) – Zero Trust Architecture Guidelines
NIST provides a comprehensive framework for understanding and implementing Zero Trust. Their Special Publication 800-207 offers detailed guidance on Zero Trust concepts, principles, and deployment strategies.
2. Cybersecurity & Infrastructure Security Agency (CISA) – Zero Trust Maturity Model
CISA’s Zero Trust Maturity Model is designed to guide organizations through the adoption of Zero Trust principles. It outlines a roadmap to implement Zero Trust in a scalable and structured way.
3. Google’s BeyondCorp – A Practical Zero Trust Model
Google pioneered BeyondCorp, one of the most well-known Zero Trust frameworks. Their site offers insights into how they built and implemented Zero Trust, along with strategies for organizations looking to follow a similar path.
4. Forrester Research – Zero Trust Extended Ecosystem
Forrester, the organization that coined the term “Zero Trust,” provides research, reports, and insights on the evolving Zero Trust Extended Ecosystem. They also offer guidance on vendors and technologies supporting Zero Trust.
5. Microsoft’s Zero Trust Deployment Framework
Microsoft offers a Zero Trust deployment framework tailored to cloud environments, remote work, and hybrid infrastructures. This guide provides technical insights, real-world examples, and steps for achieving Zero Trust in Microsoft environments.
6. Cisco Secure – Zero Trust Solutions
Cisco provides detailed resources, whitepapers, and case studies on how their security solutions align with Zero Trust principles, particularly focusing on network segmentation, endpoint security, and Zero Trust Network Access (ZTNA).
7. Palo Alto Networks – Zero Trust for Cloud and Hybrid Environments
Palo Alto Networks offers a robust set of Zero Trust resources, particularly focused on cloud security, network protection, and securing remote workforces. Their content includes webinars, whitepapers, and step-by-step implementation guides.
8. Gartner – Zero Trust Networking Research
Gartner provides insightful research on Zero Trust, covering network segmentation, identity management, and the importance of ZTNA. Their reports are often available to clients or via one-time purchases.
9. Okta – Identity-Driven Security with Zero Trust
Okta is a leading provider of identity and access management (IAM) solutions and their Zero Trust resources focus on securing user identities, ensuring least privilege access, and the importance of adaptive MFA.